The innovative persistent danger (APT) actor recognised as Winter season Vivern is now concentrating on officials in Europe and the U.S. as element of an ongoing cyber espionage marketing campaign.
“TA473 due to the fact at least February 2023 has continuously leveraged an unpatched Zimbra vulnerability in publicly facing webmail portals that allows them to obtain accessibility to the email mailboxes of govt entities in Europe,” Proofpoint explained in a new report.
The business security agency is monitoring the activity beneath its very own moniker TA473 (aka UAC-0114), describing it as an adversarial crew whose functions align with that of Russian and Belarussian geopolitical aims.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
What it lacks in sophistication, it would make up for in persistence. In new months, the group has been joined to attacks focusing on condition authorities of Ukraine and Poland as very well as governing administration officials in India, Lithuania, Slovakia, and the Vatican.
The NATO-linked intrusion wave entails the exploitation of CVE-2022-27926 (CVSS score: 6.1), a now-patched medium-severity security flaw in Zimbra Collaboration that could help unauthenticated attackers to execute arbitrary JavaScript or HTML code.
This also requires utilizing scanning instruments like Acunetix to recognize unpatched webmail portals belonging to specific companies with the objective of sending phishing email beneath the guise of benign govt companies.
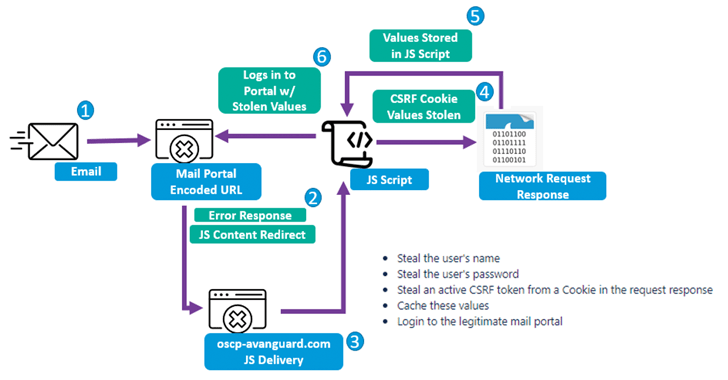
The messages arrive with booby-trapped URLs that exploit the cross-web site scripting (XSS) flaw in Zimbra to execute customized Foundation64-encoded JavaScript payloads within the victims’ webmail portals to exfiltrate usernames, passwords, and obtain tokens.
It is truly worth noting that just about every JavaScript payload is customized to the specific webmail portal, indicating that the threat actor is prepared to devote time and sources to lower the chance of detection.
“TA473’s persistent approach to vulnerability scanning and exploitation of unpatched vulnerabilities impacting publicly dealing with webmail portals is a important factor in this actor’s achievements,” Proofpoint mentioned.
“The group’s concentrate on sustained reconnaissance and painstaking examine of publicly uncovered webmail portals to reverse engineer JavaScript capable of stealing usernames, passwords, and CSRF tokens demonstrates its investment decision in compromising specific targets.”
The results appear amid revelations that at minimum three Russian intelligence organizations, which includes FSB, GRU (linked to Sandworm), and SVR (linked to APT29), probably use application and hacking instruments developed by a Moscow-based IT contractor named NTC Vulkan.
THN WEBINARBecome an Incident Reaction Pro!
Unlock the insider secrets to bulletproof incident response – Learn the 6-Stage approach with Asaf Perlman, Cynet’s IR Chief!
Will not Miss out on Out – Save Your Seat!
This contains frameworks like Scan (to facilitate substantial-scale info selection), Amesit (to conduct details operations and manipulate general public belief), and Krystal-2B (to simulate coordinated IO/OT attacks against rail and pipeline handle units).
“Krystal-2B is a teaching platform that simulates OT attacks from distinctive kinds of OT environments in coordination with some IO components by leveraging Amesit ‘for the purpose of disruption,'” Google-owned Mandiant explained.
“The contracted projects from NTC Vulkan provide perception into the investment of Russian intelligence providers into acquiring abilities to deploy extra efficient operations within just the commencing of the attack lifecycle, a piece of functions generally hidden from our view,” the danger intelligence company claimed.
Uncovered this posting interesting? Comply with us on Twitter and LinkedIn to go through more unique content we put up.
Some sections of this report are sourced from:
thehackernews.com

 MongoDB CISO: Don’t be afraid to simplify important issues for executives
MongoDB CISO: Don’t be afraid to simplify important issues for executives