Orcus is a Remote Obtain Trojan with some distinct traits. The RAT permits attackers to create plugins and presents a strong core aspect set that makes it very a unsafe destructive system in its course.
RAT is quite a stable kind that often makes it to the top rated.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
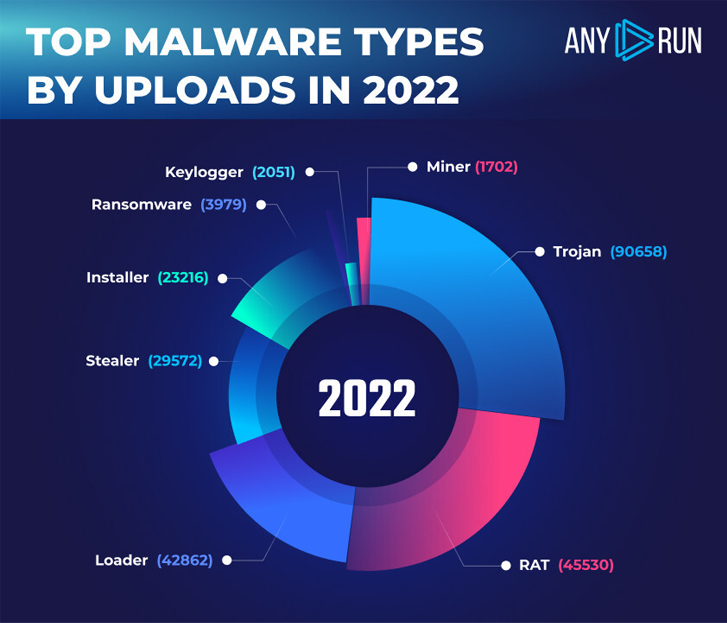 ANY.RUN’s top rated malware types in 2022
ANY.RUN’s top rated malware types in 2022
That is why you can expect to certainly occur throughout this kind in your exercise, and the Orcus family members specifically. To simplify your examination, we have gathered 3 lifehacks you should really just take advantage of. Listed here we go.
What is Orcus RAT?
Definition. Orcus RAT is a kind of destructive software program method that enables remote obtain and regulate of personal computers and networks. It is a kind of Distant Accessibility Trojan (RAT) that has been utilized by attackers to acquire entry to and handle computer systems and networks.
Abilities. Once downloaded on to a laptop or network, it commences to execute its destructive code, allowing for the attacker to obtain obtain and management. It is able of thieving data, conducting surveillance, and launching DDoS attacks.
Distribution. The malware is generally spread by using malicious e-mail, websites, and social engineering attacks. It is also frequently bundled with other destructive software package programs, such as Trojans, worms, and viruses.
Lifehacks for Orcus RAT malware assessment
The malware is made to be difficult to detect, as it often takes advantage of subtle encryption and obfuscation strategies to reduce detection. And if you have to have to get to the main of Orcus, the RAT configuration has all the information you will need.
And there are several lifehacks that you really should pay out consideration to while carrying out the analysis of Orcus RAT.
Right now we investigate the .NET sample that you can obtain for absolutely free in ANY.Operate database:
SHA-256: 258a75a4dee6287ea6d15ad7b50b35ac478c156f0d8ebfc978c6bbbbc4d441e1
1 — Get to know Orcus classes
You ought to commence with examining malware courses the place you can get the concealed program’s characteristics. A bunch of information that lessons include is specifically what will be beneficial for your investigate.
An Orcus.Config namespace has these lessons:
- Consts: Orcus’s information and directories details, e.g. the route to the file where consumer keystrokes are saved or to the directory exactly where the plugins made use of by a sample reside.
- Configurations: have wrapper solutions for decrypting the malware configuration and its plugins.
- SettingsData: is a static course only with the encrypted malware and plugin configuration fields.
2 — Discover Orcus RAT resources
The moment you dive into the Configurations course, you can observe the GetDecryptedSettings strategy. Later, it calls out the AES.Decrypt. And it appears to be like like your career is carried out and the malware configuration is lastly uncovered. But hold on – the assembly will not incorporate an Orcus.Shared.Encryption namespace.
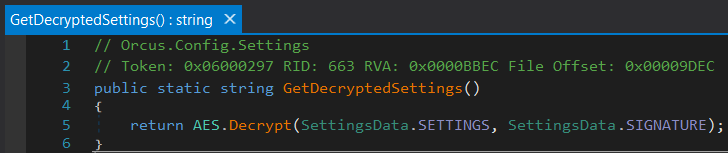 GetDecryptedSettings system
GetDecryptedSettings system
Orcus RAT stores additional assemblies inside of the malware assets working with a ‘deflate’ algorithm. You can go to the resources to uncover the required assembly. Unpacking them will permit you reveal the decryption algorithm that an Orcus sample utilizes. That brings 1 extra lifehack for currently.
3 — Decrypt details
Our treasure hunt goes on, as configuration data is encrypted.
Orcus RAT encrypts knowledge working with the AES algorithm and then encodes the encrypted details using Base64.
How to decrypt info:
- generate the crucial from a provided string applying Microsoft’s PBKDF1 implementation
- decode the knowledge from Base64
- use the generated vital to decrypt the data by means of the AES256 algorithm in CBC method.
As a consequence of decoding, we get the malware configuration in the XML structure. And all Orcus tricks are in your fingers now.
4 — Get all at when in a malware sandbox
Malware assessment is not a piece of cake, it surely requires time and energy to crack a sample. That’s why it is really constantly excellent to minimize the line: get all at once and in a shorter time. The respond to is straightforward – use a malware sandbox.
ANY.Operate malware sandbox instantly retrieves the Orcus RAT configuration. It truly is a substantially easier way to evaluate a malicious item. Try out it now – the provider has presently retrieved all details from this Orcus sample, so you can take pleasure in smooth research.
⚡ Publish the “hackernews1” promo code at [email protected] employing your business enterprise email deal with and get 14 times of ANY.Run high quality membership for free!
Summary
The Orcus RAT masquerades as a legit remote administration tool, even though it is distinct from its options and operation that it is not and was by no means meant to be. Investigation of the malware can help to get information for the cybersecurity of your corporation.
Safeguard your organization from this threat – carry out a comprehensive security system, coach personnel to recognize and stay away from malicious e-mails and sites, and use trustworthy anti-virus and ANY.Run malware sandbox to detect and analyze Orcus.
Located this short article fascinating? Follow us on Twitter and LinkedIn to examine additional unique content we submit.
Some sections of this post are sourced from:
thehackernews.com


 British Cyber Agency Warns of Russian and Iranian Hackers Targeting Key Industries
British Cyber Agency Warns of Russian and Iranian Hackers Targeting Key Industries