Like antivirus program, vulnerability scans rely on a databases of recognised weaknesses.
That is why sites like VirusTotal exist, to give cyber practitioners a possibility to see regardless of whether a malware sample is detected by several virus scanning engines, but this strategy hasn’t existed in the vulnerability management area.
The advantages of applying numerous scanning engines
Commonly talking, vulnerability scanners intention to make checks for as quite a few vulnerabilities as probable. On the other hand, the amount of vulnerabilities found out yr on year is now so significant, reaching almost 30,000 a yr, or 80 a working day, that it is really extremely hard for a single scanning motor to maintain up with them all.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
As a outcome, even the incredibly finest, field-leading main scanners will struggle to test for each and every recognized vulnerability out there, and often they will favour selected sets of application identified to be utilised by their prospects.
For instance, Intruder’s analysis from early 2023 which in comparison Tenable’s Nessus and OpenVAS showed substantial discrepancies in protection in between scanners, with a person being frequently much better in professional program, and the other favouring open supply:
“Tenable checks for 12,015 CVEs which OpenVAS does not examine for and OpenVAS checks for 6,749 CVEs which Tenable does not check out for.”

Scanning engine suppliers also just take other factors into consideration, like irrespective of whether a vulnerability has been exploited in the wild, or regardless of whether it really is in program goods which are quite broadly used. But even although your decided on scanner may perhaps be creating smart conclusions on which vulnerabilities to compose checks for there may possibly however be gaps in protection for your estate.
So it’s a severe fact that just one day you may well uncover out that you’ve got been compromised through an attack vector which your vulnerability scanner only isn’t going to have a check out for.
This raises sizeable inquiries for those searching to guard their digital estates, not only which scanner they need to pick. But regardless of whether a single scanner is even plenty of?
The multi-scanning motor technique
It is really apparent that getting various complementary scanners would increase protection by acquiring extra vulnerabilities, and exploring extra about what your attack floor appears to be like. But running numerous scanning techniques would be also considerably for most organisations to afford to pay for, both of those in finances and time constraints.
