Cybersecurity scientists have identified a targeted procedure versus Ukraine that has been found leveraging a approximately seven-12 months-outdated flaw in Microsoft Office to produce Cobalt Strike on compromised units.
The attack chain, which took spot at the end of 2023 according to Deep Instinct, employs a PowerPoint slideshow file (“sign-2023-12-20-160512.ppsx”) as the commencing place, with the filename implying that it may have been shared by using the Signal immediate messaging app.
That acquiring said, there is no true evidence to indicate that the PPSX file was dispersed in this way, even even though the Computer system Emergency Reaction Workforce of Ukraine (CERT-UA) has uncovered two distinctive campaigns that have applied the messaging application as a malware shipping and delivery vector in the past.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Just last 7 days, the company disclosed that Ukrainian armed forces are becoming significantly specific by the UAC-0184 group through messaging and dating platforms to serve malware like HijackLoader (aka GHOSTPULSE and SHADOWLADDER), XWorm, and Remcos RAT, as very well as open-source plans these types of as sigtop and tusc to exfiltrate knowledge from computer systems.

“The PPSX (PowerPoint slideshow) file appears to be an old instruction guide of the U.S. Army for mine clearing blades (MCB) for tanks,” security researcher Ivan Kosarev claimed. “The PPSX file includes a remote romance to an exterior OLE object.”
This will involve the exploitation of CVE-2017-8570 (CVSS rating: 7.8), a now-patched distant code execution bug in Office that could allow an attacker to carry out arbitrary actions upon convincing a victim to open a specifically crafted file, to load a remote script hosted on weavesilk[.]place.
The closely obfuscated script subsequently launches an HTML file that contains JavaScript code, which, in flip, sets up persistence on the host by means of Windows Registry and drops a future-phase payload that impersonates the Cisco AnyConnect VPN consumer.
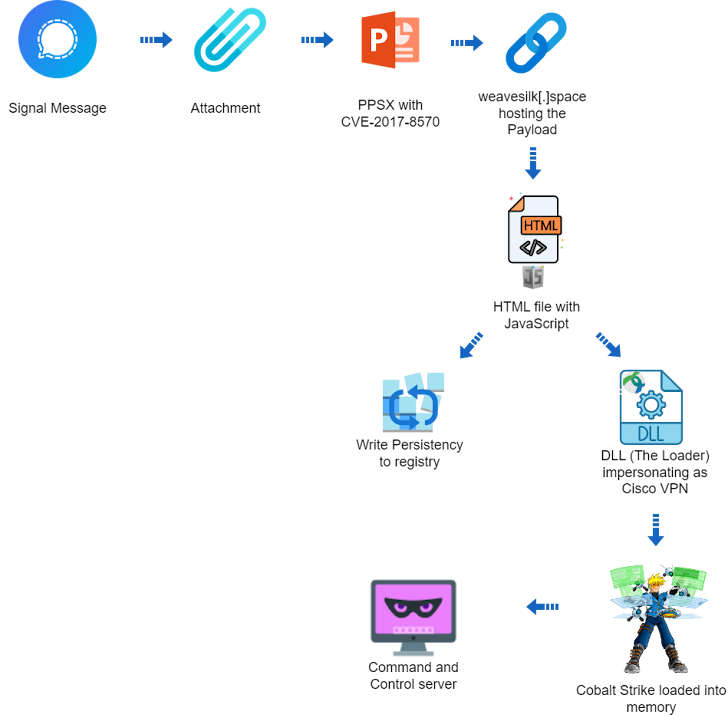
The payload contains a dynamic-connection library (DLL) that finally injects a cracked Cobalt Strike Beacon, a authentic pen-tests software, right into method memory and awaits for even more directions from a command-and-command (C2) server (“petapixel[.]enjoyable”).
The DLL also packs in capabilities to examine if it can be staying executed in a digital machine and evade detection by security software.
Deep Intuition mentioned it could neither backlink the attacks to a certain risk actor or team nor exclude the chance of a red teaming workout. Also unclear is the actual conclude goal of the intrusion.
“The lure contained military-relevant information, suggesting it was focusing on army staff,” Kosarev claimed.
“But the domain names weavesilk[.]area and petapixel[.]enjoyment are disguised as an obscure generative artwork web page (weavesilk[.]com) and a popular photography internet site (petapixel[.]com). These are unrelated, and it is really a little bit puzzling why an attacker would use these particularly to idiot army personnel.”
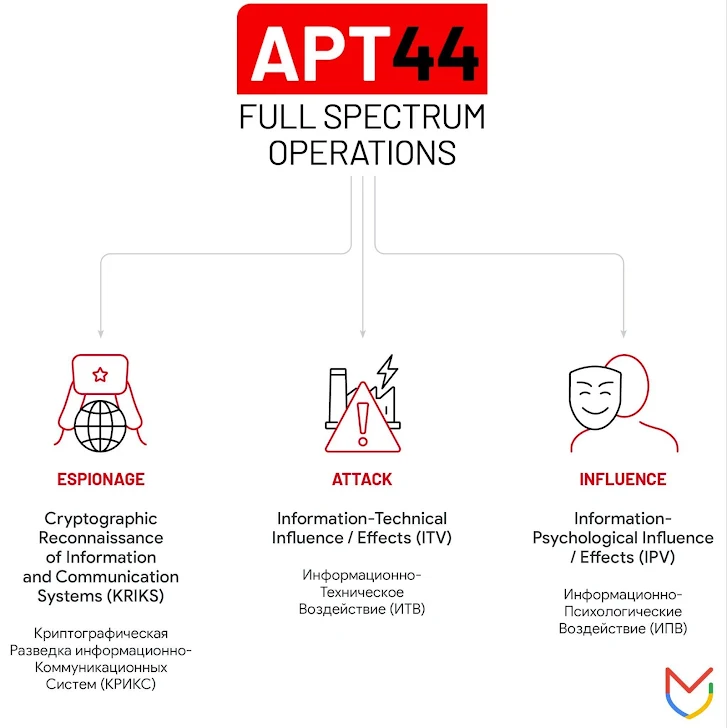
The disclosure arrives as CERT-UA revealed that about 20 electricity, drinking water, and heating suppliers in Ukraine have been focused by a Russian state-sponsored team known as UAC-0133, a sub-cluster inside Sandworm (aka APT44, FROZENBARENTS, Seashell Blizzard, UAC-0002, and Voodoo Bear), which is liable for a bulk of all the disruptive and damaging operations towards the state.
The attacks, which aimed to sabotage critical operations, include the use of malware like Kapeka (aka ICYWELL, KnuckleTouch, QUEUESEED, and wrongsens) and its Linux variant BIASBOAT, as perfectly as GOSSIPFLOW and LOADGRIP.

