In the ever-evolving landscape of cybersecurity, attackers are generally searching for vulnerabilities and exploits inside organizational environments. They do not just concentrate on single weaknesses they are on the hunt for combos of exposures and attack solutions that can lead them to their sought after goal.
In spite of the existence of quite a few security equipment, organizations frequently have to offer with two big issues Initially, these instruments usually deficiency the ability to efficiently prioritize threats, leaving security pros in the dark about which issues need to have quick focus. 2nd, these tools generally are unsuccessful to supply context about how personal issues appear with each other and how they can be leveraged by attackers to entry critical assets. This lack of perception can lead organizations to possibly endeavor to correct anything or, far more dangerously, tackle nothing at all at all.
In this write-up, we delve into 7 real-lifestyle attack route scenarios that our in-house industry experts encountered whilst employing XM Cyber’s Exposure Management System in customers’ hybrid environments throughout 2023. These eventualities give precious insights into the dynamic and ever-modifying nature of cyber threats.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
From intricate attack paths that need various techniques to alarmingly uncomplicated ones with just a couple ways, our investigation unveils a staggering fact: 75% of an organization’s critical assets can be compromised in their present-day security state. Even a lot more disconcerting, 94% of these critical property can be compromised in four measures or fewer from the first breach stage. This variability underscores the have to have for the correct resources to foresee and thwart these threats proficiently.
Now, without even more ado, let’s examine these real-existence attack paths and the lessons they instruct us.
Tale # 1
Buyer: A substantial economical business.
Scenario: Plan client simply call.
Attack Path: Exploiting DHCP v6 broadcasts to execute a Gentleman-in-the-Center attack, possibly compromising about 200 Linux techniques.
Effect: Compromise of many Linux servers with probable for information exfiltration or ransom attacks.
Remediation: Disabling DHCPv6 and patching vulnerable programs, alongside with educating developers on SSH crucial security.
In this situation, a large financial company faced the threat of a Person-in-the-Middle attack thanks to unsecured DHCP v6 broadcasts. The attacker could have exploited this vulnerability to compromise roughly 200 Linux programs. This compromise could have resulted in data breaches, ransom attacks, or other destructive pursuits. Remediation associated disabling DHCPv6, patching susceptible programs, and maximizing developer schooling on SSH vital security.

Tale # 2
Purchaser: A large vacation business.
Situation: Post-merger infrastructure integration.
Attack Route: Neglected server with unapplied patches, together with PrintNightmare and EternalBlue, potentially compromising critical property.
Impact: Possible risk to critical belongings.
Remediation: Disabling the needless server, decreasing over-all risk.
In this state of affairs, a big travel enterprise, following a merger, unsuccessful to implement critical patches on a neglected server. This oversight remaining them susceptible to known vulnerabilities like PrintNightmare and EternalBlue, most likely jeopardizing critical property. The option, nevertheless, was somewhat clear-cut: disabling the pointless server to minimize overall risk.

Tale # 3
Consumer: A huge healthcare service provider.
Situation: Routine customer phone.
Attack Route: An attack path leveraging authenticated users’ team permissions to perhaps grant domain admin accessibility.
Effect: Complete area compromise.
Remediation: Prompt removal of permissions to modify paths.
In this circumstance, a big health care provider faced the alarming prospect of an attack path that exploited authenticated users’ team permissions, possibly granting area admin obtain. Swift action was essential, involving the prompt removing of permissions to modify paths.

