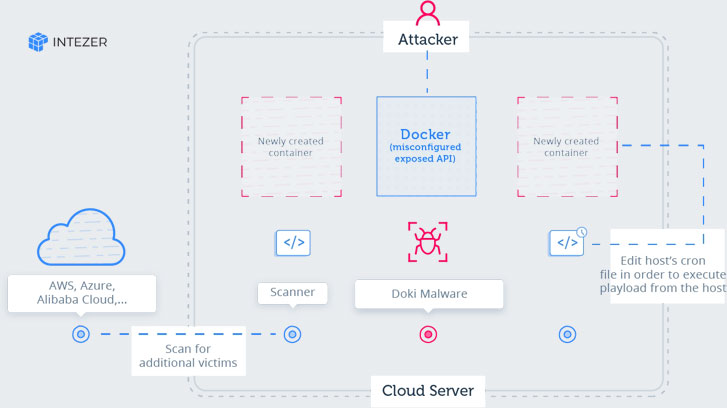
Cybersecurity researchers currently uncovered a entirely undetectable Linux malware that exploits undocumented procedures to continue to be under the radar and targets publicly accessible Docker servers hosted with well known cloud platforms, which include AWS, Azure, and Alibaba Cloud.
Docker is a well-known platform-as-a-service (PaaS) remedy for Linux and Windows made to make it less complicated for builders to build, exam, and operate their apps in a loosely isolated atmosphere named a container.
According to the most up-to-date investigation Intezer shared with The Hacker News, an ongoing Ngrok mining botnet marketing campaign not too long ago began scanning the Internet for misconfigured Docker API endpoints and contaminated numerous susceptible servers with new malware.
Although the Ngrok mining botnet is energetic for the previous two years, the new campaign is mostly focused on using regulate above misconfigured Docker servers and exploiting them to established up destructive containers with cryptominers managing on the victims’ infrastructure.
Dubbed ‘Doki,’ the multi-threaded malware leverages “an undocumented strategy to get in touch with its operator by abusing the Dogecoin cryptocurrency blockchain in a distinctive way in purchase to dynamically deliver its C2 domain tackle irrespective of samples becoming publicly obtainable in VirusTotal.”
According to researchers, the malware:
has been developed to execute commands been given from its operators,
employs a Dogecoin cryptocurrency block explorer to produce its C2 domain in authentic-time dynamically,
works by using the embedTLS library for cryptographic features and network communication,
crafts exclusive URLs with a small life time and utilizes them to down load payloads all through the attack.
“The malware makes use of the DynDNS provider and a unique Area Generation Algorithm (DGA) based mostly on the Dogecoin cryptocurrency blockchain in buy to uncover the area of its C2 in genuine time.”
Besides this, the attackers powering this new marketing campaign have also managed to compromise the host equipment by binding freshly designed containers with the server’s root directory, enabling them to accessibility or modify any file on the method.
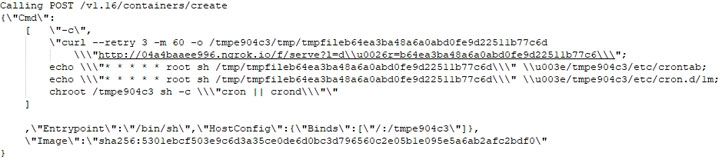
“By using the bind configuration the attacker can handle the cron utility of the host. The attacker modifies the host’s cron to execute the downloaded payload each moment.”
“This assault is quite harmful thanks to the reality the attacker makes use of container escape tactics to gain comprehensive management of the victim’s infrastructure.”
As soon as accomplished, the malware also leverages compromised programs to more scan the network for ports related with Redis, Docker, SSH, and HTTP, employing a scanning resource like zmap, zgrap, and jq.
Doki managed to continue to be under the radar for much more than six months inspite of acquiring been uploaded to VirusTotal on January 14, 2020, and scanned various situations considering that. Astonishingly, at the time of writing, it can be however undetectable by any of the 61 top malware detection engines.
The most distinguished container software program has been targeted for the 2nd time in a thirty day period. Late last month, malicious actors had been found targeting exposed Docker API endpoints and crafted malware-infested photographs to aid DDoS assaults and mine cryptocurrencies.
Consumers and businesses who operate Docker instances are encouraged not to expose docker APIs to the Internet, but if you even now need to have to, ensure that it is reachable only from a trustworthy network or VPN, and only to reliable end users to command your Docker daemon.
If you deal with Docker from a web server to provision containers via an API, you really should be even extra cautious than common with parameter checking to make certain that a destructive person can’t pass crafted parameters triggering Docker to produce arbitrary containers.
Adhere to most effective Docker security methods listed here.
Located this article intriguing? Comply with THN on Fb, Twitter and LinkedIn to read through much more distinctive written content we submit.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code


 Identity Governance Organization Critical as Orgs Return to Get the job done, Say IT Experts
Identity Governance Organization Critical as Orgs Return to Get the job done, Say IT Experts