The U.S. authorities on Tuesday introduced the court-licensed disruption of a world-wide network compromised by an superior malware strain recognised as Snake wielded by Russia’s Federal Security Support (FSB).
Snake, dubbed the “most advanced cyber espionage instrument,” is the handiwork of a Russian state-sponsored team named Turla (aka Iron Hunter, Mystery Blizzard, SUMMIT, Uroburos, Venomous Bear, and Waterbug), which the U.S. authorities attributes to a device inside Middle 16 of the FSB.
The risk actor has a observe report of greatly concentrating on entities in Europe, the Commonwealth of Unbiased States (CIS), and countries affiliated with NATO, with current action growing its footprint to incorporate Center Eastern nations deemed a menace to nations supported by Russia in the location.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“For almost 20 decades, this device […] has used variations of the Snake malware to steal sensitive documents from hundreds of computer system units in at the very least 50 nations around the world, which have belonged to North Atlantic Treaty Business (NATO) member governments, journalists, and other targets of curiosity to the Russian Federation,” the Justice Department said.
“Right after thieving these documents, Turla exfiltrated them by means of a covert network of unwitting Snake-compromised personal computers in the United States and about the globe.”

The neutralization was orchestrated as aspect of an work dubbed Procedure MEDUSA by implies of a device produced by the U.S. Federal Bureau of Investigation (FBI) codenamed PERSEUS that permitted the authorities to issue commands to the malware that induced it to “overwrite its have crucial factors” on infected devices.
The self-destruct directions, engineered after decrypting and decoding the malware’s network communications, brought about the “Snake implant to disable itself with out influencing the host pc or reputable programs on the computer system,” the company said.
Snake, according to an advisory unveiled by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), is developed as a covert device for extensive-term intelligence assortment on higher-priority targets, enabling the adversary to produce a peer-to-peer (P2P) network of compromised programs throughout the environment.
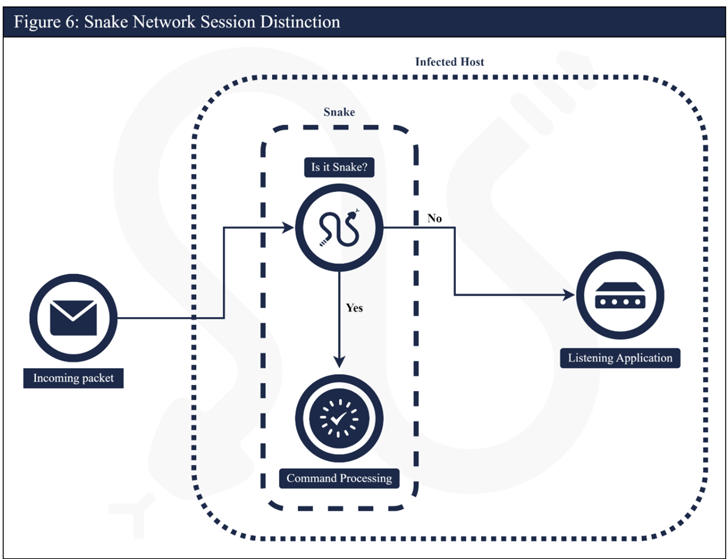
What is actually more, several units in the P2P network served as relay nodes to route disguised operational website traffic to and from Snake malware implanted on FSB’s best targets, creating the exercise tough to detect.
The C-dependent cross-platform malware further employs customized interaction methods to increase a new layer of stealth and options a modular architecture that lets for an efficient way to inject or modify factors to increase its capabilities and retain persistent access to beneficial information.
“Snake demonstrates very careful computer software engineering structure and implementation, with the implant that contains shockingly handful of bugs given its complexity,” CISA claimed, including first versions of the implant were produced about early 2004.
“The identify Uroburos is appropriate, as the FSB cycled it by virtually constant phases of up grade and redevelopment.”
Impending WEBINARLearn to Quit Ransomware with Actual-Time Defense
Sign up for our webinar and master how to cease ransomware attacks in their tracks with authentic-time MFA and assistance account protection.
Conserve My Seat!
Infrastructure related with the Kremlin-backed group has been recognized in over 50 nations across North America, South The us, Europe, Africa, Asia, and Australia, despite the fact that its concentrating on is assessed to be extra tactical, encompassing authorities networks, exploration amenities, and journalists.
Victimized sectors within just the U.S. involve education, little corporations, and media organizations, as properly as critical infrastructure sectors this sort of as governing administration services, economic companies, critical manufacturing, and communications.
Irrespective of these setbacks, Turla continues to be an active and formidable adversary, unleashing an array of practices and equipment to breach its targets throughout Windows, macOS, Linux, and Android.
The progress comes a minimal more than a 12 months following U.S. regulation enforcement and intelligence agencies disarmed a modular botnet known as Cyclops Blink controlled by a further Russian nation-point out actor referred to as Sandworm.
Located this report appealing? Observe us on Twitter and LinkedIn to read additional exclusive information we submit.
Some areas of this post are sourced from:
thehackernews.com


 ISACA: Companies Still Face Many Barriers to Achieving Digital Trust
ISACA: Companies Still Face Many Barriers to Achieving Digital Trust