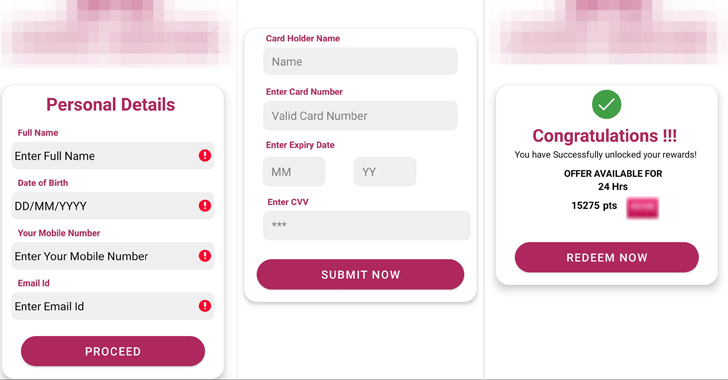
Cybersecurity scientists are warning of “massive phishing strategies” that distribute five unique malware focusing on banking buyers in India.
“The lender consumers focused incorporate account subscribers of seven banking companies, which includes some of the most very well-known banking companies located in the country and possibly impacting millions of buyers,” Pattern Micro claimed in a report released this 7 days.
Some of the qualified banking companies include things like Axis Financial institution, ICICI Bank, and the Condition Bank of India (SBI), between other individuals.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The infection chains all have a frequent entry position in that they count on SMS messages containing a phishing backlink that urge potential victims to enter their private specifics and credit history card details to supposedly get a tax refund or acquire credit card reward details.
The smishing attacks, which supply Elibomi, FakeReward, AxBanker, IcRAT, and IcSpy, are just the most recent in a sequence of related rewards-themed malware strategies that have been documented by Microsoft, Cyble, and K7 Labs in excess of the past calendar year.
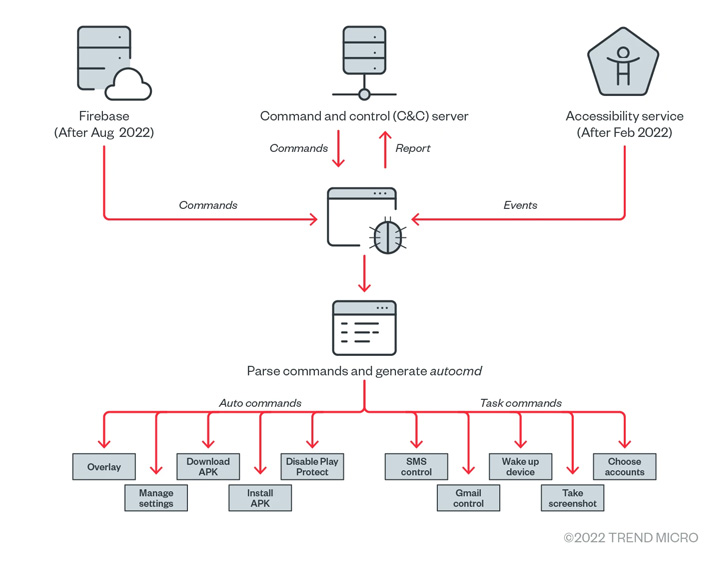
Elibomi, very first documented by McAfee in September 2021, is engineered to steal individual data, take screenshots, and even seize the lock display screen code or pattern by abusing Android’s accessibility API permissions, enabling it to seize command of the compromised devices.
The mobile malware has gone through many revisions, with a new variant of Elibomi termed Drinik observed impersonating the Money Tax Section of India to concentrate on consumers of 18 unique banking companies.
“Elibomi implements an overlay by including a view to the present-day window as an evasion method from end users, instead of getting an overlay on other apps such as financial institution applications to steal users’ qualifications,” the scientists reported.
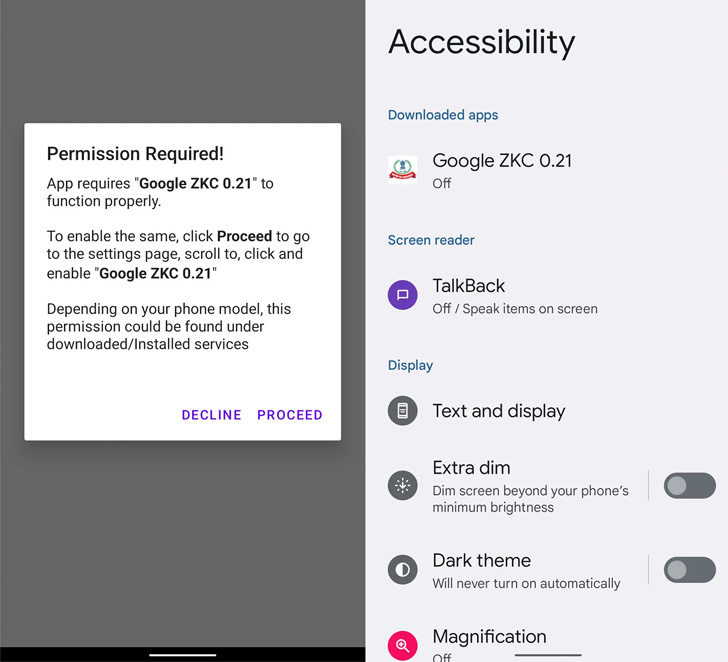
In a equivalent vein, the FakeReward and AxBanker banking trojans, once mounted, prompt the victim to grant it permissions to access SMSes and notifications, which are then leveraged to exfiltrate incoming SMS messages. AxBanker additional shows bogus web pages to siphon credit history card information.

The apps by themselves are delivered by phishing sites with area names related to that of their authentic counterparts, in addition to reusing the model logos to boost the likelihood of a successful attack and trick the consumer into downloading the destructive application to get “quick reward details.”
The similarity in stolen information and phishing themes notwithstanding, Trend Micro reported there is no concrete evidence tying all these malware family members to a solitary menace actor.
“Though no other shoppers outside India have been targeted by these malware family members, phishing campaigns in the state have considerably enhanced and are significantly becoming adept at detection evasion,” Pattern Micro pointed out.
“A person achievable motive for this uptick is the developing number of new menace actors coming into the India underground market, bringing with them worthwhile business enterprise types, and interacting with other malicious players to master, trade thoughts from, and create connections.”
Uncovered this posting exciting? Comply with THN on Facebook, Twitter and LinkedIn to study extra exclusive material we put up.
Some pieces of this posting are sourced from:
thehackernews.com