The threat actor powering the details-thieving malware recognized as Typhon Reborn has resurfaced with an up to date version (V2) that packs in enhanced capabilities to evade detection and resist examination.
The new version is provided for sale on the prison underground for $59 for every month, $360 for each year, or alternatively, for $540 for a life span membership.
“The stealer can harvest and exfiltrate sensitive details and employs the Telegram API to send out stolen information to attackers,” Cisco Talos researcher Edmund Brumaghin explained in a Tuesday report.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Typhon was 1st documented by Cyble in August 2022, detailing its myriad capabilities, like hijacking clipboard written content, capturing screenshots, logging keystrokes, and stealing data from crypto wallet, messaging, FTP, VPN, browser, and gaming applications.
Based on a further stealer malware called Prynt Stealer, Typhon is also able of offering the XMRig cryptocurrency miner. In November 2022, Palo Alto Networks Device 42 unearthed an up-to-date version dubbed Typhon Reborn.
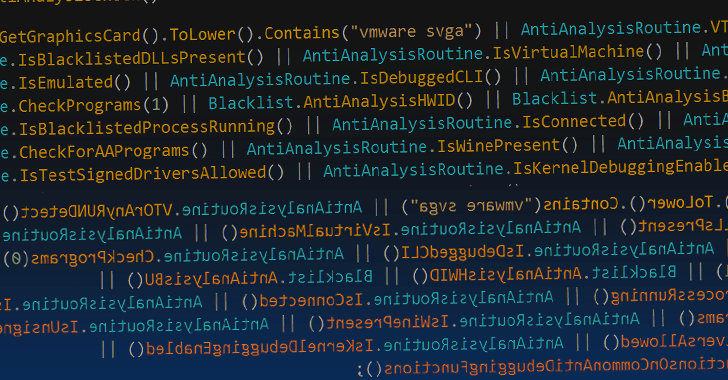
“This new version has enhanced anti-assessment strategies and it was modified to strengthen the stealer and file grabber functions,” Device 42 reported, pointing out the elimination of present options like keylogging and cryptocurrency mining in an evident attempt to reduce the prospects of detection.
The most current V2 variant, for each Cisco Talos, was marketed by its developer on January 31, 2023, on the Russian language dark web forum XSS.
“Typhon Reborn stealer is a closely refactored and improved variation of the more mature and unstable Typhon Stealer,” the malware creator reported, in addition to touting its economical price tag and the absence of any backdoors.
Like other malware, V2 arrives with selections to avoid infecting techniques that are situated in the Commonwealth of Independent States (CIS) countries. It, even so, notably excludes Ukraine and Georgia from the list.

Apart from incorporating extra anti-assessment and anti-virtualization checks, Typhon Reborn V2 gets rid of its persistence characteristics, instead opting to terminate itself immediately after exfiltrating the data.
The malware in the long run transmits the collected data in a compressed archive by way of HTTPS making use of the Telegram API, marking ongoing abuse of the messaging system.
“When the info has been correctly transmitted to the attacker, the archive is then deleted from the contaminated method,” Brumaghin claimed. “The malware then phone calls [a self-delete function] to terminate execution.”
Upcoming WEBINARLearn to Safe the Identification Perimeter – Confirmed Tactics
Strengthen your business enterprise security with our future professional-led cybersecurity webinar: Take a look at Id Perimeter procedures!
Never Pass up Out – Save Your Seat!
The findings arrive as Cyble disclosed a new Python-centered stealer malware named Creal that targets cryptocurrency users by using phishing internet sites mimicking respectable crypto mining products and services like Kryptex.
The malware is no distinct from Typhon Reborn in that it can be outfitted to siphon cookies and passwords from Chromium-centered web browsers as well as knowledge from instantaneous messaging, gaming, and crypto wallet applications.
That mentioned, the malware’s source code is readily available on GitHub, thus allowing other threat actors to alter the malware to accommodate their requires and making it a potent risk.
“Creal Stealer is able of exfiltrating information applying Discord webhooks and various file-hosting and sharing platforms these kinds of as Anonfiles and Gofile,” Cyble stated in a report revealed very last 7 days.
“The development of making use of open resource code in malware is escalating between cybercriminals, given that it will allow them to create subtle and tailored attacks with minimal bills.”
Identified this short article exciting? Stick to us on Twitter and LinkedIn to read through far more distinctive content material we write-up.
Some pieces of this short article are sourced from:
thehackernews.com

 New “Rorschach” Ransomware Spread Via Commercial Product
New “Rorschach” Ransomware Spread Via Commercial Product