With 2022 coming to a near, there is no superior time to buckle down and prepare to experience the security difficulties in the calendar year to occur. This earlier year has seen its truthful share of breaches, attacks, and leaks, forcing companies to scramble to guard their SaaS stacks. March on your own observed a few various breaches from Microsoft, Hubspot, and Okta.
With SaaS sprawl ever expanding and getting to be far more complex, corporations can search to four locations inside their SaaS ecosystem to harden and safe.
Discover how you can automate your SaaS stack security

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Misconfigurations Abound
Enterprises can have around 40 million knobs, check out boxes, and toggles in their employees’ SaaS apps. The security team is accountable to secure each of these settings, user roles and permissions to assure they comply with sector and organization policy.
Not only due to the fact of their apparent risk or misalignment with security policies, misconfigurations are overwhelmingly challenging to safe manually. These configurations can change with every update, and their complexity is compounded by the quite a few compliance market specifications. Including to that problem, SaaS application entrepreneurs are likely to sit in organization departments outside the house the security team’s scope and are not properly trained or targeted on the app’s security.
Security groups should onboard a SaaS Security Posture Management (SSPM) remedy, like Adaptive Shield, that delivers full visibility and control across a critical mass of SaaS apps in the SaaS stack. The remedy have to establish both international application configurations and platform-unique configurations inside of every application. Security groups should really be equipped to use the answer to gain context into security alerts and gain answers to queries like: Which buyers are topic to a specific misconfiguration? Are they admins? Is their MFA enabled? By owning these answers at their fingertips, security teams can implement corporation and sector guidelines to remediate potential risks from any misconfiguration.
SaaS-to-SaaS Entry
A further escalating security problem derives from the rising quantity of applications linked to the firm’s SaaS atmosphere. On regular, 1000’s of applications are linked with no the acceptance or awareness of the security crew. Workers hook up these apps, often to raise productiveness, permit remote operate and to improved create and scale firm’s perform procedures.
However, when connecting applications to their workspaces, employees are prompted to grant permissions for the app to entry. These permissions incorporate the capacity to go through, create, update, and delete company or private data, not to mention that the app itself could be destructive. By clicking “accept,” the permissions they grant can empower threat actors to gain obtain to beneficial organization data. Users are frequently unaware of the significance of the permissions they have granted to these 3rd-party apps.
Slipping in the Shadow IT domain, security groups need to be equipped to discover 3rd party apps and discover which pose a risk. From obtain scopes requested by these apps, to approved users and cross referencing, the security crew must be in a position to measure the level of accessibility to sensitive facts across the organization’s stack. An SSPM resolution like Adaptive Protect, can arm the security staff with this kind of discovery and management in addition to supplying sophisticated reporting abilities for helpful and exact risk assessments to drive actionable measures.
Get a demo of how an SSPM option can assist mitigate 3rd-party application entry.
Machine-to-SaaS Consumer Risk
Security teams should offer with threats from end users accessing their SaaS apps from personalized, unsecured units. Accessing a SaaS app via an unmanaged unit poses a superior stage of risk for an firm, specially when the gadget operator is a very privileged person. Individual products are inclined to data theft and can inadvertently pass on malware into the organization’s natural environment. Shed or stolen products can also offer a gateway for criminals to entry the network.
Security teams need to have a answer that allows them to deal with SaaS hazards originating from compromised gadgets. An SSPM remedy like Adaptive Protect can determine privileged customers these types of as admins and executives, calculate consumer-risk concentrations, and understand which endpoint gadgets will need to be extra secured.
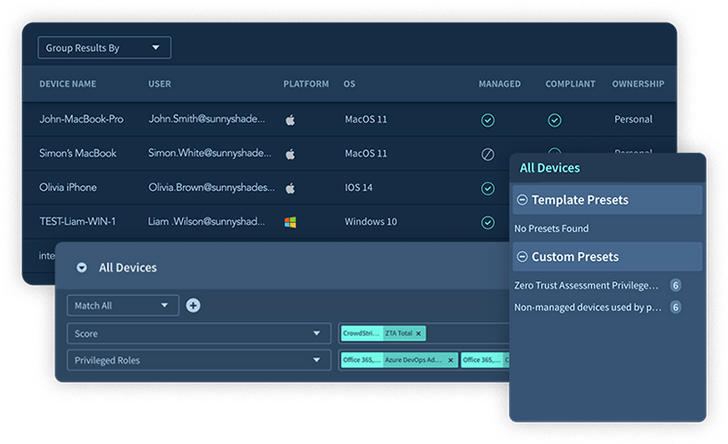 Figure 1. Adaptive Shield’s Product Stock
Figure 1. Adaptive Shield’s Product Stock
Identification and Accessibility Governance
Each SaaS application user is a probable gateway for a danger actor, as seen in the most latest Uber MFA Tiredness attack. Procedures to make sure suitable users’ access management and authentication configurations are essential, in addition to validation of function-dependent accessibility administration (as opposed to personal-primarily based accessibility) and establishing an being familiar with of entry governance. Id and accessibility governance allows make certain that security teams have full visibility and handle of what is occurring throughout all domains.
Security groups need to have to check all identities to ensure that user action satisfies their organization’s security tips. IAM Governance enables the security team to act on arising issues by providing frequent monitoring of the company’s SaaS Security posture as very well as its implementation of obtain command.
Final Feelings
Gartner known as SaaS Security Posture Administration (SSPM) in the “4 Have to-Have Systems That Manufactured the Gartner Hoopla Cycle for Cloud Security, 2021” for methods that continuously assess security risk and regulate the SaaS applications’ security posture. With an SSPM system, like Adaptive Defend, companies can harden their SaaS security to establish and remediate issues more rapidly and avert potential attacks. Security teams can introduce most effective tactics for SaaS security that prolong beyond Misconfiguration Administration to address SaaS-to-SaaS Obtain, System-to-SaaS Person Risk concentrations, and Id & Accessibility Administration Governance.
Uncovered this report exciting? Comply with us on Twitter and LinkedIn to browse additional special content material we submit.
Some parts of this report are sourced from:
thehackernews.com


 Google Adds Passkey Support to Chrome for Windows, macOS and Android
Google Adds Passkey Support to Chrome for Windows, macOS and Android