A cyberespionage actor acknowledged as Tick has been attributed with significant self esteem to a compromise of an East Asian details-decline prevention (DLP) organization that caters to govt and army entities.
“The attackers compromised the DLP company’s interior update servers to provide malware within the software developer’s network, and trojanized installers of genuine instruments used by the corporation, which at some point resulted in the execution of malware on the desktops of the firm’s buyers,” ESET researcher Facundo Muñoz said.
Tick, also recognised as Bronze Butler, Stalker Panda, REDBALDKNIGHT, and Stalker Taurus, is a suspected China-aligned collective that has generally absent following authorities, manufacturing, and biotechnology companies in Japan. It is really reported to be active considering that at the very least 2006.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Other lesser-known targets involve Russian, Singaporean, and Chinese enterprises. Attack chains orchestrated by the group have ordinarily leveraged spear-phishing emails and strategic web compromises as an entry place.
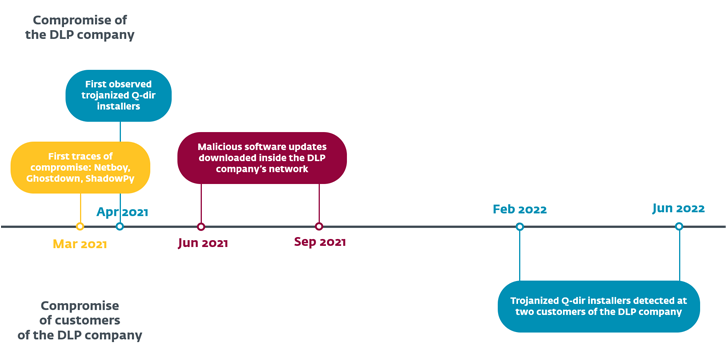
In late February 2021, Tick emerged as one particular of the danger actors to capitalize on the ProxyLogon flaws in Microsoft Trade Server as a zero-working day to fall a Delphi-primarily based backdoor in a web server belonging to a South Korean IT corporation.
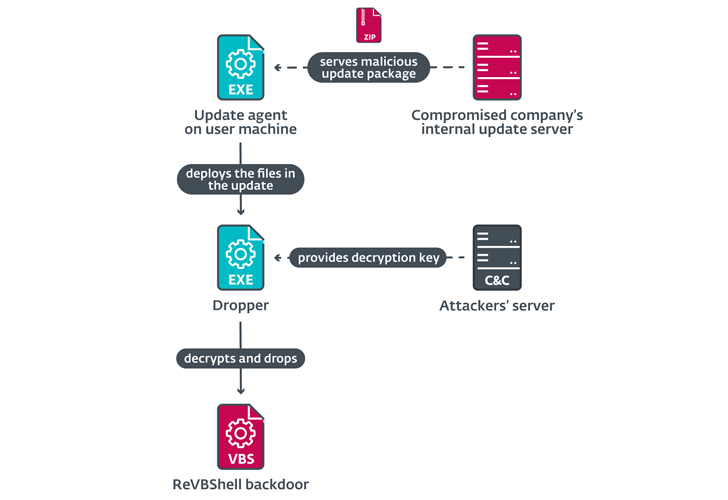
All around the same time, the adversarial collective is considered to have received access to the network of an East Asian program developer organization through mysterious means. The title of the business was not disclosed.
This was followed by the deployment of a tampered variation of a reputable software called Q-Dir to fall an open up source VBScript backdoor named ReVBShell, in addition to a previously undocumented downloader named ShadowPy.
ShadowPy, as the title signifies, is a Python downloader that is liable for executing a Python script retrieved from a distant server.
Also sent during the intrusion had been variants of a Delphi backdoor termed Netboy (aka Invader or Kickesgo) that arrives with facts gathering and reverse shell capabilities as very well as one more downloader codenamed Ghostdown.
WEBINARDiscover the Concealed Dangers of Third-Party SaaS Apps
Are you informed of the dangers involved with third-party application access to your company’s SaaS apps? Be a part of our webinar to study about the sorts of permissions being granted and how to lower risk.
RESERVE YOUR SEAT
“To manage persistent obtain, the attackers deployed destructive loader DLLs along with legitimate signed apps vulnerable to DLL lookup-order hijacking,” Muñoz stated. “The reason of these DLLs is to decode and inject a payload into a selected procedure.”
Subsequently, in February and June 2022, the trojanized Q-Dir installers had been transferred by way of remote assistance equipment like helpU and ANYSUPPORT to two of the company’s customers, an engineering and a production company positioned in East Asia.
The Slovak cybersecurity firm reported the target here was not to execute a provide chain attack against its downstream clients, but fairly that the rogue installer was “unknowingly” used as section of complex guidance actions.
The incident is also probably similar to yet another unattributed cluster in-depth by AhnLab in May 2022 that included the use of Microsoft Compiled HTML Support (.CHM) documents to fall the ReVBShell implant.
Located this short article intriguing? Comply with us on Twitter and LinkedIn to read far more special information we publish.
Some pieces of this post are sourced from:
thehackernews.com

 IDCARE: Meet the cyber security charity shaping Australia and New Zealand’s data breach response
IDCARE: Meet the cyber security charity shaping Australia and New Zealand’s data breach response