Cybersecurity scientists are contacting attention to a zero-day flaw in Microsoft Office environment that could be abused to achieve arbitrary code execution on impacted Windows systems.
The vulnerability came to light right after an independent cybersecurity research staff acknowledged as nao_sec uncovered a Word document (“05-2022-0438.doc”) that was uploaded to VirusTotal from an IP handle in Belarus.
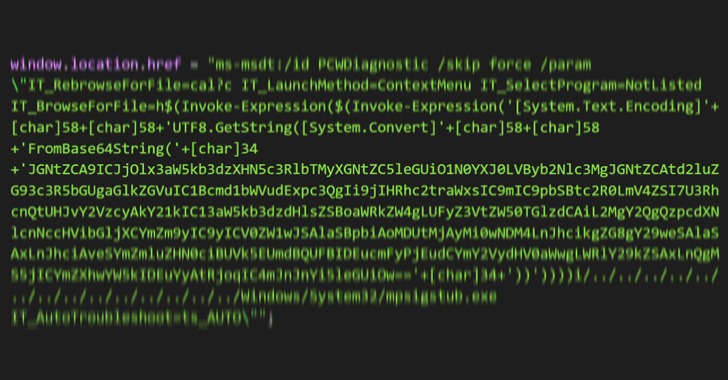
“It employs Word’s exterior website link to load the HTML and then utilizes the ‘ms-msdt’ plan to execute PowerShell code,” the scientists famous in a series of tweets final 7 days.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

According to security researcher Kevin Beaumont, who dubbed the flaw “Follina,” the maldoc leverages Word’s distant template feature to fetch an HTML file from a server, which then makes use of the “ms-msdt://” URI scheme to operate the malicious payload.
MSDT is brief for Microsoft Help Diagnostics Instrument, a utility that’s utilized to troubleshoot and gather diagnostic facts for assessment by assistance gurus to solve a challenge.
“There is certainly a great deal going on here, but the initial trouble is Microsoft Phrase is executing the code through msdt (a guidance tool) even if macros are disabled,” Beaumont stated.

“Safeguarded Look at does kick in, whilst if you improve the doc to RTF type, it runs without the need of even opening the document (through the preview tab in Explorer) enable by itself Shielded Watch,” the researcher included.
Numerous Microsoft Office variations, together with Office environment, Business 2016, and Workplace 2021, are claimed to be affected, despite the fact that other variations are envisioned to be susceptible as perfectly.
What is actually a lot more, Richard Warren of NCC Team managed to show an exploit on Business Professional Pro with April 2022 running on an up-to-day Windows 11 equipment with the preview pane enabled.
“Microsoft are going to need to patch it throughout all the distinct solution choices, and security distributors will need strong detection and blocking,” Beaumont said. We have reached out to Microsoft for remark, and we’ll update the tale at the time we hear back.
Uncovered this posting appealing? Follow THN on Fb, Twitter and LinkedIn to study additional unique content material we put up.
Some parts of this post are sourced from:
thehackernews.com

 Mobile Threat Volumes Slump 58% in a Year
Mobile Threat Volumes Slump 58% in a Year