The Russia-connected hacking crew recognized as Turla has been observed working with an up-to-date edition of a regarded 2nd-stage backdoor referred to as Kazuar.
The new results occur from Palo Alto Networks Unit 42, which is tracking the adversary beneath its constellation-themed moniker Pensive Ursa.
“As the code of the upgraded revision of Kazuar reveals, the authors put distinctive emphasis on Kazuar’s capacity to operate in stealth, evade detection and thwart investigation attempts,” security scientists Daniel Frank and Tom Fakterman said in a specialized report.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“They do so employing a wide range of innovative anti-examination methods and by safeguarding the malware code with successful encryption and obfuscation techniques.”
Pensive Ursa, active since at least 2004, is attributed to the Russian Federal Security Provider (FSB). Previously this July, the Personal computer Crisis Reaction Staff of Ukraine (CERT-UA) implicated the risk group to attacks targeting the protection sector in Ukraine and Eastern Europe with backdoors these as DeliveryCheck and Kazuar.

Kazuar is a .NET-centered implant that initially came to light-weight in 2017 for its skills to stealthily interact with compromised hosts and exfiltrate facts. In January 2021, Kaspersky highlighted supply code overlaps in between the malware strain and Sunburst, a further backdoor applied in conjunction with the SolarWinds hack of 2020.
The enhancements to Kazuar indicate that the danger actor guiding the operation continues to evolve its attack techniques and mature in sophistication, although increasing its capability to regulate victims’ devices. This contains the use of strong obfuscation and custom string encryption strategies to evade detection.
“Kazuar operates in a multithreading product, while just about every of Kazuar’s most important functionalities operates as its individual thread,” the researchers described.
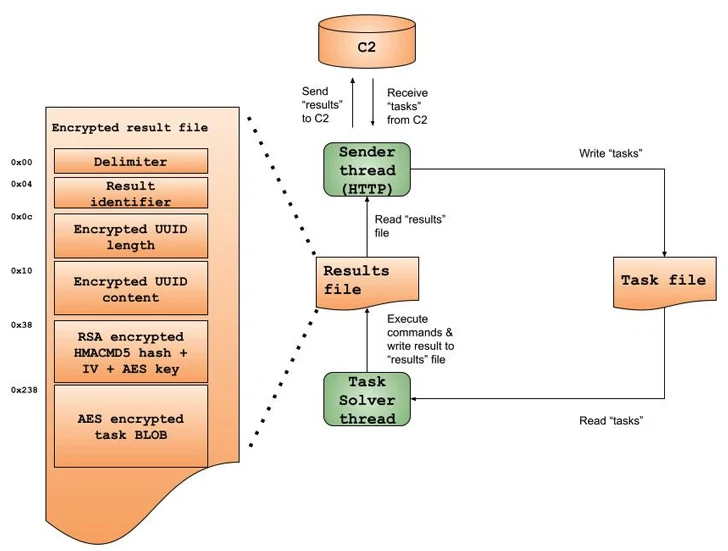
“In other words, one particular thread handles obtaining instructions or duties from its [command-and-control], even though a solver thread handles execution of these commands. This multithreading product permits Kazuar’s authors to set up an asynchronous and modular circulation management.”
The malware supports a wide array of characteristics – leaping from 26 commands in 2017 to 45 in the most up-to-date variant – that facilitates extensive system profiling, facts collection, credential theft, file manipulation, and arbitrary command execution.
It also incorporates capabilities to established up automatic jobs that will run at specified intervals to gather method data, take screenshots, and grab data files from certain folders. Communication with C2 servers usually takes location in excess of HTTP.

“In addition to direct HTTP conversation with the C2, Kazuar has the skill to purpose as a proxy, to get and send out commands to other Kazuar brokers in the infected network,” the researchers said.
“It is doing this proxy conversation by using named pipes, building their names dependent on the machine’s GUID. Kazuar uses these pipes to build peer-to-peer conversation among unique Kazuar occasions, configuring every single as a server or a customer.”
What is actually more, the comprehensive anti-assessment functionalities lends Kazuar a significant degree of stealth, guaranteeing it stays idle and ceases all C2 conversation if it is getting debugged or analyzed.
The advancement comes as Kaspersky exposed that a variety of condition and industrial companies in Russia were targeted with a custom Go-based backdoor that performs knowledge theft as part of a spear-phishing campaign that commenced in June 2023. The menace actor guiding the operation is currently unidentified.
Located this post attention-grabbing? Adhere to us on Twitter and LinkedIn to study far more unique content we submit.
Some areas of this posting are sourced from:
thehackernews.com


 Alert: F5 Warns of Active Attacks Exploiting BIG-IP Vulnerability
Alert: F5 Warns of Active Attacks Exploiting BIG-IP Vulnerability