A critical security flaw in the Bricks theme for WordPress is becoming actively exploited by risk actors to operate arbitrary PHP code on inclined installations.
The flaw, tracked as CVE-2024-25600 (CVSS rating: 9.8), allows unauthenticated attackers to accomplish distant code execution. It impacts all variations of the Bricks up to and which include 1.9.6.
It has been dealt with by the theme developers in variation 1.9.6.1 produced on February 13, 2024, simply days immediately after WordPress security company Snicco reported the flaw on February 10.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
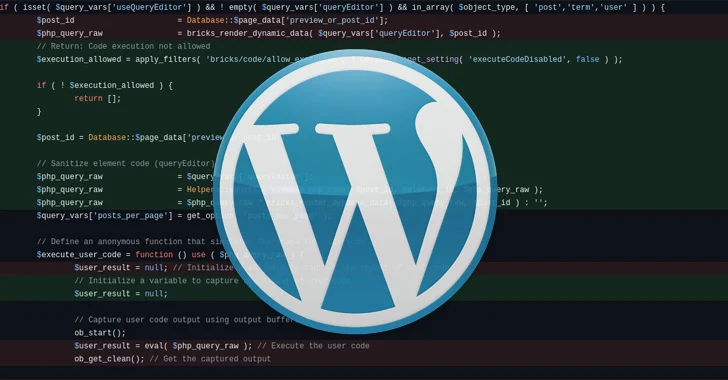
Though a evidence-of-thought (PoC) exploit has not been introduced, specialized specifics have been introduced by both equally Snicco and Patchstack, noting that the fundamental vulnerable code exists in the prepare_question_vars_from_configurations() functionality.
Specially, it concerns the use of security tokens referred to as “nonces” for verifying permissions, which can then be used to pass arbitrary commands for execution, properly making it possible for a danger actor to seize manage of a targeted internet site.
The nonce worth is publicly available on the frontend of a WordPress website, Patchstack said, adding there are no sufficient purpose checks applied.

“Nonces ought to under no circumstances be relied on for authentication, authorization, or access management,” WordPress cautions in its documentation. “Protect your functions employing present_person_can(), and constantly assume nonces can be compromised.”
WordPress security corporation Wordfence explained it detected above three dozen attack makes an attempt exploiting the flaw as of February 19, 2024. Exploitation makes an attempt are said to have commenced on February 14, a working day immediately after public disclosure.
A majority of the attacks are from the adhering to IP addresses –
- 200.251.23[.]57
- 92.118.170[.]216
- 103.187.5[.]128
- 149.202.55[.]79
- 5.252.118[.]211
- 91.108.240[.]52
Bricks is estimated to have all-around 25,000 at present active installations. People of the plugin are suggested to apply the newest patches to mitigate opportunity threats.
Observed this posting fascinating? Observe us on Twitter and LinkedIn to go through a lot more special written content we article.
Some pieces of this report are sourced from:
thehackernews.com

 Iran and Hezbollah Hackers Launch Attacks to Influence Israel-Hamas Narrative
Iran and Hezbollah Hackers Launch Attacks to Influence Israel-Hamas Narrative