Shutterstock
Bitwarden buyers have elevated fears that destructive Google advertisements were becoming utilized to focus on buyers with malware-laden websites and dupe them into divulging login aspects.
Rumblings of fake Bitwarden adverts very first emerged on the company’s formal discussion board previously this 7 days, with a single person revealing they experienced encountered a destructive internet site promoted on the research motor.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The site attempted to impersonate the formal Web Vault login feature for the password manager.
Prashant Gonga, the consumer that initially highlighted the issue, explained they described the advertisement with the domain registrar and named on the Bitwarden compliance crew to investigate the trouble.
“The phishing web page is very comparable to the vault login website page, alongside with an SSL certification and similar-sounding domain identify to make it look legit,” they reported.
“I hope Bitwarden can consider down this domain ahead of an individual gets their account compromised.”
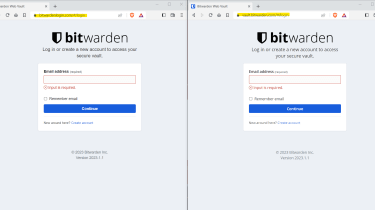
The faux and respectable Bitwarden pages were nearly indistinguishable
Buyers on the Bitwarden subreddit also flagged the issue in two individual posts, with some noting that the pretend and genuine internet websites have been nearly indistinguishable.
“God damn. In scenarios like this, how can I detect the phony a single? This is definitely scary,” one post on the subreddit explained.
One more article issued a warning to end users and advised them to report the malicious link to Google.
While the faux internet site highlighted by users seems to have been taken down at this phase, this follows similar occasions of danger actors using malicious adverts to target password supervisor shoppers.
Just this week, security scientists found that Google success for yet another well known password supervisor, 1Password, ended up demonstrating destructive ads. The issue prompted the enterprise to issue a warning to end users via social media urging them to stay vigilant and stay clear of clicking dubious links.
“It’s come to our interest that some websites are posing as 1Password,” the enterprise reported. “Remember to act cautiously when clicking hyperlinks and sharing qualifications or individual information and facts on-line. Make sure that any website link directs you to our web-site.”
It’s occur to our attention that some web sites are posing as 1Password. Don’t forget to act cautiously when clicking backlinks and sharing credentials or personal info on the internet. Be certain that any url directs you to our web-site, https://t.co/EHFDLvXsSi.
— 1Password (@1Password) January 26, 2023
Rising malvertising risks
The issue of malvertising, whereby destructive program or links are disguised as authentic advertisements, has been thrust firmly into the spotlight in latest months.
Earlier this month, cryptocurrency influencer ‘NFT God’ discovered on Twitter that they mistakenly downloaded a malicious backlink for streaming software OBS.
Following attempting to down load the software package by way of a destructive connection on the web site, the victim’s Substack and Twitter accounts ended up hacked and their NFT wallet was stolen.
The scale of this issue was even more highlighted by security researcher, Will Dormann, who disclosed that the faux OBS promotion was just 1 of a selection of malicious adverts existing on Google at the time.
Security industry experts at the time questioned why Google could not display one-way links in paid out advertisements in the Virus Complete system owned by the tech big.
Questioned about its plans to rectify the persistent issue and the plan of running links by means of Virus Full, Google declined to provide remark on the subject to IT Pro.
Because the scenario of malvertising involving OBS was raised, Dormann ongoing to spotlight the issue influencing many other popular apps utilized by buyers and enterprises alike.
Research from HP Wolf Security Menace Research Group observed that malvertising campaigns have continually developed in both equally quantity and sophistication. Preferred software package these as Audacity, Microsoft Groups, Discord, and Adobe Innovative Cloud have all been mimicked in latest months to dupe consumers.
Some parts of this write-up are sourced from:
www.itpro.co.uk

 3 Lifehacks While Analyzing Orcus RAT in a Malware Sandbox
3 Lifehacks While Analyzing Orcus RAT in a Malware Sandbox