Human rights activists in Morocco and the Western Sahara region are the targets of a new risk actor that leverages phishing attacks to trick victims into setting up bogus Android apps and provide credential harvesting webpages for Windows people.
Cisco Talos is tracking the action cluster under the name Starry Addax, describing it as principally singling out activists involved with the Sahrawi Arab Democratic Republic (SADR).
Starry Addax’s infrastructure – ondroid[.]site and ondroid[.]retail outlet – is intended to concentrate on both of those Android and Windows consumers, with the latter involving bogus internet websites masquerading as login web pages for common social media internet websites.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The adversary, believed to be energetic considering that January 2024, is identified to send spear-phishing email messages to targets, urging recipients to set up Sahara Press Service’s cellular app or a applicable decoy associated to the region.
Based on the working method from exactly where the ask for is originating from, the goal is either served a destructive APK that impersonates the Sahara Press Company or redirected to a social media login web site to harvest their qualifications.
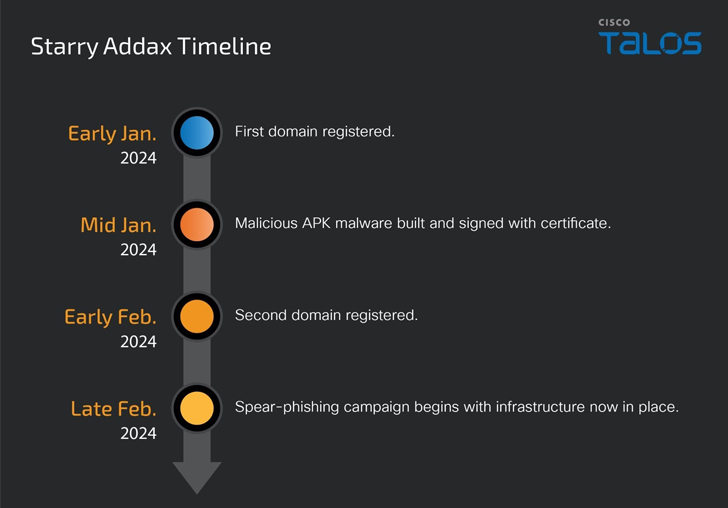
The novel Android malware, dubbed FlexStarling, is multipurpose and geared up to produce supplemental malware elements and steal sensitive information from contaminated products.
As soon as put in, it requests the victim to grant it in depth permissions that allow for the malware to perform nefarious steps, like fetching commands to be executed from a Firebase-based mostly command-and-regulate (C2), a signal that the danger actor is looking to fly underneath the radar.
“Strategies like this that goal superior-worth individuals ordinarily intend to sit quietly on the gadget for an extended interval,” Talos reported.

“All components from the malware to the running infrastructure seem to be to be bespoke/tailor made-manufactured for this precise campaign indicating a hefty concentrate on stealth and conducting activities underneath the radar.”
The advancement will come amid the emergence of a new commercial Android remote entry trojan (RAT) known as Oxycorat that is being presented for sale with varied information gathering abilities.
Identified this article interesting? Abide by us on Twitter and LinkedIn to read far more unique information we publish.
Some parts of this posting are sourced from:
thehackernews.com


 Researchers Discover LG Smart TV Vulnerabilities Allowing Root Access
Researchers Discover LG Smart TV Vulnerabilities Allowing Root Access