Trojanized installers for the TOR anonymity browser are remaining utilized to goal consumers in Russia and Jap Europe with clipper malware developed to siphon cryptocurrencies due to the fact September 2022.
“Clipboard injectors […] can be silent for decades, exhibit no network exercise or any other symptoms of existence until finally the disastrous working day when they replace a crypto wallet handle,” Vitaly Kamluk, director of international investigation and investigation group (Wonderful) for APAC at Kaspersky, said.
Another notable facet of clipper malware is that its nefarious functions are not activated except if the clipboard information satisfy particular conditions, building it extra evasive.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
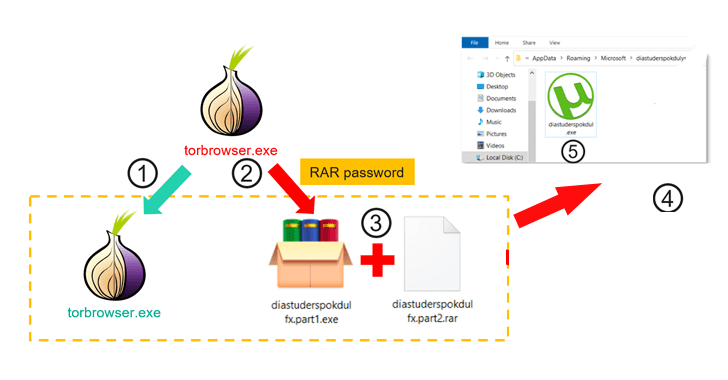
It is really not immediately clear how the installers are distributed, but proof points to the use of torrent downloads or some unfamiliar third-party resource because the Tor Project’s site has been subjected to blockades in Russia in latest decades.
Irrespective of the technique made use of, the installer launches the genuine executable, even though also concurrently launching the clipper payload that is built to monitor the clipboard material.
“If the clipboard includes text, it scans the contents with a established of embedded typical expressions,” Kamluk mentioned. “Ought to it obtain a match, it is changed with a single randomly chosen deal with from a hardcoded list.”
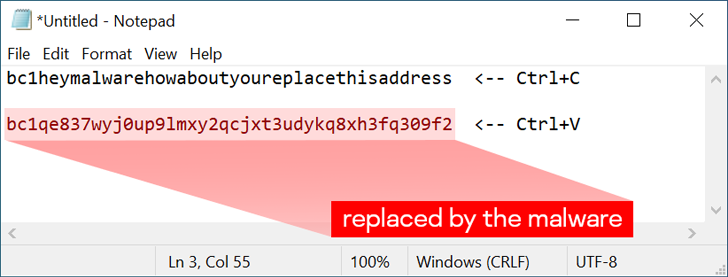
Every sample is packed with thousands of possible alternative addresses that’s chosen at random. It also will come with the capability to disable the malware by usually means of a distinctive hotkey combination (Ctrl+Alt+F10), an choice probable additional in the course of the screening period.
The Russian cybersecurity firm said it recorded around 16,000 detections, of which a majority are registered in Russia and Ukraine, adopted by the U.S., Germany, Uzbekistan, Belarus, China, the Netherlands, the U.K., and France. In all, the menace has been spotted in 52 nations around the world worldwide.
WEBINARDiscover the Concealed Dangers of Third-Party SaaS Applications
Are you aware of the hazards involved with 3rd-party app accessibility to your company’s SaaS applications? Sign up for our webinar to discover about the types of permissions being granted and how to reduce risk.
RESERVE YOUR SEAT
The scheme is approximated to have netted the operators just about $400,00 in illicit income as a result of the theft of Bitcoin, Litecoin, Ether, and Dogecoin. The sum of Monero belongings plundered is not identified owing to the privacy capabilities designed into the support.
It can be suspected that the campaign could be much larger in scope thanks to the likelihood that the menace actors could be leveraging other software package installers and hitherto unseen supply procedures to goal unwary buyers.
To secure towards such threats, it really is constantly suggested to down load program only from dependable and trusted resources.
Discovered this article intriguing? Abide by us on Twitter and LinkedIn to read through much more special information we post.
Some components of this post are sourced from:
thehackernews.com

 Just 1% of Cloud Permissions Are Actively Used
Just 1% of Cloud Permissions Are Actively Used