A new Golang-dependent information stealer malware dubbed Titan Stealer is remaining marketed by menace actors via their Telegram channel.
“The stealer is capable of stealing a wide variety of info from contaminated Windows devices, together with credential details from browsers and crypto wallets, FTP shopper aspects, screenshots, method details, and grabbed information,” Uptycs security researchers Karthickkumar Kathiresan and Shilpesh Trivedi stated in a the latest report.
Aspects of the malware had been very first documented by cybersecurity researcher Will Thomas (@BushidoToken) in November 2022 by querying the IoT lookup motor Shodan.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
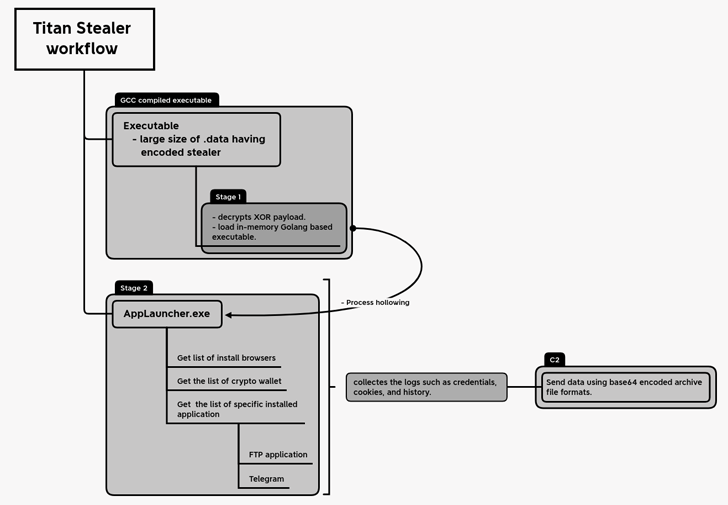
Titan is supplied as a builder, enabling prospects to customize the malware binary to consist of precise functionalities and the kind of information and facts to be exfiltrated from a victim’s device.
The malware, on execution, employs a strategy recognised as process hollowing to inject the destructive payload into the memory of a legitimate process acknowledged as AppLaunch.exe, which is the Microsoft .NET ClickOnce Launch Utility.
Some of the key web browsers specific by Titan Stealer include things like Google Chrome, Mozilla Firefox, Microsoft Edge, Yandex, Opera, Brave, Vivaldi, 7 Star Browser, Iridium Browser, and many others. The crypto wallets singled out are Armory, Armory, Bytecoin, Coinomi, Edge Wallet, Ethereum, Exodus, Guarda, Jaxx Liberty, and Zcash.
It truly is also able of accumulating the list of installed applications on the compromised host and capturing data linked with the Telegram desktop application.
The amassed info is subsequently transmitted to a remote server beneath the attacker’s handle as a Foundation64-encoded archive file. Also, the malware arrives with a web panel that enables adversaries to accessibility the stolen facts.
The actual modus operandi made use of to distribute the malware is unclear as still, but ordinarily danger actors have leveraged a selection of techniques, these types of as phishing, destructive adverts, and cracked program.
“A single of the principal reasons [threat actors] may possibly be applying Golang for their information and facts stealer malware is since it lets them to effortlessly produce cross-platform malware that can run on several functioning techniques, such as Windows, Linux, and macOS,” Cyble stated in its individual evaluation of Titan Stealer.
“Also, the Go compiled binary documents are tiny in dimension, producing them much more difficult to detect by security software package.”
The growth arrives a minor about two months soon after SEKOIA comprehensive another Go-primarily based malware referred to as Aurora Stealer that is staying set to use by several prison actors in their strategies.
The malware is normally propagated by way of lookalike sites of well known software, with the very same domains actively current to host trojanized variations of unique applications.
It has also been noticed using advantage of a technique acknowledged as padding to artificially inflate the measurement of the executables to as a lot as 260MB by introducing random data so as to evade detection by antivirus application.
The results arrive close on the heels of a malware campaign that has been noticed offering Raccoon and Vidar working with hundreds of fake sites masquerading as legitimate program and online games.
Team Cymru, in an analysis posted before this thirty day period, noted that “Vidar operators have split their infrastructure into two elements a person committed to their normal clients and the other for the management team, and also perhaps premium / important consumers.”
Identified this posting fascinating? Comply with us on Twitter and LinkedIn to go through a lot more unique written content we article.
Some components of this posting are sourced from:
thehackernews.com

 Fake Money Apps Garner Millions of Android Downloads
Fake Money Apps Garner Millions of Android Downloads