When intended for advantage and effective interaction, email automobile-forwarding regulations can inadvertently guide to the unauthorized dissemination of delicate details to exterior entities, putting confidential info at risk of publicity to unauthorized functions. Wing Security (Wing), a SaaS security organization, declared yesterday that their SaaS shadow IT discovery strategies now incorporate a remedy that solves for automobile-email forwarding as well. When Wing’s shadow IT option is provided as a no cost resource that can be onboarded and applied as a self-assistance, users keen to upgrade will be capable to love the company’s new Gmail and Outlook integrations, which broaden the company’s discovery capabilities and increase their info security characteristics.
The challenges of email vehicle-forwarding regulations
Car-forwarding e-mail is a fantastic way to save time on repetitive responsibilities and are for that reason really well-known amid personnel who regularly collaborate and share details with external business enterprise partners. Risk examples include things like:

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
- Automation indicates no one particular is examining for delicate or personal facts. Email messages with a sure phrase blend in the title, or a particular sender, will instantly be forwarded to an external entity devoid of any oversight. This can lead to PII knowledge leakage, delicate facts leakage and regulatory violations that can compromise an organization’s compliance.
- Auto-forwarding can also reveal a probable insider risk. A disgruntled worker may well automobile-ahead selected e-mails to competition. It can also be as popular as an personnel who plans to go away the firm and wants to manage accessibility to their operate after they go away – vehicle-forwarding e-mails to their private email account.
- Destructive actors might use this as an entry point. Negative actors can use these email forwarding principles to exfiltrate knowledge just after a effective attack, or as a implies to unfold phishing campaigns within just businesses.
 Screenshot from Wing’s system, automobile-forwarding issues located in gmail and Outlook
Screenshot from Wing’s system, automobile-forwarding issues located in gmail and Outlook
What is the relationship involving SaaS Security and email Security?
For quite a few causes, it is critical for corporations to uncover SaaS Shadow IT applications. Shadow IT refers to the unauthorized use of IT units in just an firm, typically for the sake of ease or effectiveness, without the need of the explicit approval of the IT section. There are some SaaS programs that may well pose major dangers to the organization’s security, compliance, and total efficiency:
- Security Risks: SaaS purposes are part of the contemporary provide chain, and as these kinds of they ought to go through appropriate seller risk assessments and user access testimonials prior to connecting them to firm data. With Shadow IT, breached programs, non-compliant purposes or destructive purposes go unnoticed.
- Compliance Issues: Numerous industries have demanding regulatory prerequisites that ought to be adhered to, particularly concerning info privacy and protection. Utilizing unauthorized purposes can end result in non-compliance, foremost to legal penalties, fines, and harm to the organization’s name.
- Economical Implications: Uncontrolled proliferation of Shadow IT apps can guide to needless expenditure. Corporations may well conclude up paying out for redundant products and services or duplicate accounts, foremost to negligent shelling out and money waste.
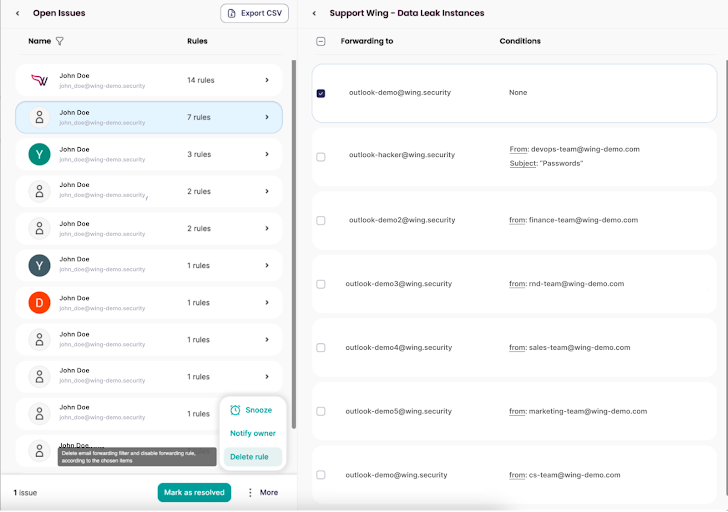 Wing’s merchandise illustration – dangerous email forwarding regulations
Wing’s merchandise illustration – dangerous email forwarding regulations
Wing’s SaaS discovery entails the systematic identification, categorization, and investigation of an organization’s SaaS use to mitigate shadow IT challenges. The organization delivers three distinctive and non-intrusive discovery methods: Connecting to organizations’ big SaaS applications (e.g., Google Drive, Salesforce, Slack, and many others) to determine linked purposes, scanning endpoints for SaaS signature hits and cross-checking them with Wing’s considerable SaaS databases of over 280,000 SaaS records. Their 3rd and freshly released capability will involve connecting to enterprise e-mails and conducting scans to detect crystal clear indications of SaaS usage. Wing emphasizes that recognizing is just the very first action in fixing and therefore presents buyers the indicates to remediate and eliminate risky shares right within their platform.
Identified this posting exciting? Comply with us on Twitter and LinkedIn to read additional exclusive content we submit.
Some sections of this short article are sourced from:
thehackernews.com


 MuddyC2Go: New C2 Framework Iranian Hackers Using Against Israel
MuddyC2Go: New C2 Framework Iranian Hackers Using Against Israel