Risk actors are exploiting improperly secured Microsoft SQL (MS SQL) servers to produce Cobalt Strike and a ransomware pressure termed FreeWorld.
Cybersecurity business Securonix, which has dubbed the campaign DB#JAMMER, explained it stands out for the way the toolset and infrastructure is utilized.
“Some of these resources contain enumeration software, RAT payloads, exploitation and credential thieving software, and ultimately ransomware payloads,” security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov mentioned in a specialized breakdown of the activity.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The ransomware payload of decision appears to be a more recent variant of Mimic ransomware named FreeWorld.”
Initial accessibility to the sufferer host is realized by brute-forcing the MS SQL server, employing it to enumerate the databases and leveraging the xp_cmdshell configuration choice to run shell commands and perform reconnaissance.

The up coming stage entails having measures to impair method firewall and build persistence by connecting to a distant SMB share to transfer information to and from the sufferer procedure as perfectly as put in malicious applications this sort of as Cobalt Strike.
This, in transform, paves the way for the distribution of AnyDesk program to ultimately thrust FreeWorld ransomware, but not right before carrying out a lateral movement move. The unknown attackers are also claimed to have unsuccessfully attempted to establish RDP persistence as a result of Ngrok.
“The attack initially succeeded as a end result of a brute pressure attack versus a MS SQL server,” the scientists mentioned. “It is crucial to emphasize the worth of powerful passwords, particularly on publicly uncovered expert services.”
The disclosure will come as the operators of the Rhysida ransomware have claimed 41 victims, with additional than fifty percent of them situated in Europe.
Rhysida is a single of the nascent ransomware strains that emerged in May well 2023, adopting the more and more well known tactic of encrypting and exfiltrating delicate data from companies and threatening to leak the info if the victims refuse to pay.
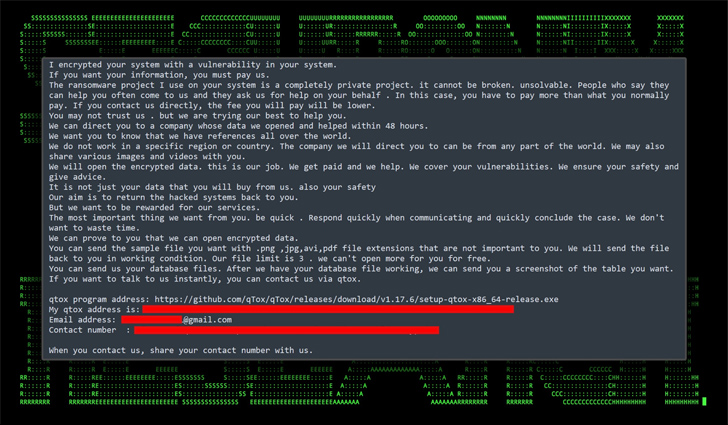
It also follows the launch of a cost-free decryptor for a ransomware termed Essential Team owing to various cryptographic mistakes in the software. The Python script, however, only functions on samples compiled right after August 3, 2023.
“Crucial Team ransomware works by using a base64 encoded static crucial N0dQM0I1JCM= to encrypt victims’ knowledge,” Dutch cybersecurity corporation EclecticIQ stated in a report produced Thursday.
“The menace actor attempted to boost the randomness of the encrypted knowledge by using a cryptographic strategy termed salting. The salt was static and employed for every single encryption process which poses a significant flaw in the encryption schedule.”
Future WEBINARDetect, Respond, Shield: ITDR and SSPM for Entire SaaS Security
Learn how Identification Risk Detection & Response (ITDR) identifies and mitigates threats with the help of SSPM. Study how to safe your company SaaS programs and defend your knowledge, even after a breach.
Supercharge Your Competencies
2023 has witnessed a report surge in ransomware attacks pursuing a lull in 2022, even as the percentage of incidents that resulted in the victim paying have fallen to a history very low of 34%, according to studies shared by Coveware in July 2023.
The ordinary ransom sum paid out, on the other hand, has strike $740,144, up 126% from Q1 2023.
The fluctuations in monetization prices have been accompanied by ransomware risk actors continuing to evolve their extortion tradecraft, which include sharing aspects of its attack strategies to show why its victims usually are not eligible for a cyber insurance policies payout.
“Snatch claims they will release information of how attacks versus non-paying victims succeeded in the hope that insurers will make your mind up that the incidents really should not be lined by insurance plan ransomware,” Emsisoft security researcher Brett Callow claimed in a post shared on X (previously Twitter) very last month.
Discovered this write-up intriguing? Follow us on Twitter and LinkedIn to read through far more exceptional content material we article.
Some elements of this write-up are sourced from:
thehackernews.com

 Russian State-Backed ‘Infamous Chisel’ Android Malware Targets Ukrainian Military
Russian State-Backed ‘Infamous Chisel’ Android Malware Targets Ukrainian Military