Story # 4
Consumer: A world-wide monetary establishment.
Situation: Regimen shopper connect with.
Attack Route: Intricate path involving support accounts, SMB ports, SSH keys, and IAM roles, with potential to compromise critical property.
Effect: Likely disastrous if exploited.
Remediation: Swift removal of personal SSH keys, resetting IAM role permissions, and consumer removing.
In this circumstance, a world-wide economical institution faced a sophisticated attack route that leveraged service accounts, SMB ports, SSH keys, and IAM roles. The probable for compromise of critical assets loomed significant. Swift remediation was needed, involving the elimination of private SSH keys, resetting IAM part permissions, and user removal.
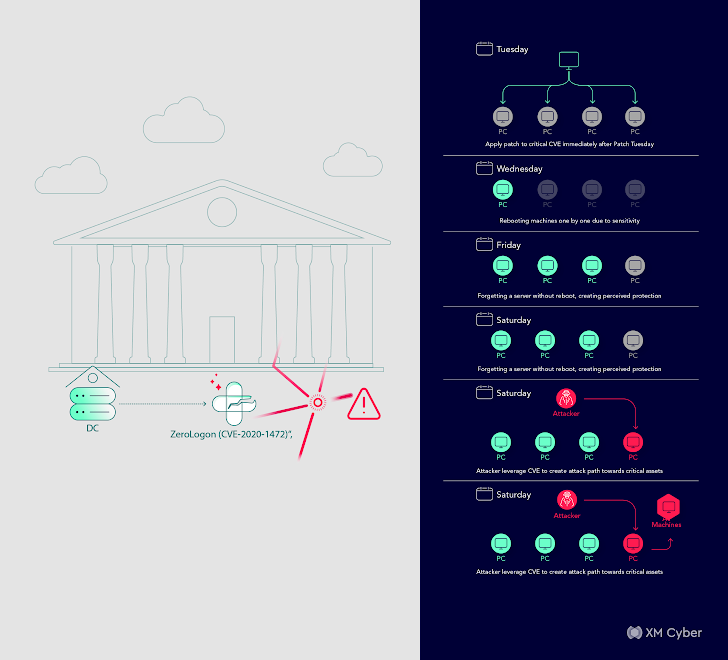
Tale # 5
Shopper: A community transportation business.
State of affairs: Onboarding assembly.
Attack Route: Direct path from a DMZ server to area compromise, possibly main to area controller compromise.
Effects: Potential compromise of the complete area.
Remediation: Proscribing permissions and consumer removal.
In this circumstance, a community transportation organization found out a immediate path from a DMZ server to domain compromise, which could have in the long run led to the compromise of the whole area. Rapid remediation was important, involving the restriction of permissions and consumer removing.
.e book-information padding: 20px .e book-graphic img border-radius: 5px .xm_container screen: flex align-things: center margin: 20px 10px 30px qualifications: #f9fbff color: #160755 padding: 20px border: 2px sound #d9deff border-radius: 10px text-align: left box-shadow: 5px 5px #e2ebff -webkit-border-top-remaining-radius: 15px -moz-border-radius-topleft: 15px -webkit-border-base-ideal-radius: 15px -moz-border-radius-bottomright: 15px .book-impression flex: 250pxmargin-appropriate: 20px .e-book-information flex: 1 .book-information ul margin: 15px .e book-specifics ul li margin-base: 5px @media (max-width: 600px) .xm_container flex-way: column .e-book-impression margin-right: margin-bottom: 20px
Energy of Attack Paths in Cloud
Unlock cloud security insights with our Book, “The Energy of Attack Paths in Cloud.” Master to visualize and cut off attack routes, safeguarding critical belongings. Bridge Security and IT teams for swift remediation. Elevate your cybersecurity activity nowadays!
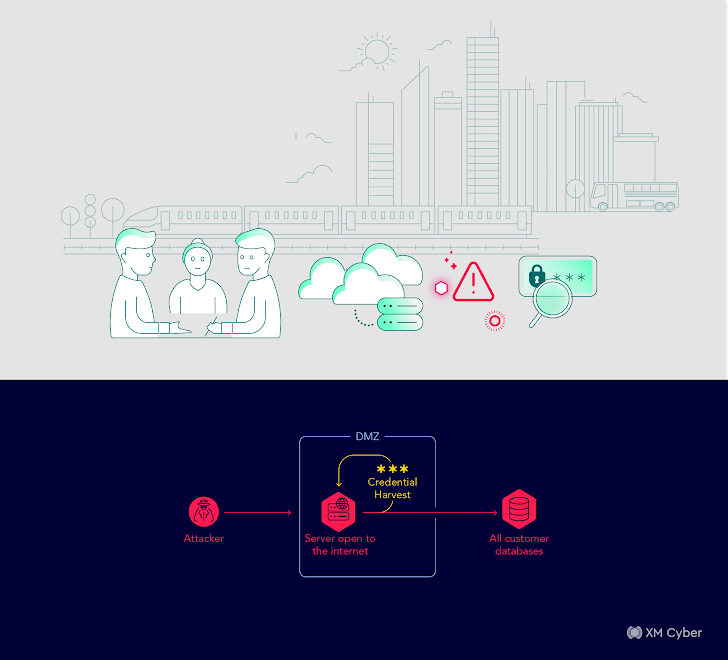
Tale # 6
Shopper: A healthcare facility with a potent target on security.
Situation: Regimen client connect with.
Attack Route: Energetic Directory misconfiguration letting any authenticated person to reset passwords, developing a broad attack floor.
Effect: Opportunity account takeovers.
Remediation: Lively directory security hardening and a comprehensive remediation plan.
This situation unveiled a hospital’s vulnerability because of to an Energetic Listing misconfiguration. This misconfiguration permitted any authenticated person to reset passwords, drastically growing the attack area. Remediation necessitated active directory security hardening and the implementation of a thorough remediation plan.

