It’s not a new principle that Place of work 365, Salesforce, Slack, Google Workspace or Zoom, and so forth., are remarkable for enabling the hybrid workforce and hyper-productiveness in organizations nowadays. Nonetheless, there are three principal problems that have arisen stemming from this evolution: (1) While SaaS applications contain a host of indigenous security settings, they have to have to be hardened by the security staff of the corporation. (2) Workforce are granting 3rd party application access to main SaaS applications that pose opportunity threats to the organization. (3) These SaaS applications are accessed by various devices without having their gadget hygiene score even staying checked.
1 — Misconfiguration Administration
It is not an easy job to have just about every app placing properly configured — at all moments. The problem lies within just how burdensome this accountability is — each and every app has tens or hundreds of security options to configure, in addition to countless numbers of user roles and permission in a usual organization, compounded by the several compliance business expectations and frameworks that businesses strive to stick to.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The complexity of securing SaaS applications is only increased by the truth that normally the SaaS app operator sits outside the house the security crew, in the section that most makes use of the application (think Income has CRM app, Advertising and marketing has automation application) — and they are untrained and not concentrated on the security upkeep of the application. It all quantities to just how burdensome and unrealistic it is to count on security teams to be ready to continue to be in management of the organization’s SaaS stack.
2 — 3rd Party App Access
OAuth 2. has significantly simplified authentication and authorization and gives a great-grained delegation of access rights. Represented in the sort of scopes, an software asks for the user’s authorization for particular permissions. An app can ask for 1 or far more scopes. By the approval of the scopes, the consumer grants these apps permissions to execute code to conduct logic guiding the scenes within their surroundings. These apps can be harmless or as threatening as an executable file.
When it arrives to area devices and executable documents, companies currently have handle created-in that allows security groups to block problematic systems and information. It requires to be the similar when it arrives to SaaS apps.
3 — Gadget-to-SaaS-Consumer Posture
From the 1st entry by means of to the product posture, security teams will need to be ready to discover and handle the dangers coming from SaaS people and their involved equipment. A unit with a low cleanliness score poses a high risk relying on which applications this personnel is employing. In the scenario of a extremely privileged user, an unsecured machine can pose an even better degree of risk for an corporation. The security staff wants the ability to correlate SaaS application end users, their roles, and permissions with their associated devices’ compliance and integrity ranges. This close-to-conclude technique enables a holistic zero-have confidence in technique to SaaS security that is only now coming into the picture.
SaaS Security Posture Administration Handles the SaaS Stack Worries
That’s why Gartner named SaaS Security Posture Administration (SSPM) a Have to HAVE option to continually evaluate security dangers and control the SaaS applications’ security posture in the “4 Ought to-Have Technologies That Designed the Gartner Hoopla Cycle for Cloud Security, 2021.” Other cloud answers do not supply preventative protection. For example, a CASB solution is party-pushed CASB will inform the firm to a SaaS leak or breach only at the time it has happened.
An SSPM alternative, like Adaptive Protect, comes into participate in to allow security groups to detect, review, and prioritize misconfigurations as very well as deliver visibility to 3rd party apps with entry to their core applications and Device-to-SaaS-Consumer posture administration.
Simply click below to schedule a 15-minute demo of Adaptive Shield’s SSPM alternative.
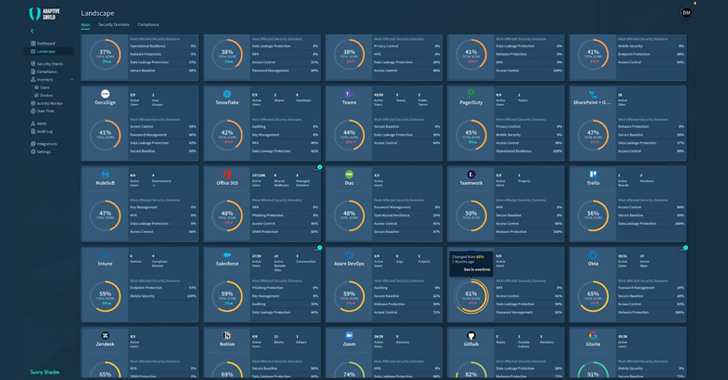
Adaptive Protect lets you filter and slice the knowledge by application, domain, and compliance frameworks.
