
TLDR:
Adopt a present day, examination-pushed methodology for securing your corporation with Detection-as-Code.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Above the previous 10 years, threat detection has turn into business-critical and even more challenging. As enterprises go to the cloud, guide danger detection procedures are no extended equipped to continue to keep up. How can teams automate security examination at scale and address the worries that threaten company goals? The reply lies in dealing with risk detections like software package or detection-as-code.
Watch Panther’s On-Desire Webinar: Scaling Security with Detection-as-Code with Cedar to come across out how Cedar uses Panther to leverage Detection-as-Code to establish higher-signal alerts.
Detection-as-Code: A New (Hope) Paradigm Detections define logic for analyzing security log facts to discover attacker behaviors. When a rule is matched, an inform will get despatched to your staff for containment or investigation.
What is detection-as-code?
Detection-as-Code is a contemporary, flexible, and structured method to writing detections that implement software package engineering finest tactics to security. By adopting this new paradigm, teams can establish scalable procedures for creating and hardening detections to recognize innovative threats across swiftly expanding environments.
Added benefits of Adopting a Code-Pushed Workflow
Danger detection packages that are fantastic-tuned for specific environments and devices are the most impactful. By managing detections as well-penned code that can be tested, checked into supply command, and code-reviewed by friends, groups can generate greater-good quality alerts that cut down tiredness and speedily flag suspicious exercise.
1 — Make Tailor made, Flexible Detections with a Programming Language
Composing detections in a universally-acknowledged, versatile, and expressive language this sort of as Python features various pros alternatively of using domain-distinct languages (DSL) that are far too limited. With languages, this sort of as Python, you can compose additional sophisticated and tailor-made detections to match the needs particular to your business. These regulations also tend to be a lot more readable and straightforward to understand as the complexity will increase.
One more benefit of this strategy is using a loaded set of built-in or third-party libraries produced by the security community for interacting with APIs or processing information, which boosts the usefulness of the detection.
2 — Check-Driven Improvement (TDD)
A appropriate QA for detection code can help groups to find out detection blind-spots early on, protect screening for false alerts, and encourage detection efficacy. A TDD solution allows security groups to assume like an attacker, document that knowledge, and curate an internal repository of insight into the attacker’s lifecycle.
The edge of TDD is a lot more than just validation of code correctness. A TDD strategy to writing detections enhances the good quality of detection code and enables much more modular, extensible, and adaptable detections. Engineers can very easily make modifications to their detection with out worry of breaking alerts or hamstringing day to day operations.
3 — Collaboration with Model Regulate Units
When crafting new detections or modifying them, edition management lets groups to swiftly and simply revert to former states. It also confirms that groups are applying the most up-to-day detection rather than referencing out-of-date or incorrect code. Model regulate can also assist give necessary context for specific detections that induced an notify or enable pinpoint when detections are adjusted.
As new and more info enters the procedure in excess of time, detections need to also alter. A change command course of action is critical to support groups address and alter the detections as required, while simultaneously guaranteeing that all changes are perfectly-documented and nicely-reviewed.
4 — Automatic Workflows for Trusted Detections
A Ongoing Integration/Ongoing Deployment (CI/CD) pipeline can be beneficial for security groups that have extended desired to transfer security even more left. Applying a CI/CD pipeline will help reach the pursuing two objectives:
- Remove silos concerning groups as they function together on a prevalent platform, code-assessment every single other’s do the job, and remain arranged.
- Provide automatic screening and shipping and delivery pipelines for your security detections. Groups can remain agile by concentrating on making high-quality-tuned detections. In its place of manually screening, deploying, and making sure that the detections usually are not extremely tuned, which could trigger phony alerts.
5 — Reusable Code
Last but not least, Detection-as-Code can endorse code reusability across a massive established of detections. As groups write huge quantities of detections above time, they commence to see unique styles arise. Engineers can reuse the current code to conduct the very same or incredibly identical perform throughout various detections without the need of starting from scratch.
Code reusability can be a vital component of detection-crafting that lets groups to share functions between detections or modify and adapt detections for precise use-instances. For instance, suppose you required to repeat a established of Permit/Deny lists (let’s say for access administration) or a distinct processing logic in several areas. In that case, you can use Helpers in languages this kind of as Python to share features concerning detections.
