Every single New Calendar year introduces a new established of issues and opportunities for strengthening our cybersecurity posture. It really is the character of the subject – the velocity at which malicious actors have out state-of-the-art persistent threats provides a regular, evolving fight for cyber resilience. The excitement in cybersecurity lies in this steady adaptation and discovering, generally staying just one move in advance of possible threats.
As practitioners in an industry that operates around-the-clock, this hypervigilance turns into next character. We are generally in a continual point out of readiness, anticipating the following shift, adapting techniques, and counteracting threats. However, it stays just as crucial to have our fingers on the pulse of the most frequent vulnerabilities impacting security postures correct now. Why? Realizing these weak factors is not just about protection it truly is about ensuring robust, uninterrupted small business continuity in an natural environment where by challenges are generally all-around the corner.
The Great importance of Routinely Assessing Your Security Posture
The journey to establish a cyber resilient security posture begins with pinpointing present vulnerabilities nonetheless, when questioned about their vulnerability visibility, a lot less than 50 percent of cybersecurity experts claim to have higher (35%) or entire visibility (11%). At most effective, far more than 50 percent of corporations (51%) have only average visibility into their vulnerabilities.[1]
Normal assessments are one of the primary methods you can appraise your organization’s security posture and attain the visibility you require to understand exactly where dangers are. These assessments comprehensively evaluate your organization’s cybersecurity practices and infrastructure and can selection in scope and frequency relying on your organization’s desires and the maturity of your risk software.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
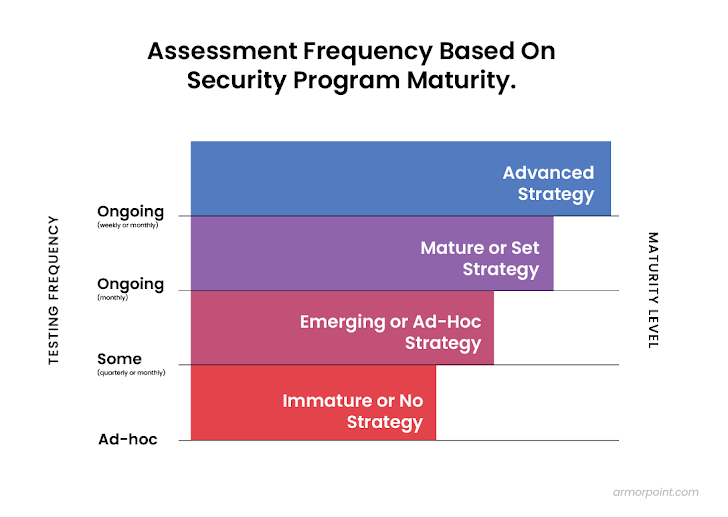
Security Maturity and Your Screening Frequency
- Immature or No Risk Technique: Assessments are not carried out on an ongoing frequency or are carried out on an ad-hoc foundation.
- Emerging or Advertisement-Hoc Risk Strategy: Assessments are done with some frequency, commonly quarterly or monthly.
- Experienced or Set Tactic: Assessments are executed on an ongoing foundation, typically month to month.
- Superior Strategy: Frequently assessments are engrained in the total risk program and get area on a month to month or weekly foundation dependent on the sort of exam.
Instructed Screening Frequency by Common Framework
- NIST CSF: The Nationwide Institute of Requirements and Technology (NIST) guidelines range from quarterly to regular scans, based on the specific tips of the governing framework.
- PCI DSS: The Payment Card Marketplace Data Security Standard (PCI DSS) mandates quarterly scans.
- HIPAA: The Well being Info Defense Accountability Act (HIPAA) does not need certain scanning intervals but emphasizes the value of a perfectly-outlined evaluation technique.
Sorts of Frequent Assessments
- Vulnerability Scans
- Penetration Exams
- Breach and Ransomware Simulations
- Security Track record Scans
- Organization Impact Analyses
- Security Posture Assessment
Conducting assessments routinely permits your organization to preemptively establish probable security threats and vulnerabilities, significantly like preventive well being examine-ups for your organization’s cybersecurity.
ArmorPoint has a short while ago produced a security maturity self-evaluation. Choose the 15-question quiz to identify the gaps in your security posture.
The Top rated 6 Vulnerabilities
Now, let us check out the vulnerabilities normally located in the course of these frequent security posture assessments and their prospective impression on your organization’s security integrity.
Vulnerability Management Plan Gaps
A structured vulnerability administration program is the cornerstone of proactive cybersecurity for your corporation. It serves as your organization’s radar for immediately determining and addressing security weaknesses. Organizations that absence these a system expose by themselves to significant dangers these as greater exposure to recognized vulnerabilities, inefficient patch administration, and the lessened potential to prioritize critical vulnerabilities.
Deficiencies in Detection and Monitoring
Inadequate detection units can go away your organization blind to ongoing threats, allowing attackers to function undetected for extended durations. Without enough detection programs, this kind of as innovative Intrusion Detection Devices (IDS) or Security Details and Function Administration (SIEM) methods, there is a risk of delayed or skipped menace detection, greater dwell time for attackers, and a higher possible for information exfiltration. To boost this factor, it really is vital to introduce advanced monitoring instruments and methods. Deploying state-of-the-artwork danger detection and reaction systems, utilizing habits analytics for anomaly detection, and conducting threat-hunting routines are some of the key ways to enhance detection capabilities.
The absence of this kind of steps delays the identification of threats and hampers the capacity to reply properly in a well timed way. Implementing a strong, well-rounded detection and checking procedure is critical for maintaining a robust defense in opposition to evolving cyber threats. This consists of continually updating and refining detection methodologies to continue to be ahead of the most recent attack vectors and methods utilized by cybercriminals.