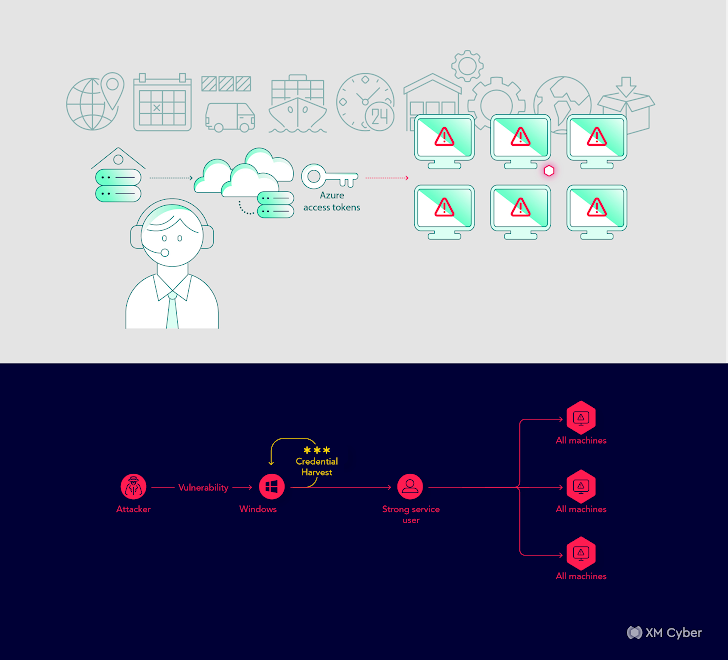
Story # 7
Shopper: A big delivery and logistics enterprise.
State of affairs: Regime client get in touch with.
Attack Path: An intricate attack route from a workstation device to Azure, probably compromising the complete enterprise surroundings.
Effect: Likely compromise of the complete company natural environment.
Remediation: Person purpose changes and issue remediation.
In this state of affairs, a key shipping and delivery and logistics enterprise uncovered an intricate attack path that could have allowed attackers to compromise the overall enterprise environment. Remediation essential adjustments to user roles and the comprehensive remediation of identified issues.
The Massive Takeaway
The typical thread in these scenarios is that every corporation experienced sturdy security steps in position, adhered to most effective procedures, and believed they recognized their risks. Having said that, they generally viewed these risks in isolation, producing a phony feeling of security.
Luckily for us these companies were being capable to get a context-centered comprehending of their environments with the correct tools. They figured out how various issues can and do intersect and consequently prioritized necessary remediations, to reinforce their security posture and mitigate these threats proficiently.
Located this write-up appealing? Abide by us on Twitter and LinkedIn to examine additional distinctive content material we submit.
Some pieces of this short article are sourced from:
thehackernews.com

 TetrisPhantom: Cyber Espionage via Secure USBs Targets APAC Governments
TetrisPhantom: Cyber Espionage via Secure USBs Targets APAC Governments