A suspected Pakistan-aligned superior persistent threat (APT) group identified as Transparent Tribe has been connected to an ongoing cyber espionage campaign concentrating on Indian and Pakistani Android consumers with a backdoor identified as CapraRAT.
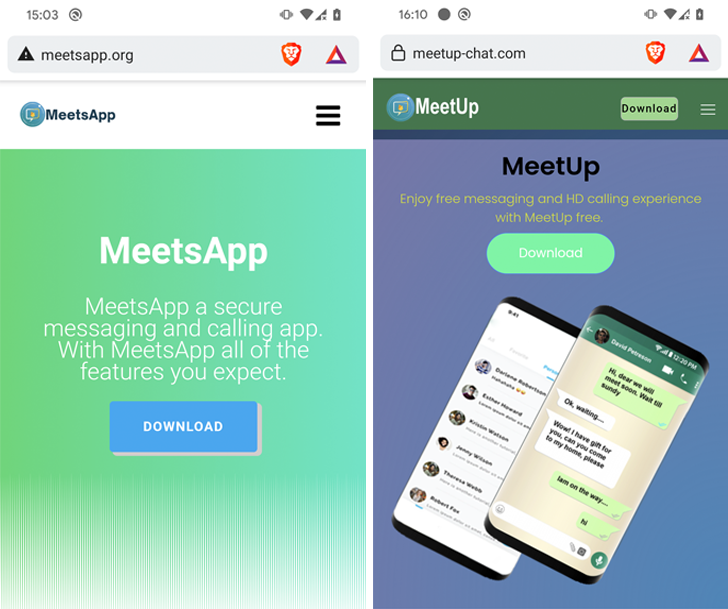
“Clear Tribe distributed the Android CapraRAT backdoor via trojanized safe messaging and contacting apps branded as MeetsApp and MeetUp,” ESET explained in a report shared with The Hacker Information.
As many as 150 victims, probable with military or political leanings, are approximated to have been targeted, with the malware (com.meetup.application) readily available to download from fake sites that masquerade as the formal distribution centers of these apps.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
It is staying suspected that the targets are lured by way of a honeytrap romance rip-off wherein the danger actor ways the victims via an additional system and persuades them to install the malware-laced applications beneath the pretext of “protected” messaging and calling.
Nonetheless, the apps, in addition to presenting the promised operation, arrive implanted with CapraRAT, a modified variation of the open source AndroRAT that was initially documented by Trend Micro in February 2022 and which reveals overlaps with a Windows malware regarded as CrimsonRAT.
The backdoor is packed with an extensive set of attributes that will allow it to choose screenshots and photographs, report phone calls and surrounding audio, and exfiltrate other delicate information. It can also make phone calls, ship SMS messages, and receive commands to download files.
That possessing stated, consumers are also required to generate an account by linking their phone quantities and completing an SMS verification action in get to accessibility the app’s functionalities.
Discover the Most current Malware Evasion Strategies and Avoidance Approaches
Ready to bust the 9 most hazardous myths about file-primarily based attacks? Join our approaching webinar and turn into a hero in the combat versus client zero bacterial infections and zero-working day security events!
RESERVE YOUR SEAT
The Slovak cybersecurity firm said the campaign is narrowly targeted and that it observed no evidence that suggests the apps were being accessible on the Google Enjoy Retailer.
Transparent Tribe, also referred to as APT36, Procedure C-Big, and Mythic Leopard, was not long ago attributed to another established of attacks targeting Indian govt businesses with malicious versions of a two-factor authentication answer identified as Kavach.
The conclusions also get there weeks just after cybersecurity business ThreatMon detailed a spear-phishing marketing campaign by SideCopy actors concentrating on Indian federal government entities with an aim to deploy an up to date version of a backdoor known as ReverseRAT.
Located this article exciting? Follow us on Twitter and LinkedIn to read additional exceptional information we article.
Some areas of this report are sourced from:
thehackernews.com

 Why Healthcare Can’t Afford to Ignore Digital Identity
Why Healthcare Can’t Afford to Ignore Digital Identity