Introduction to Panther
Panther is a security analytics platform built to reduce the challenges of conventional SIEMs. Panther is built for security engineers, by security engineers. Alternatively than inventing nevertheless another proprietary language for expressing detection logic, Panther gives security groups a Python rules-engine to write expressive menace detection and automate detection and response at cloud-scale. Panther’s modular and open solution presents uncomplicated integrations and adaptable detections to enable you build a modern day security functions pipeline.
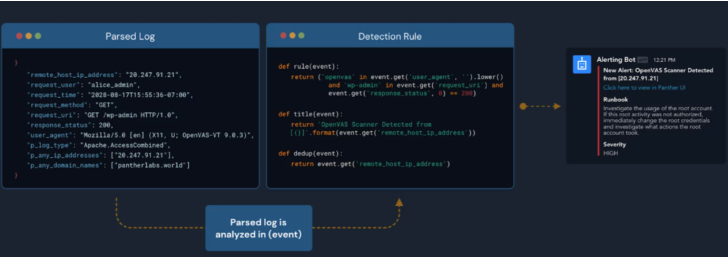 Detection-as-Code workflow in Panther
Detection-as-Code workflow in Panther
Panther presents reputable and resilient detections that can make it effortless to:
- Write expressive and adaptable detections in Python for requirements distinct to your enterprise.
- Framework and normalize logs into a stringent schema that permits detections with Python and queries with SQL.
- Conduct authentic-time danger detection and power investigations towards enormous volumes of security details.
- Gain from 200+ pre-crafted detections mapped to precise threats, suspicious action, and security frameworks like MITRE ATT&CK.
Detection-as-Code workflow in Panther
An Case in point Detection in Panther
When producing a detection in Panther, you start with a rule() perform that identifies a distinct actions to discover. For illustration, let’s suppose you want an notify when a brute power Okta login is suspected. The adhering to detection can assist identify this habits with Panther:
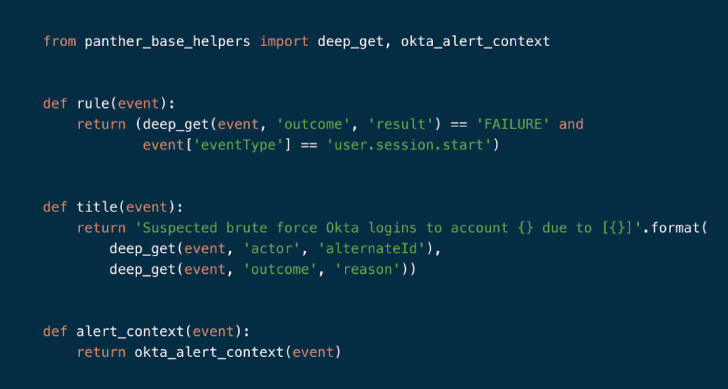 Okta Brute Power Login Rule in Panther
Okta Brute Power Login Rule in Panther
In the over instance:
- The rule() purpose requires just one argument of ‘event’ and returns a boolean worth.
- The title() operate controls the created warn information despatched to analysts. Values from the situations can then be interpolated to increase useful contexts.
Regulations can be enabled and analyzed right in the Panther UI, or modified and uploaded programmatically with the Panther Assessment tool, which permits you to check, offer, and deploy detections through the command-line interface (CLI). And to aid with incident triage, Panther guidelines include metadata this sort of as severity, log kinds, unit tests, runbooks, and a lot more.
Get Began
Are you having full gain of all your security details to detect threats and suspicious exercise? Master how to protected your cloud, network, apps, and endpoints with Panther Business. Ask for a demo these days.
Observed this write-up intriguing? Follow THN on Fb, Twitter and LinkedIn to go through additional exclusive information we post.
Some elements of this post are sourced from:
thehackernews.com


 Experts Detail Saintstealer and Prynt Stealer Info-Stealing Malware Families
Experts Detail Saintstealer and Prynt Stealer Info-Stealing Malware Families