Risk actors are applying Android Deal (APK) information with unidentified or unsupported compression approaches to elude malware assessment.
That’s according to results from Zimperium, which identified 3,300 artifacts leveraging these types of compression algorithms in the wild. 71 of the discovered samples can be loaded on the operating process without having any troubles.
There is no proof that the apps were available on the Google Play Store at any point in time, indicating that the applications ended up distributed via other usually means, generally via untrusted application shops or social engineering to trick the victims into sideloading them.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

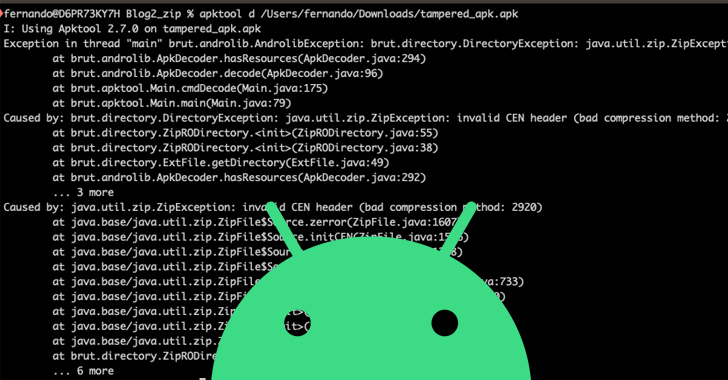
The APK data files use “a approach that boundaries the risk of decompiling the software for a massive amount of applications, reducing the prospects of getting analyzed,” security researcher Fernando Ortega said. “In get to do that, the APK (which is in essence a ZIP file), is making use of an unsupported decompression system.”
The gain of these kinds of an method is its potential to resist decompilation applications, though even now getting able to be mounted on Android gadgets whose running technique version is earlier mentioned Android 9 Pie.
The Texas-based mostly cybersecurity business claimed it began its very own analysis soon after a write-up from Joe Security on X (formerly Twitter) in June 2023 about an APK file that exhibited this conduct.

Android deals use the ZIP structure in two modes, one without compression and a person employing the DEFLATE algorithm. The crucial acquiring here is that APKs packed applying unsupported compression procedures are not installable on handsets operating Android versions underneath 9, but they work appropriately on subsequent variations.
In addition, Zimperium identified that malware authors are also intentionally corrupting the APK documents by obtaining filenames with much more than 256 bytes and malformed AndroidManifest.xml documents to result in crashes on analysis resources.
The disclosure comes months following Google unveiled that danger actors are leveraging a method called versioning to evade its Participate in Store’s malware detections and focus on Android people.
Found this write-up intriguing? Observe us on Twitter and LinkedIn to read through much more special content we put up.
Some components of this short article are sourced from:
thehackernews.com

 14 Suspected Cybercriminals Arrested Across Africa in Coordinated Crackdown
14 Suspected Cybercriminals Arrested Across Africa in Coordinated Crackdown