A never ever-right before-noticed distant obtain trojan dubbed ZuoRAT has been singling out compact place of work/household workplace (SOHO) routers as aspect of a complex campaign focusing on North American and European networks.
The malware “grants the actor the means to pivot into the community network and acquire access to added devices on the LAN by hijacking network communications to retain an undetected foothold,” scientists from Lumen Black Lotus Labs mentioned in a report shared with The Hacker Information.
The stealthy operation, which focused routers from ASUS, Cisco, DrayTek, and NETGEAR, is considered to have commenced in early 2020 during the initial months of the COVID-19 pandemic, successfully remaining less than the radar for around two years.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Customers and remote staff routinely use SOHO routers, but these gadgets are seldom monitored or patched, which will make them 1 of the weakest factors of a network’s perimeter,” the firm’s menace intelligence staff stated.
Original accessibility to the routers is attained by scanning for regarded unpatched flaws to load the remote entry resource, working with it obtain access to the network and fall a upcoming-phase shellcode loader that is employed to provide Cobalt Strike and customized backdoors this sort of as CBeacon and GoBeacon that are capable of operating arbitrary commands.
In addition to enabling in-depth reconnaissance of focus on networks, site visitors assortment, and network interaction hijacking, the malware has been described as a heavily modified variation of the Mirai botnet, whose source code leaked in October 2016.
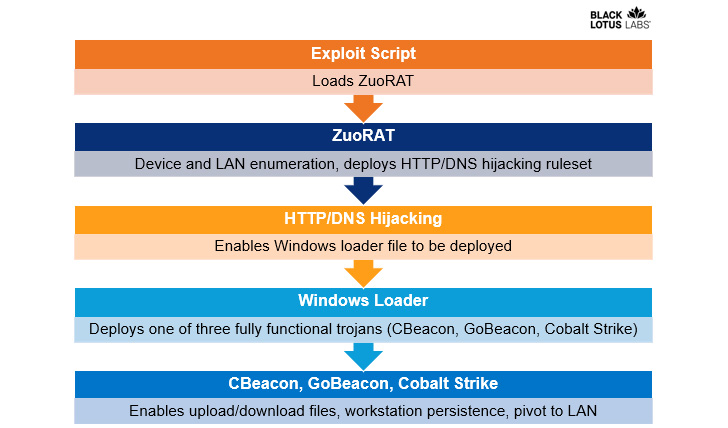
“ZuoRAT is a MIPS file compiled for SOHO routers that can enumerate a host and internal LAN, seize packets currently being transmitted about the infected unit, and conduct particular person-in-the-center attacks (DNS and HTTPS hijacking centered on predefined policies),” the researchers mentioned.
Also integrated is a operate to harvest TCP connections in excess of ports 21 and 8443, which are related with FTP and web browsing, perhaps enabling the adversary to maintain tabs on the users’ internet exercise driving the compromised router.
Other capabilities of ZuoRAT permit the attackers to watch DNS and HTTPS traffic with an aim to hijack the requests and redirect the victims to destructive domains making use of preset guidelines that are created and stored in non permanent directories in an try to resist forensic examination.
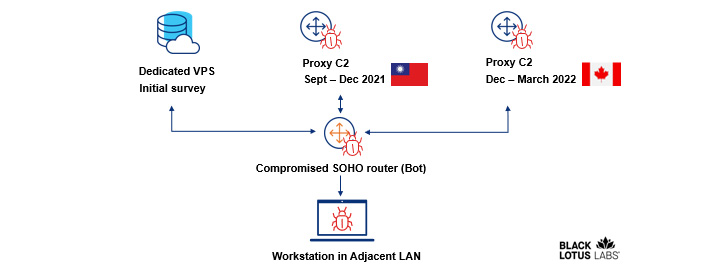
That is not the only stage taken by the hackers to conceal its actions, for the attacks depend on an obfuscated, multi-phase C2 infrastructure that includes utilizing a digital non-public server to fall the preliminary RAT exploit and leveraging the compromised routers themselves as proxy C2 servers.

To further prevent detection, the staging server has been spotted hosting seemingly innocuous material, in a single instance mimicking a website known as “muhsinlar.net,” a propaganda portal established up for the Turkestan Islamic Party (Idea), a Uyghur extremist outfit originating from China.
The id of the adversarial collective guiding the campaign continues to be unknown, though an investigation of the artifacts has unveiled attainable references to the Chinese province of Xiancheng and the use of Alibaba’s Yuque and Tencent for command-and-control (C2).
The elaborate and evasive mother nature of the procedure coupled with the ways applied in the attacks to remain undercover point towards possible country-point out action, Black Lotus Labs famous.
“The capabilities demonstrated in this marketing campaign — attaining accessibility to SOHO gadgets of various makes and versions, amassing host and LAN details to advise focusing on, sampling and hijacking network communications to gain most likely persistent obtain to in-land products and deliberately stealth C2 infrastructure leveraging multistage siloed router to router communications — points to a highly innovative actor,” the researchers concluded.
Observed this short article attention-grabbing? Adhere to THN on Fb, Twitter and LinkedIn to browse additional exceptional material we submit.
Some sections of this report are sourced from:
thehackernews.com


 Android Spyware ‘Revive’ Upgraded to Banking Trojan
Android Spyware ‘Revive’ Upgraded to Banking Trojan