Ukraine has arrive under a refreshing cyber onslaught from Russia that associated the deployment of a earlier undocumented Golang-primarily based info wiper dubbed SwiftSlicer.
ESET attributed the attack to Sandworm, a country-state group connected to Armed forces Device 74455 of the Major Intelligence Directorate of the Normal Employees of the Armed Forces of the Russian Federation (GRU).
“The moment executed it deletes shadow copies, recursively overwrites files situated in %CSIDL_System%motorists, %CSIDL_Procedure_Push%WindowsNTDS and other non-program drives and then reboots computer,” ESET disclosed in a collection of tweets.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The overwrites are accomplished by working with randomly generated byte sequences to fill 4,096 byte-duration blocks. The intrusion was discovered on January 25, 2023, the Slovak cybersecurity corporation included.
Sandworm, also tracked beneath the monikers BlackEnergy, Electrum, Iridium, Iron Viking, TeleBots, and Voodoo Bear, has a historical past of staging disruptive and damaging cyber campaigns targeting businesses globally given that at the very least 2007.
The sophistication of the menace actor is evidenced by its various distinct eliminate chains, which comprise a extensive assortment of personalized resources these as BlackEnergy, GreyEnergy, Industroyer, NotPetya, Exaramel, and Cyclops Blink.
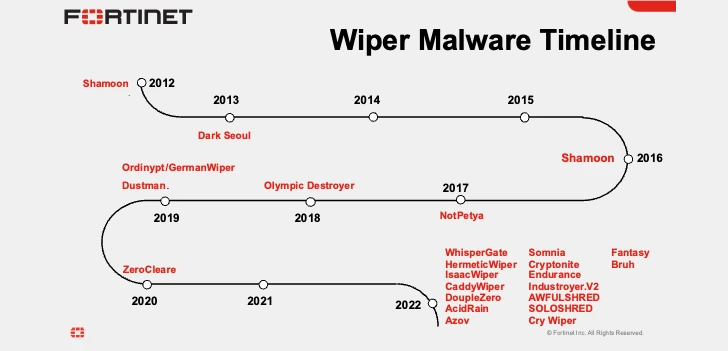
In 2022 alone, coinciding with Russia’s navy invasion of Ukraine, Sandworm has unleashed WhisperGate, HermeticWiper, IsaacWiper, CaddyWiper, Industroyer2, Status, and RansomBoggs from critical infrastructure in Ukraine.
“When you feel about it, the growth in wiper malware for the duration of a conflict is barely a surprise,” Fortinet FortiGuard Labs researcher Geri Revay explained in a report revealed this 7 days. “It can scarcely be monetized. The only practical use case is destruction, sabotage, and cyberwar.”
The discovery of SwiftSlicer details to the constant use of wiper malware variants by the Russian adversarial collective in attacks built to wreak havoc in Ukraine.
The enhancement also comes as the Laptop or computer Emergency Response Workforce of Ukraine (CERT-UA) joined Sandworm to a modern mainly unsuccessful cyberattack on the nationwide news agency Ukrinform.
The intrusion, which is suspected of acquiring been carried out no afterwards than December 7, 2022, entailed the use of 5 different items of info wiping courses, namely CaddyWiper, ZeroWipe, SDelete, AwfulShred, and BidSwipe targeting Windows, Linux, and FreeBSD devices.
“It was founded that the last phase of the cyberattack was initiated on January 17, 2023,” CERT-UA explained in an advisory. “However, it had only partial results, in certain, in relation to various knowledge storage systems.”
Sandworm is not the only group that has its eyes on Ukraine. Other Russian point out-sponsored actors these types of as APT29, COLDRIVER, and Gamaredonhave actively specific a vary of Ukrainian organizations given that the onset of the war.
Located this report exciting? Comply with us on Twitter and LinkedIn to study much more distinctive content material we write-up.
Some components of this write-up are sourced from:
thehackernews.com

 Multiple Vulnerabilities Found In Healthcare Software OpenEMR
Multiple Vulnerabilities Found In Healthcare Software OpenEMR