Wing Security lately introduced that fundamental 3rd-party risk assessment is now offered as a no cost product or service. But it raises the queries of how SaaS is connected to third-party risk administration (TPRM) and what companies need to do to guarantee a good SaaS-TPRM process is in area. In this posting we will share 5 guidelines to handle the third-party dangers linked with SaaS, but 1st…
What exactly is Third-Party Risk Management in SaaS?
SaaS is fast developing, presenting organizations advantage, swift implementations, and valuable options. Even so, this advancement introduces a security problem where hazards come up from the interconnected character of SaaS source chains. It is crystal clear that before onboarding a new contractor or vendor, we need to have because of diligence, security checks, and referrals. Having said that, we now comprehend that in the SaaS domain, apps are, in point, the go-to seller of selection.
Let us make clear: Any worker can quite effortlessly connect SaaS vendors to enterprise details, granting them permissions and entry. This easy onboarding is essential for efficiency, scalability, and getting operate completed. But it also introduces plenty of security issues for the reason that most SaaS applications, unlike conventional suppliers, frequently bypass or skip security or IT acceptance.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
3rd-party SaaS security solutions participate in a pivotal purpose in safeguarding an organization’s SaaS supply chain, and assessing SaaS distributors results in being a very important ingredient of in depth seller risk management. Whilst some of the accountability for security falls on the SaaS seller, corporations should remain vigilant in controlling third-party challenges, irrespective of their measurement, to uphold a secure and sturdy business enterprise atmosphere and to be certain they comply with field standards.
In very simple conditions, Third-Party Risk Administration in the context of SaaS is the approach of evaluating and controlling the opportunity dangers posed by 3rd-party suppliers and assistance companies in the SaaS domain. TPRM aids security and IT teams establish and comprehend different types of challenges coming via third-party expert services that relate to cybersecurity, which include information privacy vulnerabilities, compliance gaps, operational issues, financial issues, and reputational problems.
5 TPRM recommendations to be certain SaaS Security
1. Identification and Categorization:
Pinpointing and categorizing third-party connections is a critical stage for businesses to understand the prospective threats these connections pose to security and compliance. A absence of systematic facts selection and analysis on entry degrees and seller security can leave security and IT groups in the dark, hindering their capability to assess and securely use unique third-party apps properly.
On the other hand, with SaaS Security Posture Administration (SSPM) technology, corporations can triumph over this obstacle by easily getting all their third-party SaaS programs. SSPM answers provide contextual info on the degree of accessibility these apps have to organizational property and particulars about the vendor’s security degree centered on constant assessment.
 Wing Security’s TPRM option for SaaS applications
Wing Security’s TPRM option for SaaS applications
2. Owing Diligence and Evaluation:
Conducting because of diligence just before onboarding purposes is an vital action in guaranteeing that risky purposes are not getting released into an organization’s SaaS Stack. This maximizes the need to have to assess 3rd-party security controls, procedures, and techniques, making certain they fulfill the essential standards in advance of onboarding them.
To tackle this problem, companies need to glance for a answer that can present the necessary security and compliance details about related SaaS suppliers/apps. Information and facts these types of as security compliances, privacy compliances, vendor dimensions, area, historic menace intelligence alerts relating to breaches or security incidents that the vendor had expert, and so on. This information and facts is a major element of the owing diligence process of 3rd-party vendors.
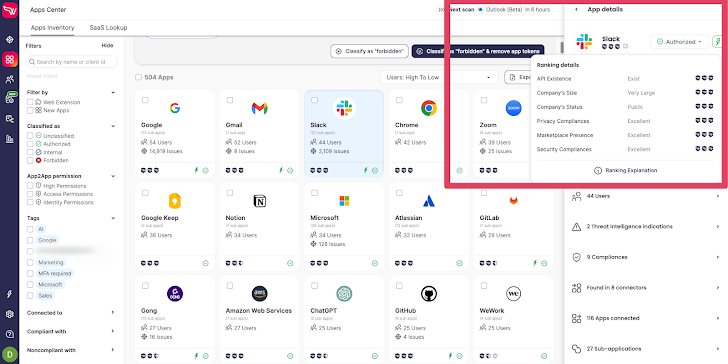 Wing Security’s free discovery remedy for SaaS purposes
Wing Security’s free discovery remedy for SaaS purposes
3. Ongoing Monitoring:
Ongoing checking is a important element of powerful TPRM. 3rd-party risk Administration does not prevent only at the phase of avoidance but also stresses the worth of regularly assessing 3rd-party functionality and security practices to ensure ongoing compliance and security with established standards. This proactive method will help corporations remain ahead of evolving risks.
An successful way to offer with this is to have a security resolution that is in a position to constantly check for updates in the vendors’ information and facts which includes adjustments in security and privacy compliances, threat intelligence alerts, and its risk posture.
4. Incident Response:
In the celebration of a security incident that pertains to a 3rd-party relationship, corporations need to be certain that a robust incident response plan is in spot. It starts by having the potential to obtain timely menace intelligence alerts when breaches or security incidents manifest, enabling them to respond promptly and properly.
5. Documentation and Reporting:
Maintaining in-depth information of the TPRM course of action is critical for demonstrating compliance with security expectations. Generating comprehensive reviews is significant due to the fact it provides transparency and facilitates smooth audits of the organization’s risk administration attempts.
Businesses need to opt for a alternative that can take care of the inventory of the complete organizational SaaS purposes to day, see all the relevant information and facts that supports the TRPM system, and export the suitable studies for audit reasons.
Implications of insufficient TPRM techniques:
Failing to apply correct 3rd-Party Risk Management practices can have serious penalties for corporations. Cybersecurity breaches ensuing from vulnerabilities released by third-party vendors can direct to the publicity of sensitive facts, economic theft, and reputational problems. Non-compliance with information privacy restrictions can attract hefty fines and lawful liabilities.
What is to achieve from TPRM?
Productive TPRM tactics present several gains. It empowers security groups to determine and handle possible threats, main to enhanced security and compliance. Strengthened seller relationships boost rely on and collaboration, though the skill to display good due diligence aids navigate regulatory specifications far more proficiently.
Finally, Third-Party Risk Management is a very important procedure that consists of figuring out and mitigating potential vulnerabilities introduced by third-party suppliers. TPRM plays a essential job in strengthening an organization’s total security posture by making sure adherence to regulatory compliance and finest security techniques all over the complete SaaS offer chain.
This proactive strategy is essential for securing businesses from SaaS threats, as it consists of evaluating the cybersecurity techniques of 3rd-party vendors to establish probable vulnerabilities and challenges in the provide chain. These assessments aid knowledgeable final decision-generating and risk mitigation and make sure alignment with the organization’s security benchmarks, ultimately fortifying the all round security defenses.
That mentioned, right now, seller risk assessments are critical but not enough. It truly is crucial to have both the abilities to assess and mitigate risk. By beginning with thorough 3rd-party risk assessments, corporations can attain the needed insights to choose the subsequent methods in proactively addressing dangers and making certain a secure and perfectly-secured SaaS source chain.
Identified this write-up intriguing? Observe us on Twitter and LinkedIn to go through more distinctive written content we put up.
Some pieces of this short article are sourced from:
thehackernews.com


 7 Uses for Generative AI to Enhance Security Operations
7 Uses for Generative AI to Enhance Security Operations