Scientists have shown a new style of fingerprinting procedure that exploits a machine’s graphics processing unit (GPU) as a suggests to track customers across the web persistently.
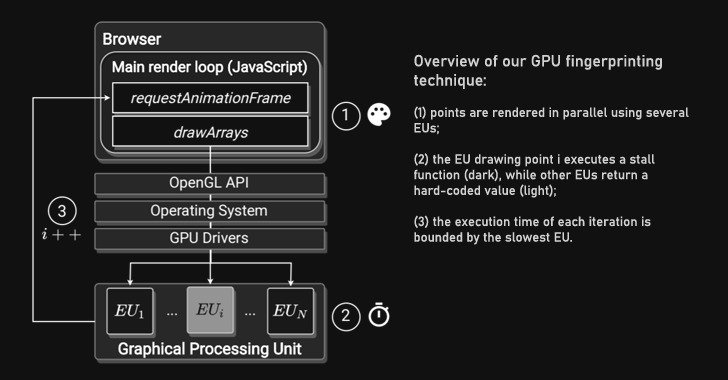
Dubbed DrawnApart, the technique “identifies a system from the special homes of its GPU stack,” researchers from Australia, France, and Israel stated in a new paper,” adding ” versions in pace amongst the various execution units that comprise a GPU can serve as a trustworthy and strong gadget signature, which can be gathered working with unprivileged JavaScript.”
A system fingerprint or machine fingerprint is data that is gathered about the hardware, put in software package, as very well as the web browser and its connected increase-ons from a distant computing unit for the purpose of exclusive identification.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Fingerprints can be a double-edged sword. On the a person hand, a fingerprint algorithm might permit a services provider (e.g., lender) to detect and stop identity theft and credit history card fraud. But it can also be abused to compile long-phrase records of individuals’ searching action for focused promotion.

Browser fingerprinting, in a identical vein, principally depends on stitching collectively crucial pieces of data gleaned from the browser to develop the fingerprint. The characteristics run the gamut, spanning the browser’s version, OS, timezone, display screen, language, checklist of fonts, and even the way the browser renders textual content and graphics.
But browser fingerprints also suffer from a person significant disadvantage in that they can evolve over time, generating it more difficult to keep track of customers for prolonged durations. Which is exactly where DrawnApart will come in.
It is really not only the very first-of-its-form system to examine and weaponize the production discrepancies between equivalent GPUs, but also for reliably using the solution to distinguish concerning equipment with identical hardware and application configurations, properly undermining users’ privacy.
At its core, the proposed tracking method includes measuring the time required to render unique graphics primitives employing the WebGL API, each individual targeting diverse execution models that comprise a GPU, to develop a fingerprint trace which is then fed into a deep finding out network to uniquely identify the particular device that generated it.
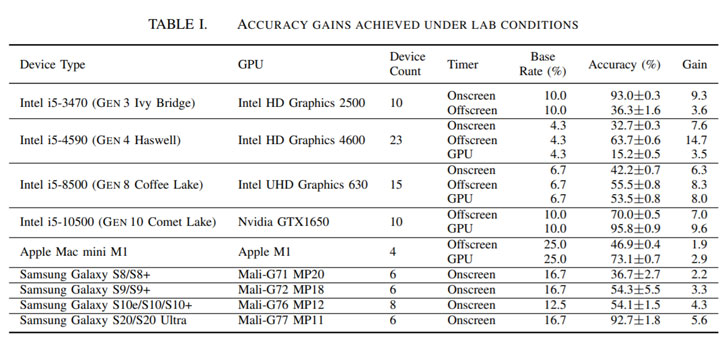
In an analysis setup constituting 88 equipment, such as Windows 10 desktops, Apple Mac mini equipment, and a number of generations of Samsung Galaxy smartphones, the scientists discovered that when employed in conjunction with condition-of-the-art fingerprint linking algorithms like FP-STALKER, DrawnApart prolonged the median ordinary tracking period from 17.5 days to 28 days.
Countermeasures to block the GPU fingerprinting technique range from script blocking to disabling WebGL, and restricting each individual web page to a one execution device, or even turning off components-accelerated rendering — a go the scientists warn could seriously impact usability and responsiveness.
Furthermore, the ongoing improvement into the WebGPU conventional — at present accessible in canary releases of Google Chrome and Mozilla Firefox — is predicted to considerably reduce the time taken to gather the fingerprint, prompting the lecturers to conclude that the “results of accelerated compute APIs on user privacy should be deemed prior to they are enabled globally.”
Observed this write-up exciting? Abide by THN on Fb, Twitter and LinkedIn to examine a lot more exceptional content we submit.
Some sections of this posting are sourced from:
thehackernews.com


 MoD reported seven data incidents to the ICO between 2020 and 2021
MoD reported seven data incidents to the ICO between 2020 and 2021