While GOSSIPFLOW is a Golang-centered SOCKS5 proxy, LOADGRIP is an ELF binary written in C which is used to load BIASBOAT on compromised Linux hosts.
Sandworm is a prolific and hugely adaptive menace group linked to Unit 74455 within the Main Directorate of the Standard Personnel of the Armed Forces of the Russian Federation (GRU). It is identified to be active due to the fact at least 2009, with the adversary also tied to a few hack-and-leak hacktivist personas these kinds of as XakNet Crew, CyberArmyofRussia_Reborn, and Solntsepek.
“Sponsored by Russian armed forces intelligence, APT44 is a dynamic and operationally experienced threat actor that is actively engaged in the whole spectrum of espionage, attack, and impact operations,” Mandiant stated, describing the innovative persistent menace (APT) as engaged in a multi-pronged work to support Russia gain a wartime advantage because January 2022.
“APT44 functions are world wide in scope and mirror Russia’s extensive ranging national interests and ambitions. Patterns of activity in excess of time point out that APT44 is tasked with a selection of distinctive strategic priorities and is highly probably found by the Kremlin as a flexible instrument of power able of serving both equally enduring and emerging intelligence needs.”
Found this write-up fascinating? Stick to us on Twitter and LinkedIn to study extra exclusive written content we submit.
Some pieces of this write-up are sourced from:
thehackernews.com


 Bogus npm Packages Used to Trick Software Developers into Installing Malware
Bogus npm Packages Used to Trick Software Developers into Installing Malware