It’s the next Tuesday of the month, and Microsoft has unveiled yet another set of security updates to repair a full of 97 flaws impacting its computer software, one particular of which has been actively exploited in ransomware attacks in the wild.
7 of the 97 bugs are rated Critical and 90 are rated Significant in severity. Interestingly, 45 of the shortcomings are remote code execution flaws, followed by 20 elevation of privilege vulnerabilities. The updates also stick to fixes for 26 vulnerabilities in its Edge browser that were being unveiled more than the previous thirty day period.
The security flaw that is arrive beneath lively exploitation is CVE-2023-28252 (CVSS rating: 7.8), a privilege escalation bug in the Windows Common Log File Process (CLFS) Driver.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“An attacker who correctly exploited this vulnerability could acquire System privileges,” Microsoft claimed in an advisory, crediting researchers Boris Larin, Genwei Jiang, and Quan Jin for reporting the issue.
CVE-2023-28252 is the fourth privilege escalation flaw in the CLFS part that has arrive under active abuse in the past yr by itself soon after CVE-2022-24521, CVE-2022-37969, and CVE-2023-23376 (CVSS scores: 7.8). At least 32 vulnerabilities have been identified in CLFS due to the fact 2018.
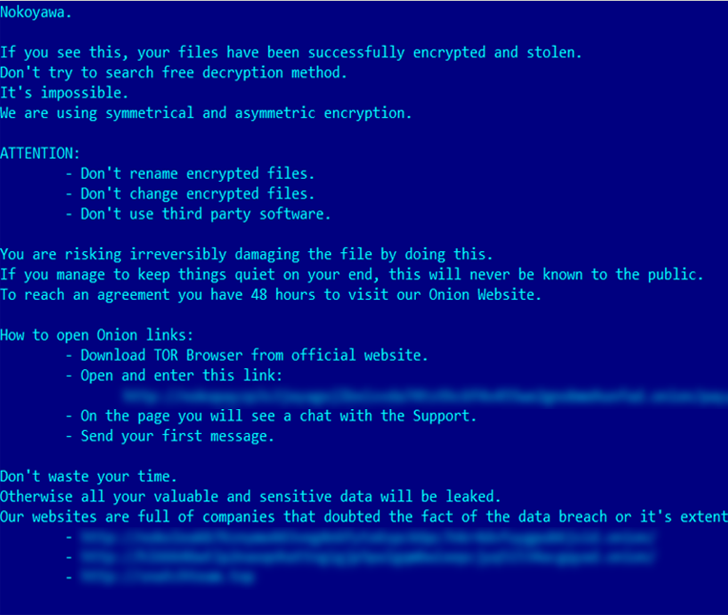
In accordance to Russian cybersecurity company Kaspersky, the vulnerability has been weaponized by a cybercrime team to deploy Nokoyawa ransomware versus smaller and medium-sized organizations in the Middle East, North The united states, and Asia.
“CVE-2023-28252 is an out-of-bounds produce (increment) vulnerability that can be exploited when the program makes an attempt to lengthen the metadata block,” Larin claimed. “The vulnerability gets induced by the manipulation of the base log file.”
In mild of ongoing exploitation of the flaw, CISA included the Windows zero-working day to its catalog of Regarded Exploited Vulnerabilities (KEV), ordering Federal Civilian Executive Department (FCEB) organizations to secure their devices by Might 2, 2023.
Also patched are critical remote code execution flaws impacting DHCP Server Support, Layer 2 Tunneling Protocol, Raw Picture Extension, Windows Stage-to-Issue Tunneling Protocol, Windows Pragmatic Normal Multicast, and Microsoft Information Queuing (MSMQ).
The MSMQ bug, tracked as CVE-2023-21554 (CVSS rating: 9.8) and dubbed QueueJumper by Verify Stage, could guide to unauthorized code execution and take around a server by sending a specifically crafted destructive MSMQ packet to an MSMQ server.
“The CVE-2023-21554 vulnerability lets an attacker to possibly execute code remotely and without having authorization by reaching the TCP port 1801,” Look at Place researcher Haifei Li claimed. “In other terms, an attacker could gain regulate of the approach by just a single packet to the 1801/tcp port with the exploit, triggering the vulnerability.”
Two other flaws discovered in MSMQ, CVE-2023-21769 and CVE-2023-28302 (CVSS scores: 7.5), could be exploited to lead to a denial-of-company (DoS) ailment these types of as a assistance crash and Windows Blue Screen of Loss of life (BSoD).
Approaching WEBINARLearn to Secure the Identity Perimeter – Tested Tactics
Enhance your enterprise security with our upcoming professional-led cybersecurity webinar: Examine Identity Perimeter tactics!
Don’t Skip Out – Save Your Seat!
Microsoft has also updated its advisory for CVE-2013-3900, a WinVerifyTrust signature validation vulnerability, to involve the subsequent Server Main installation variations –
- Windows Server 2008 for 32-bit Units Services Pack 2
- Windows Server 2008 for x65-based Programs Assistance Pack 2
- Windows Server 2008 R2 for x64-based Methods Services 1
- Windows Server 2012
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019, and
- Windows Server 2022
The development arrives as North Korea-linked danger actors have been observed leveraging the flaw to include encrypted shellcode into genuine libraries with no invalidating the Microsoft-issued signature.
Software program Patches from Other Distributors
In addition to Microsoft, security updates have also been launched by other distributors in the past several months to rectify various vulnerabilities, which include —
- Adobe
- AMD
- Android
- Apache Tasks
- Apple
- Arm
- Aruba Networks
- Cisco
- Citrix
- CODESYS
- Dell
- Drupal
- F5
- Fortinet
- GitLab
- Google Chrome
- HP
- IBM
- Jenkins
- Juniper Networks
- Lenovo
- Linux distributions Debian, Oracle Linux, Red Hat, SUSE, and Ubuntu
- MediaTek
- Mozilla Firefox, Firefox ESR, and Thunderbird
- NETGEAR
- NVIDIA
- Palo Alto Networks
- Qualcomm
- Samba
- Samsung
- SAP
- Schneider Electric powered
- Siemens
- SonicWall, and
- Sophos
Found this write-up attention-grabbing? Comply with us on Twitter and LinkedIn to read through extra distinctive material we post.
Some areas of this write-up are sourced from:
thehackernews.com


 Lazarus Sub-Group Labyrinth Chollima Uncovered as Mastermind in 3CX Supply Chain Attack
Lazarus Sub-Group Labyrinth Chollima Uncovered as Mastermind in 3CX Supply Chain Attack