A menace group of suspected Romanian origin called RUBYCARP has been noticed preserving a lengthy-working botnet for carrying out crypto mining, dispersed denial-of-provider (DDoS), and phishing attacks.
The group, believed to be energetic for at minimum 10 decades, employs the botnet for money get, Sysdig said in a report shared with The Hacker Information.
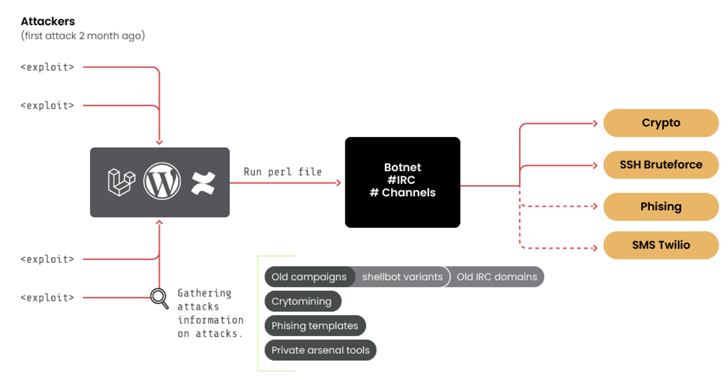
“Its key process of operation leverages a botnet deployed employing a selection of public exploits and brute-pressure attacks,” the cloud security agency mentioned. “This team communicates through general public and personal IRC networks.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Proof collected so considerably implies that RUBYCARP may perhaps have crossover with an additional menace cluster tracked by Albanian cybersecurity business Alphatechs underneath the moniker Outlaw, which has a record of conducting crypto mining and brute-drive attacks and has given that pivoted to phishing and spear-phishing campaigns to forged a extensive net.

“These phishing e-mail frequently entice victims into revealing sensitive data, such as login qualifications or financial specifics,” security researcher Brenton Isufi mentioned in a report posted in late December 2023.
A noteworthy aspect of RUBYCARP’s tradecraft is the use of a malware referred to as ShellBot (aka PerlBot) to breach focus on environments. It has also been noticed exploiting security flaws in the Laravel Framework (e.g., CVE-2021-3129), a technique also adopted by other threat actors like AndroxGh0st.

In a signal that the attackers are growing their arsenal of preliminary accessibility strategies to extend the scale of the botnet, Sysdig stated it found symptoms of WordPress sites becoming compromised utilizing commonly applied usernames and passwords.
“At the time access is obtained, a backdoor is put in based on the popular Perl ShellBot,” the company claimed. “The victim’s server is then related to an [Internet Relay Chat] server acting as command-and-control, and joins the bigger botnet.”
The botnet is estimated to comprise around 600 hosts, with the IRC server (“chat.juicessh[.]pro”) established on May well 1, 2023. It greatly relies on IRC for standard communications as effectively as for taking care of its botnets and coordinating crypto mining campaigns.
On top of that, associates of the team – named juice_, Eugen, Catalin, MUIE, and Smecher, among the other folks – have been identified to communicate via an Undernet IRC channel known as #cristi. Also place to use is a mass scanner instrument to uncover new possible hosts.

RUBYCARP’s arrival on the cyber threat scene is not shocking offered their capacity to choose benefit of the botnet to gasoline varied illicit income streams this kind of as crypto mining and phishing functions to steal credit history card quantities.
When it seems that the stolen credit history card information is employed to order attack infrastructure, there is also the chance that the facts could be monetized by way of other signifies by offering it in the cyber criminal offense underground.
“These menace actors are also concerned in the development and sale of cyber weapons, which is just not quite common,” Sysdig explained. “They have a significant arsenal of instruments they have crafted up above the several years, which presents them fairly a assortment of versatility when conducting their operations.
Found this short article fascinating? Adhere to us on Twitter and LinkedIn to read through more distinctive content material we publish.
Some elements of this posting are sourced from:
thehackernews.com

 Hackers Targeting Human Rights Activists in Morocco and Western Sahara
Hackers Targeting Human Rights Activists in Morocco and Western Sahara