A cybercrime company acknowledged as Lemon Team is leveraging hundreds of thousands of pre-infected Android smartphones around the globe to have out their destructive functions, posing major offer chain threats.
“The an infection turns these units into cellular proxies, tools for thieving and providing SMS messages, social media and on line messaging accounts and monetization through advertisements and click on fraud,” cybersecurity organization Craze Micro mentioned.
The action encompasses no fewer than 8.9 million compromised Android devices, especially finances telephones, with a greater part of the infections found in the U.S., Mexico, Indonesia, Thailand, Russia, South Africa, India, Angola, the Philippines, and Argentina.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The findings ended up offered by scientists Fyodor Yarochkin, Zhengyu Dong, Vladimir Kropotov, and Paul Pajares at the Black Hat Asia convention held in Singapore very last 7 days.
Describing it as a constantly evolving dilemma, the cybersecurity agency stated the threat actors are branching out to other Android-centered IoT equipment these kinds of as Clever TVs, Android Television bins, amusement techniques, and even kid’s watches.
The infections are globally distribute throughout in above 180 nations around the world, with in excess of 50 brand names of cell equipment compromised by a malware pressure identified as Guerilla.
“Pursuing our timeline estimates, the threat actor has spread this malware about the very last five a long time,” the scientists said. “A compromise on any important critical infrastructure with this infection can probably yield a major income for Lemon Group in the extended run at the expense of genuine consumers.”
Guerilla was very first documented by Sophos in 2018 when it discovered 15 applications uploaded on the Play Keep that harbored functionality to interact in simply click fraud and act as a backdoor.
The malware also captivated interest in early 2022 for its skill to intercept SMS messages that match predefined attributes this sort of as one particular-time passwords (OTPs) affiliated with numerous on-line platforms, shortly right after which the risk actor transformed the identify of the enterprise from Lemon to Durian Cloud SMS.
The aim, for every Craze Micro, is to bypass SMS-based verification and publicize bulk digital phone figures – which belong to unsuspecting end users of the infected Android handsets – for sale to develop on the net accounts.
Whilst these kinds of services have a privacy gain, letting consumers to indication up for companies making use of non permanent or disposable phone numbers, they can also be abused to create spam accounts on a significant scale and carry out fraud.
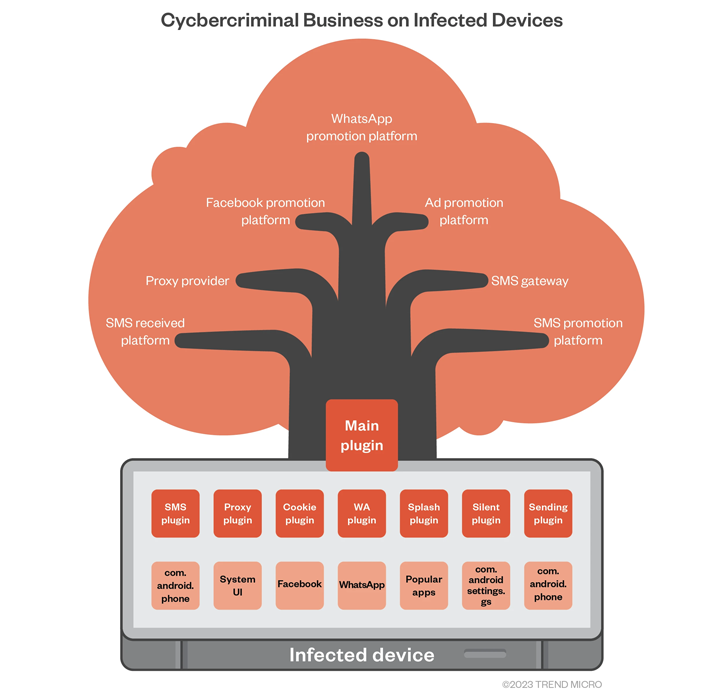
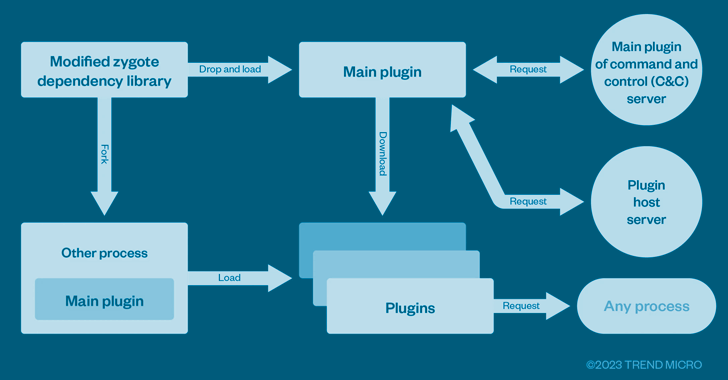
The most current results from the cybersecurity firm illustrate that the SMS grabbing function is just 1 of the quite a few plugins involved with a downloader element (aka the most important plugin) which is loaded into a zygote procedure by usually means of a tampered library.
It’s value noting that the same technique of modifying the zygote system has also been adopted by an additional cellular trojan named Triada.
“With this, every time other application procedures are forked from the zygote, it would also be tampered,” the researchers claimed. “The most important plugin will load other plugins with the recent process getting the focus on, and the other plugins will test to manage the current app via a hook.”
Every single of the Guerilla plugins serves a unique business enterprise perform and a monetization opportunity for the Lemon Team actors. Some of them are detailed underneath –
- Proxy plugin to setup reverse proxy from an contaminated phone and permit other actors to hire out access to the network assets of the impacted cellular system
- Cookie plugin to harvest users’ Facebook cookies and other profile facts
- WhatsApp plugin to hijack sessions and ship undesired messages
- Splash plugin to serve unwarranted ads when launching selected apps, and
- Silent plugin to stealthily install an APK file and launch the application
Even more investigation into the sprawling procedure has unraveled infrastructure overlaps Lemon Team and Triada, suggesting that the two teams may well have collaborated at some level.
Impending WEBINARZero Have faith in + Deception: Find out How to Outsmart Attackers!
Uncover how Deception can detect superior threats, quit lateral motion, and boost your Zero Have faith in technique. Be part of our insightful webinar!
Help you save My Seat!
The unauthorized firmware modifications are believed to have happened through an unnamed third-party seller that “makes the firmware elements for cell telephones” and which also manufactures very similar elements for Android Automobile.
The disclosure arrives as Microsoft security researcher Dimitrios Valsamaras detailed a new attack technique dubbed Soiled Stream that turns Android share targets into a vector for distributing malicious payloads and capturing delicate details from other applications installed on a unit.
“The thought is similar to a file add vulnerability of a web software,” Valsamaras mentioned. “Additional specially, a malicious application works by using a specifically crafted material provider to bear a payload that it sends to the focus on application.”
“As the sender controls the content but also the name of the stream, the receiver may well overwrite critical files with malicious content in case it does not carry out some important security checks. Moreover, when certain circumstances apply, the receiver might also be compelled to duplicate secured data files to a community listing, setting the user’s private information at risk.”
Found this article fascinating? Adhere to us on Twitter and LinkedIn to browse more exclusive information we submit.
Some elements of this article are sourced from:
thehackernews.com

 Apple’s App Store Blocks $2b in Fraudulent Transactions
Apple’s App Store Blocks $2b in Fraudulent Transactions