A beforehand undocumented threat actor dubbed YoroTrooper has been targeting federal government, energy, and global corporations throughout Europe as portion of a cyber espionage campaign that has been active due to the fact at least June 2022.
“Information stolen from prosperous compromises include things like qualifications from numerous programs, browser histories and cookies, process information and screenshots,” Cisco Talos researchers Asheer Malhotra and Vitor Ventura stated in a Tuesday investigation.
Outstanding nations focused consist of Azerbaijan, Tajikistan, Kyrgyzstan, Turkmenistan, and other Commonwealth of Unbiased States (CIS) nations.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The risk actor is believed to be Russian-talking owing to the victimology designs and the presence of Cyrillic snippets in some of the implants.
That explained, the YoroTrooper intrusion set has been discovered to exhibit tactical overlaps with the PoetRAT workforce that was documented in 2020 as leveraging coronavirus-themed baits to strike governing administration and strength sectors in Azerbaijan.
YoroTrooper’s facts accumulating goals are realized via a blend of commodity and open up source stealer malware these types of as Ave Maria (aka Warzone RAT), LodaRAT, Meterpreter, and Stink, with the an infection chains employing malicious shortcut data files (LNKs) and decoy files wrapped in ZIP or RAR archives that are propagated by using spear-phishing.
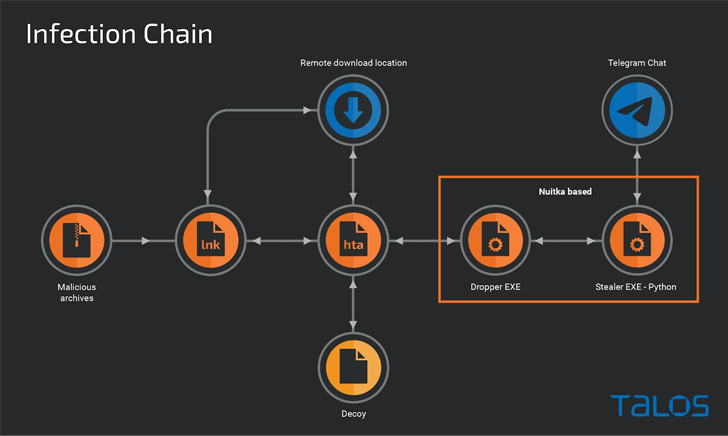
The LNK documents perform as easy downloaders to execute an HTA file retrieved from a distant server, which is then used to show a lure PDF document, although stealthily launching a dropper to supply a custom stealer that uses Telegram as an exfiltration channel.
WEBINARDiscover the Concealed Potential risks of Third-Party SaaS Apps
Are you aware of the threats affiliated with 3rd-party app access to your company’s SaaS apps? Sign up for our webinar to study about the types of permissions becoming granted and how to limit risk.
RESERVE YOUR SEAT
The use of LodaRAT is noteworthy as it suggests that the malware is remaining used by several operators irrespective of its attribution to a further team known as Kasablanka, which has also been observed distributing Ave Maria in new strategies concentrating on Russia.
Other auxiliary resources deployed by YoroTrooper consist of reverse shells and a C-primarily based tailor made keylogger which is able of recording keystrokes and preserving them to a file on disk.
“It is really worth noting that whilst this marketing campaign started with the distribution of commodity malware these types of as Ave Maria and LodaRAT, it has progressed significantly to include Python-centered malware,” the researchers mentioned.
“This highlights an maximize in the efforts the menace actor is putting in, possible derived from profitable breaches throughout the program of the campaign.”
Observed this posting intriguing? Stick to us on Twitter and LinkedIn to examine extra exclusive content we write-up.
Some elements of this write-up are sourced from:
thehackernews.com

 Achieving zero trust for corporate networks
Achieving zero trust for corporate networks