A Vietnamese risk actor has been attributed as driving a “malverposting” marketing campaign on social media platforms to infect more than 500,000 devices around the world more than the past 3 months to supply variants of details stealers these kinds of as S1deload Stealer and SYS01stealer.
Malverposting refers to the use of promoted social media posts on products and services like Facebook and Twitter to mass propagate destructive software program and other security threats. The plan is to achieve a broader audience by spending for adverts to “amplify” their posts.
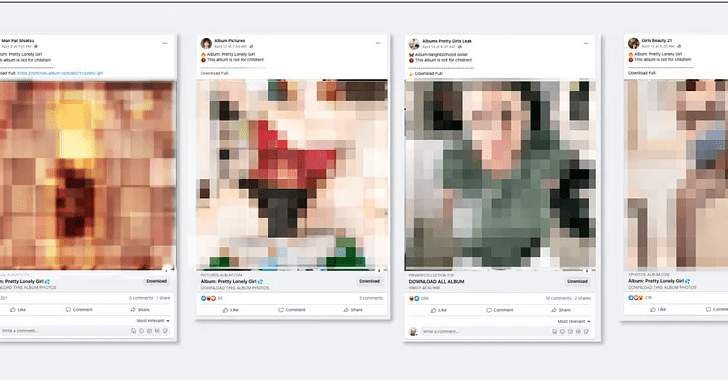
According to Guardio Labs, these kinds of attacks start with the adversary making new organization profiles and hijacking currently well known accounts to provide advertisements that assert to offer you free grownup-rated picture album downloads.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Inside of these ZIP archive documents are purported illustrations or photos that are really executable documents, which, when clicked, activate the infection chain and in the long run deploy the stealer malware to siphon session cookies, account details, and other info.
The attack chain is really successful as it produces a “vicious circle” wherein the facts plundered making use of the stealer is utilised to make an at any time-expanding army of hijacked Facebook bot accounts that are then employed to drive much more sponsored posts, proficiently scaling the scheme further more.
To slip beneath the radar of Fb, the menace actor has been located to go off the recently created organization profile internet pages as photographer accounts. A greater part of the bacterial infections have been documented in Australia, Canada, India, the U.K., and the U.S.
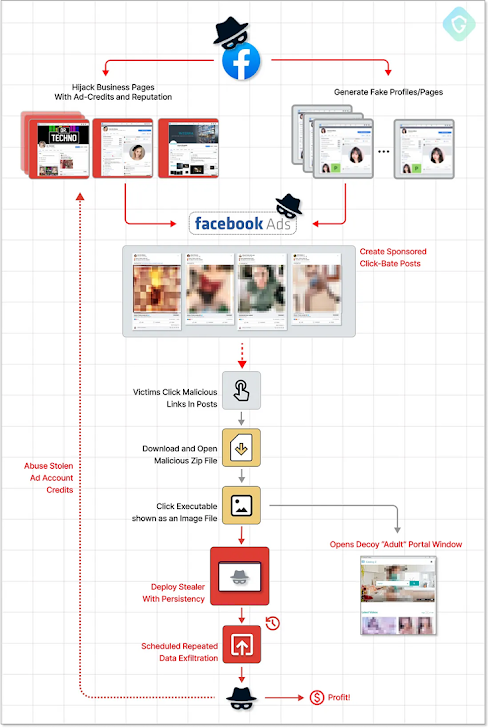
The strategy by means of which the PHP-dependent stealer is deployed is claimed to be continuously evolving to integrate much more detection evasion features, suggesting that the danger actor powering the campaign is actively refining and retooling their techniques in response to general public disclosures.
“The destructive payload is really complex and varies all the time, introducing new evasive techniques,” Guardio Labs security researcher Nati Tal reported.
Upcoming WEBINARLearn to Halt Ransomware with True-Time Protection
Sign up for our webinar and study how to halt ransomware attacks in their tracks with genuine-time MFA and assistance account security.
Preserve My Seat!
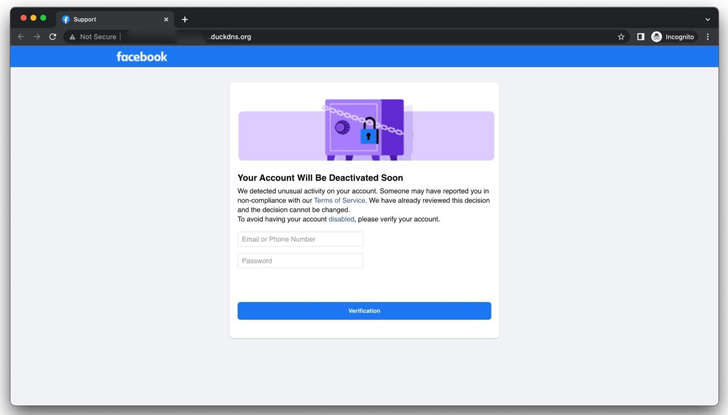
The results come as Group-IB exposed aspects of an ongoing phishing operation that is aimed at Facebook end users by tricking them to enter their qualifications on phony copycat websites developed to steal their account qualifications and get over the profiles.
In a connected enhancement, Malwarebytes unearthed a malvertising marketing campaign that has been discovered to trick users searching for video games and food stuff recipes on Google to provide malicious advertisements that redirect them to phony internet websites designed on Weebly with the aim of conducting a tech aid fraud.
Uncovered this short article appealing? Observe us on Twitter and LinkedIn to read additional exclusive content material we article.
Some components of this short article are sourced from:
thehackernews.com

 APT28 Targets Ukrainian Government Entities with Fake “Windows Update” Emails
APT28 Targets Ukrainian Government Entities with Fake “Windows Update” Emails