Lack of Policies and Strategies
Corporations have to have formalized cybersecurity policies and methods to correctly take care of security hazards. Without having these in area, there are several effects, which includes inconsistent security techniques throughout departments, weakened incident response capabilities, trouble in making sure compliance with restrictions, and higher publicity to authorized, regulatory, economical, and reputational consequences. Crafting and employing extensive security insurance policies involves building and documenting these policies plainly, guaranteeing they are communicated effectively to all employees, and educating them on the worth of compliance.
Normal testimonials, updates, and adaptations of these insurance policies are important to maintain pace with the evolving cyber threat landscape. This also ensures that the organization’s cybersecurity steps continue being applicable and powerful. In addition, acquiring a set of very well-described treatments helps in standardizing responses to security incidents, which aids in reducing the influence and rushing up restoration periods in the celebration of a breach.
Insufficient Screening Tactics
Typical testing of security techniques and incident response plans is crucial for determining weaknesses and guaranteeing preparedness for genuine-world attacks. This involves conducting frequent penetration testing to uncover vulnerabilities, building, practicing, and fantastic-tuning incident response plans, and engaging in third-party security assessments. The significance of common testing can not be overstated, as it not only allows in identifying vulnerabilities right before attackers do but also assesses the usefulness of present security controls.
In addition, common testing makes certain a swift and powerful reaction to incidents, mitigating likely destruction proactively. This practice is very important in sustaining an up-to-date and resilient cybersecurity posture, capable of defending versus the most recent security threats. Partaking with third-party specialists for assessments delivers an exterior standpoint, frequently uncovering blind places that interior teams may overlook.
Training and Cyber Recognition
Insufficiently experienced personnel can inadvertently introduce vulnerabilities and make an organization more inclined to attacks. The issue of inadequate teaching qualified prospects to misconfigurations, human errors, and failure to realize and respond to threats, therefore lessening the effectiveness of security controls. To deal with this, ways for security consciousness training are important. Offering ongoing cybersecurity teaching, encouraging skilled enhancement and certifications, and fostering a lifestyle of security consciousness are vital measures.
These instruction initiatives support ensure that workers at all concentrations are outfitted to detect and answer to security threats successfully. By maintaining the workforce educated and vigilant, companies can drastically lower the risk of breaches induced by human error. This proactive tactic to personnel training is a critical element of a extensive cybersecurity strategy.
Framework Adoption and Implementation
Choosing and adhering to a cybersecurity framework is important for businesses looking to establish a structured strategy to security. The requirement of frameworks lies in giving a clear roadmap for security, ensuring alignment with industry best tactics, and facilitating compliance with rules. The advised process for framework selection includes assessing your organization’s particular wants and risk tolerance, deciding upon a suitable framework (e.g., NIST Cybersecurity Framework), and customizing it to in good shape the organization’s exceptional demands.
Framework adoption and implementation deliver a structured and methodical solution to managing cybersecurity challenges. They also provide rules for location up sturdy security steps and protocols, as a result enhancing the over-all security posture of an corporation. Customizing the picked out framework guarantees that it aligns properly with the organization’s specific security needs, marketplace benchmarks, and regulatory needs.
Risk Appetite and Comprehending
Comprehending your organization’s risk appetite and integrating it into your cybersecurity strategy is vital for successful risk management. Analyzing the level of risk your firm is willing to acknowledge differs from a single group to a different and influences conclusion-producing and source allocation. This understanding of risk appetite is essential in aligning cybersecurity efforts with the organization’s risk tolerance and prioritizing security steps centered on risk assessments.
Risk informs method, and sustaining continual vigilance is necessary to keep track of evolving threats and adapt security procedures accordingly. This method ensures that cybersecurity measures are not only reactive but proactive, anticipating potential threats and mitigating them prior to they materialize. By comprehension and running risk proficiently, organizations can construct a resilient and robust cybersecurity posture tailored to their precise wants and risk tolerance amounts.
Mitigating Determined Vulnerabilities
Now that we have completely examined these typical vulnerabilities, it truly is critical to fully grasp how to prioritize their resolution centered on severity and opportunity effect. The to start with step is to get extra visibility into your organization’s vulnerabilities. At the time discovered, you can prioritize these vulnerabilities correctly to mitigate them. To mitigate these risks, it can be recommended to put into practice an business-acknowledged framework these kinds of as NIST CSF, CIS, or SANS. These frameworks guide corporations in establishing robust cybersecurity techniques and requires examining current security actions towards the framework’s requirements, building and utilizing proper insurance policies, and ensuring standard staff members teaching for awareness. Continuous monitoring and advancement are vital, as it allows for the timely identification and rectification of security gaps and vulnerabilities.
Acquire a proactive action towards strengthening your security posture. Collaborate with seasoned cybersecurity authorities who can assistance discover and handle your organization’s unique security gaps. Request a complimentary Cybersecurity Workshop from ArmorPoint these days.
Cybersecurity is not a 1-time effort and hard work it’s an ongoing commitment to shielding your organization’s belongings and status. By addressing these frequent vulnerabilities uncovered in security posture assessments and remaining vigilant, you can improve your security posture and minimize the risk of slipping target to cyberattacks.
Download a Cybersecurity Checklist to find out what gaps you have in your security posture.
1 https://www.tripwire.com/state-of-security/perception-vulnerability-management-report
Observed this posting intriguing? Adhere to us on Twitter and LinkedIn to study additional unique content material we submit.
Some elements of this short article are sourced from:
thehackernews.com


 Italian Data Protection Watchdog Accuses ChatGPT of Privacy Violations
Italian Data Protection Watchdog Accuses ChatGPT of Privacy Violations