RedHat on Friday introduced an “urgent security alert” warning that two variations of a popular facts compression library named XZ Utils (beforehand LZMA Utils) have been backdoored with destructive code built to make it possible for unauthorized distant obtain.
The program offer chain compromise, tracked as CVE-2024-3094, has a CVSS rating of 10., indicating optimum severity. It impacts XZ Utils versions 5.6. (launched February 24) and 5.6.1 (unveiled March 9).
“Through a collection of complex obfuscations, the liblzma construct approach extracts a prebuilt item file from a disguised exam file current in the resource code, which is then made use of to modify distinct features in the liblzma code,” the IBM subsidiary mentioned in an advisory.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“This benefits in a modified liblzma library that can be applied by any software package linked in opposition to this library, intercepting and modifying the information conversation with this library.”
Precisely, the nefarious code baked into the code is created to interfere with the sshd daemon procedure for SSH (Protected Shell) by using the systemd software program suite, and potentially allow a threat actor to crack sshd authentication and attain unauthorized accessibility to the technique remotely “beneath the correct situation.”
Microsoft security researcher Andres Freund has been credited with exploring and reporting the issue on Friday. The seriously obfuscated destructive code is stated to have been launched about a collection of 4 commits to the Tukaani Task on GitHub by a consumer named JiaT75.
“Given the exercise about quite a few weeks, the committer is either instantly involved or there was some very serious compromise of their process,” Freund mentioned. “Sad to say the latter appears like the much less very likely rationalization, provided they communicated on various lists about the ‘fixes.'”
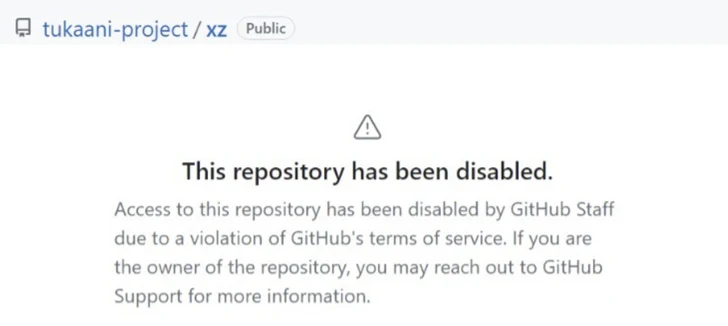
Microsoft-owned GitHub has since disabled the XZ Utils repository preserved by the Tukaani Venture “thanks to a violation of GitHub’s phrases of company.” There are at present no experiences of energetic exploitation in the wild.
Proof exhibits that the packages are only current in Fedora 41 and Fedora Rawhide, and do not affect Crimson Hat Business Linux (RHEL), Debian Secure, Amazon Linux, and SUSE Linux Enterprise and Leap.

Out of an abundance of caution, Fedora Linux 40 end users have been advised to downgrade to a 5.4 make. Some of the other Linux distributions impacted by the offer chain attack are below –
- Kali Linux (involving March 26 and 29)
- openSUSE Tumbleweed and openSUSE MicroOS (among March 7 and 28)
- Debian testing, unstable, and experimental variations (from 5.5.1alpha-.1 to 5.6.1-1)
The progress has prompted the U.S. Cybersecurity and Infrastructure Security Company (CISA) to issue an warn of its personal, urging buyers to downgrade XZ Utils to an uncompromised version (e.g., XZ Utils 5.4.6 Steady).
Discovered this posting intriguing? Abide by us on Twitter and LinkedIn to read far more exceptional material we put up.
Some parts of this report are sourced from:
thehackernews.com


 Dormakaba Locks Used in Millions of Hotel Rooms Could Be Cracked in Seconds
Dormakaba Locks Used in Millions of Hotel Rooms Could Be Cracked in Seconds