That is why the group at Intruder, a major Attack Surface Administration vendor, determined from the begin to incorporate multiple scanning engines, presenting consumers the widest breadth of checks, while streamlining finances and time constraints by giving them in a one platform.
Most recently, Intruder has included Nuclei to its suite of vulnerability scanning engines, enhancing its means to take care of and safe attack surfaces.
With over 3,000 more checks in this first launch, Intruder can supply much broader and deeper protection and discovery capabilities that can’t be matched by utilizing a single vulnerability scanner by itself.
What is Nuclei?
Nuclei is an open up-resource vulnerability scanning motor, identical to OpenVAS, which is rapidly, extensible, and addresses a wide range of weaknesses. It is grow to be ever more well known with bug bounty hunters, penetration testers and scientists who want to deliver repeatable checks for severe weaknesses.
These experts, doing the job with the Nuclei development staff at ProjectDiscovery, mix their information and insights about cutting-edge weaknesses to produce checks very quick – which helps make scanning as shortly as feasible immediately after a vulnerability is discovered.
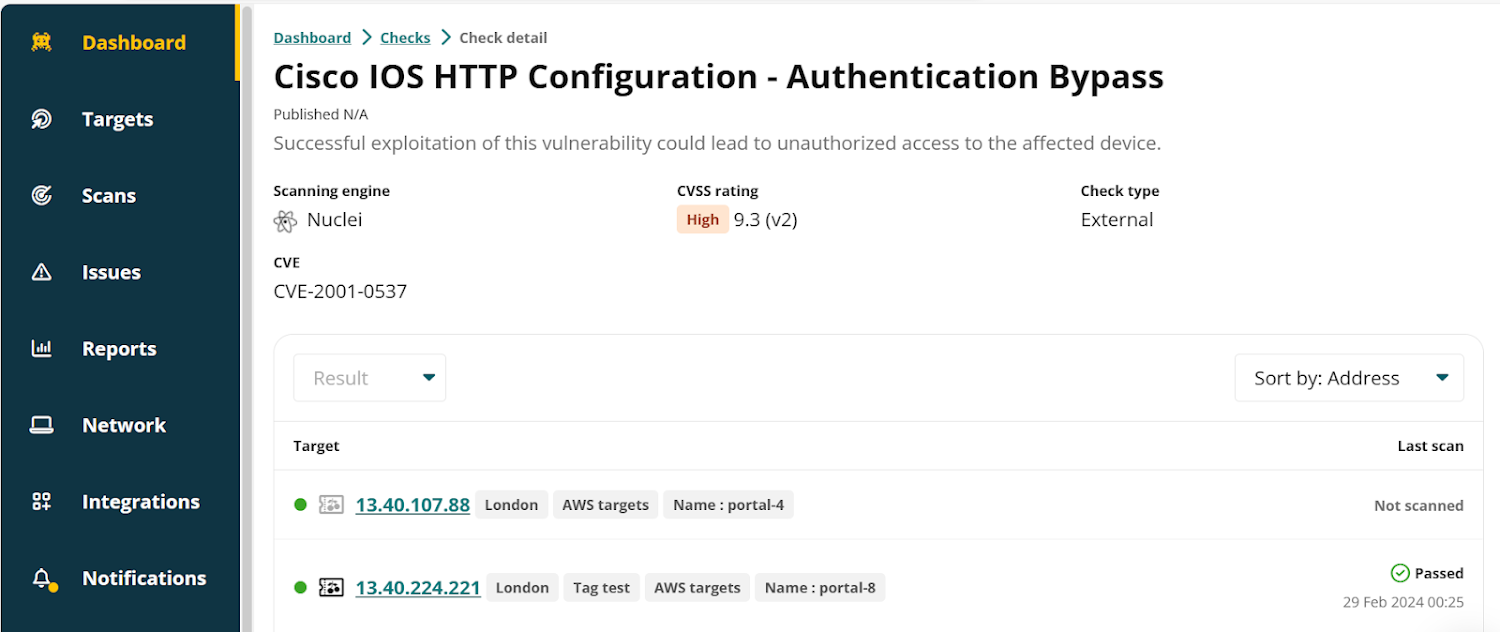 An instance of a Nuclei check out in the Intruder platform
An instance of a Nuclei check out in the Intruder platform
What does Nuclei add to Intruder?
By integrating Nuclei as a scanning motor, Intruder further boosts its vulnerability administration system capabilities to check and protected attack surfaces much more correctly.
This contains expanded detection of exposures like login panels that ought to not be exposed to the internet, and growing the range of checks for known vulnerabilities in usually uncovered services.
Nuclei augments Intruder’s present scanning engines, these types of as Tenable and OpenVAS, by delivering a deeper and broader check out of your attack area, hence enabling superior defense by uncovering hazards that would keep on being undetected by a one scanning engine.
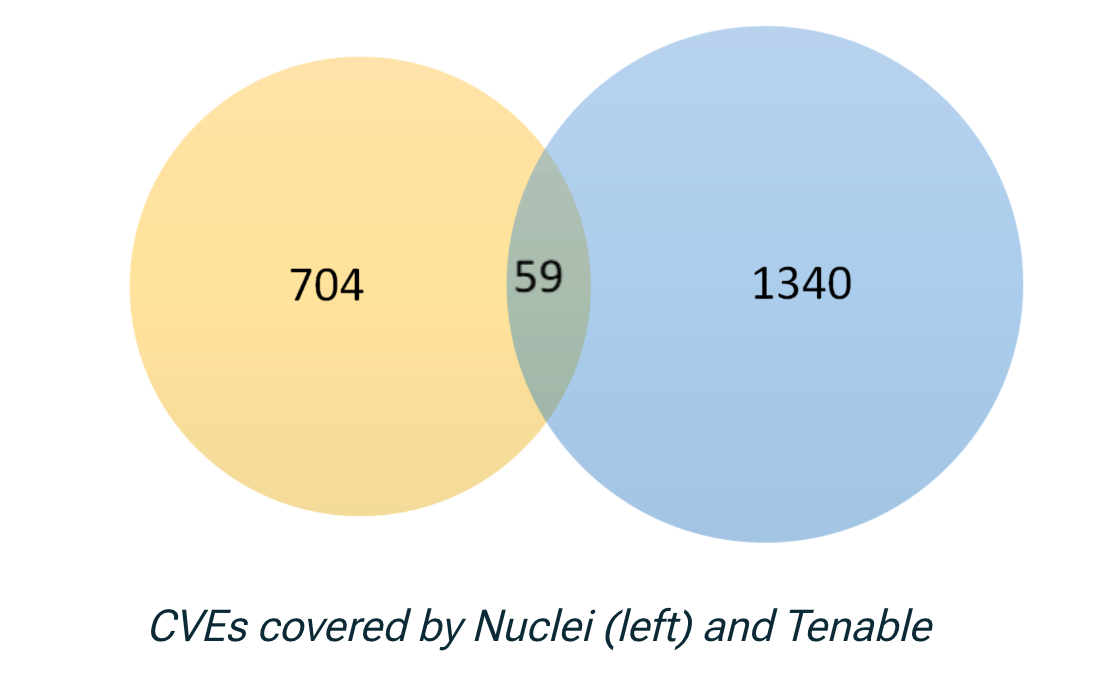
Visualize and decrease your exposure with Intruder
The measurement of your attack floor, and how very well it is managed, is intently tied to your risk of opportunistic attackers exploiting your units. The a lot less you expose, and the a lot more hardened the expert services you expose are, the more durable it is for an attacker to exploit a weakness.
