A suspected Vietnamese-origin threat actor has been noticed targeting victims in numerous Asian and Southeast Asian countries with malware built to harvest valuable information considering that at least Could 2023.
Cisco Talos is tracking the cluster less than the name CoralRaider, describing it as monetarily inspired. Targets of the campaign contain India, China, South Korea, Bangladesh, Pakistan, Indonesia, and Vietnam.
“This team focuses on stealing victims’ credentials, economical info, and social media accounts, including business enterprise and ad accounts,” security scientists Chetan Raghuprasad and Joey Chen stated. “They use RotBot, a personalized variant of Quasar RAT, and XClient stealer as payloads.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Other commodity malware employed by the group comprises a mix of remote obtain trojans and data stealers these kinds of as AsyncRAT, NetSupport RAT, and Rhadamanthys.

The focusing on of business and advertisement accounts has been of particular emphasis for attackers functioning out of Vietnam, with many stealer malware families like Ducktail, NodeStealer, and VietCredCare deployed to take control of the accounts for even more monetization.
The modus operandi involves the use of Telegram to exfiltrate the stolen information from target equipment, which is then traded in underground markets to crank out illicit revenues.
“CoralRaider operators are dependent in Vietnam, centered on the actor messages in their Telegram C2 bot channels and language choice in naming their bots, PDB strings, and other Vietnamese words hard-coded in their payload binaries,” the researchers mentioned.
Attack chains start with a Windows shortcut file (LNK), though there is now no clear explanation as to how these information are distributed to the targets.
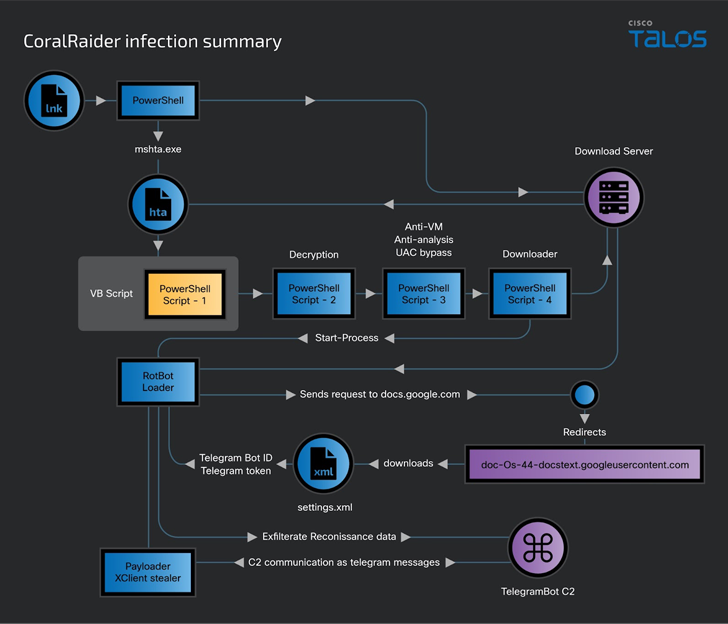
Should the LNK file be opened, an HTML application (HTA) file is downloaded and executed from an attacker-managed obtain server, which, in switch, operates an embedded Visual Essential script.
The script, for its component, decrypts and sequentially executes 3 other PowerShell scripts that are liable for accomplishing anti-VM and anti-assessment checks, circumventing Windows User Obtain Command (UAC), disabling Windows and software notifications, and downloading and running RotBot.
RotBot is configured to call a Telegram bot and retrieve the XClient stealer malware and execute it in memory, finally facilitating the theft of cookies, qualifications, and economical details from web browsers like Brave, Cốc Cốc, Google Chrome, Microsoft Edge, Mozilla Firefox, and Opera Discord and Telegram info and screenshots.
XClient is also engineered to siphon knowledge from victims’ Facebook, Instagram, TikTok and YouTube accounts, gathering information about the payment methods and permissions connected with their Facebook business enterprise and advertisements accounts.
“RotBot is a variant of the Quasar RAT client that the risk actor has custom-made and compiled for this marketing campaign,” the researchers stated. “[XClient] has intensive information and facts-thieving capability via its plugin module and several modules for performing remote administrative duties.”

The improvement comes as Bitdefender disclosed particulars of a malvertising campaign on Fb that is taking edge of the excitement bordering generative AI instruments to push an assortment of data stealers like Rilide, Vidar, IceRAT, and a new entrant regarded as Nova Stealer.
The starting off stage of the attack is the danger actor using more than an existing Fb account and modifying its physical appearance to mimic perfectly-recognised AI equipment from Google, OpenAI, and Midjourney, and growing their get to by operating sponsored adverts on the system.
A single is imposter webpage masquerading as Midjourney experienced 1.2 million followers prior to it was taken down on March 8, 2023. The risk actors taking care of the web site were being predominantly from Vietnam, the U.S., Indonesia, the U.K., and Australia, amongst some others.
“The malvertising campaigns have tremendous access by way of Meta’s sponsored advertisement procedure and have actively been targeting European end users from Germany, Poland, Italy, France, Belgium, Spain, the Netherlands, Romania, Sweden, and in other places,” the Romanian cybersecurity business mentioned.
Discovered this posting intriguing? Follow us on Twitter and LinkedIn to study extra distinctive articles we post.
Some parts of this post are sourced from:
thehackernews.com


 New Phishing Campaign Targets Oil & Gas with Evolved Data-Stealing Malware
New Phishing Campaign Targets Oil & Gas with Evolved Data-Stealing Malware