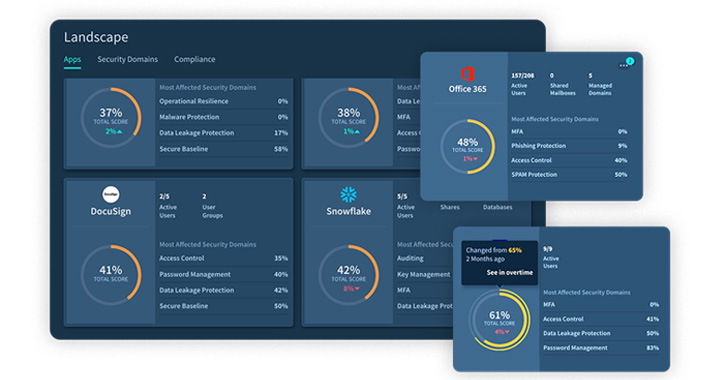
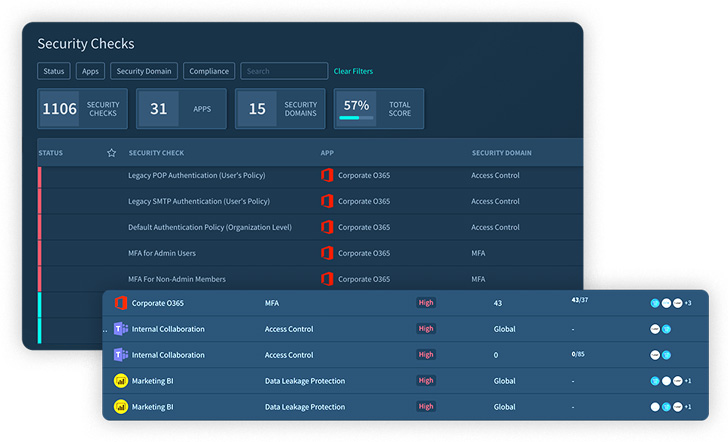
The core of the resolution is the specific and granular security checks currently being continuously carried out throughout the SaaS stack, when security teams can address misconfigurations promptly or create a ticket that integrates with any ticketing process:
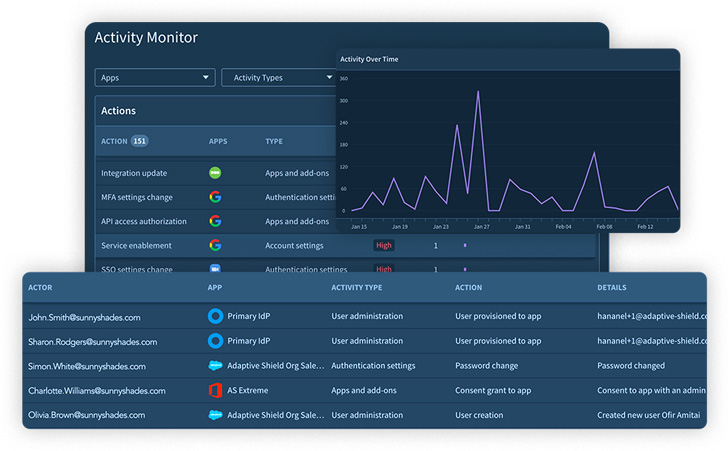
As a result of the Activity Checking aspect, Adaptive Shield monitors the things to do of privileged buyers:
Simply click listed here to timetable a 15-moment demo to see all capabilities and functionalities.
Observed this write-up intriguing? Abide by THN on Fb, Twitter and LinkedIn to browse extra distinctive content material we publish.
Some components of this post are sourced from:
thehackernews.com

 An analysis of the European cyberthreat landscape
An analysis of the European cyberthreat landscape