You can decrease your attack surface area by consistently checking for modifications with an automatic vulnerability administration tool like Intruder.
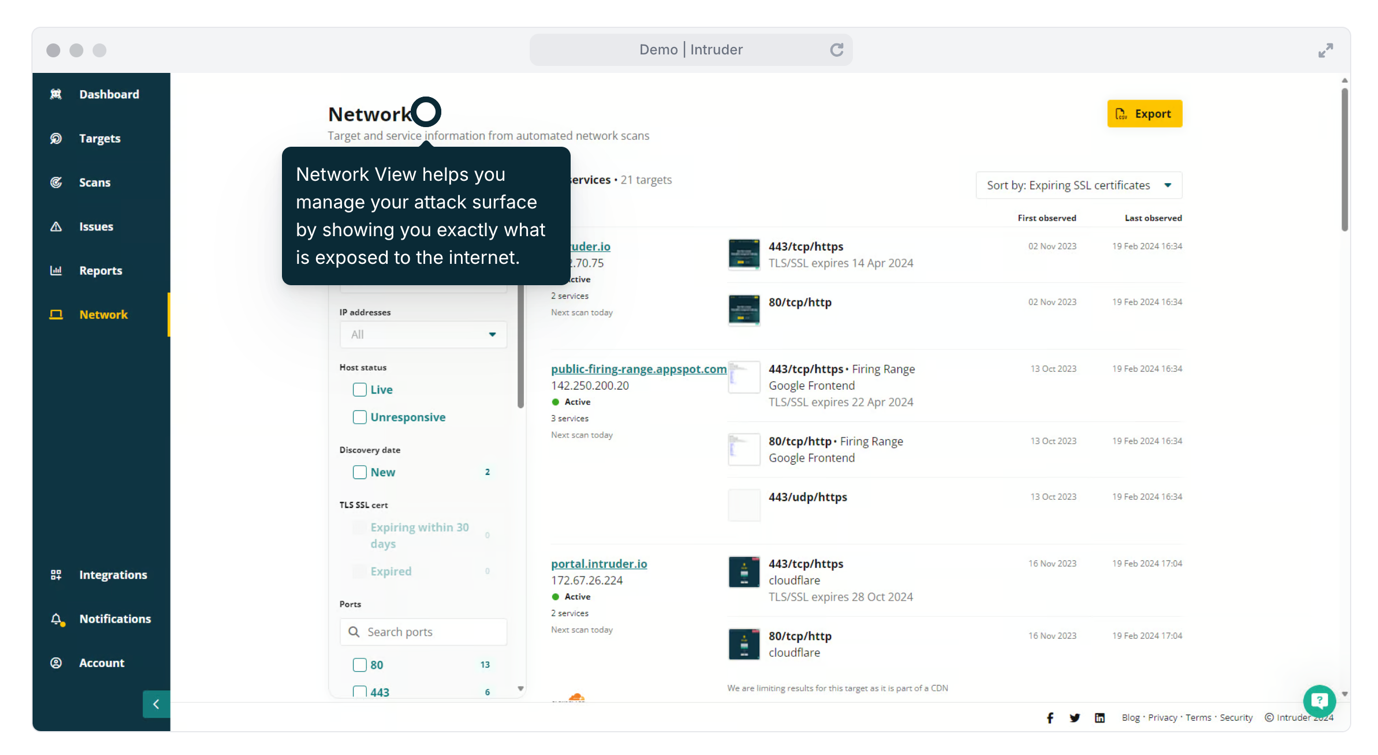 A screenshot of Intruder’s attack surface management dashboard.
A screenshot of Intruder’s attack surface management dashboard.
Intruder’s platform permits you to:
- Learn property: when new cloud services are spun up and uncovered to the internet, Intruder kicks off a scan to uncover any vulnerabilities so you can repair them a lot quicker.
- Know what’s exposed: get entire visibility of your network perimeter, keep track of lively and unresponsive targets, establish improvements, check expiring certificates, and see any ports, companies or protocols that should not be exposed to the internet.
- Detect much more: Intruder works by using many scanners to recognize vulnerabilities and exposures throughout your attack floor giving you the biggest visibility.
- Target on the significant issues: see success prioritized primarily based on context, so you can aim on the most pressing troubles devoid of throwing away time sifting via the noise.
Located this short article appealing? This write-up is a contributed piece from one of our valued companions. Adhere to us on Twitter and LinkedIn to study extra exceptional material we post.
Some parts of this post are sourced from:
thehackernews.com


 Dropbox Discloses Breach of Digital Signature Service Affecting All Users
Dropbox Discloses Breach of Digital Signature Service Affecting All Users