Cybersecurity scientists have dissected the inner workings of an info-stealing malware termed Saintstealer that is intended to siphon credentials and system information and facts.
“Soon after execution, the stealer extracts username, passwords, credit rating card aspects, and many others.,” Cyble researchers mentioned in an analysis previous week. “The stealer also steals facts from different places across the procedure and compresses it in a password-secured ZIP file.”
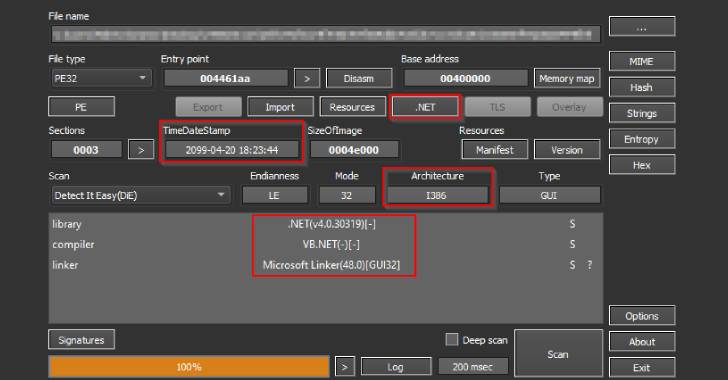
A 32-little bit C# .NET-dependent executable with the name “saintgang.exe,” Saintstealer is outfitted with anti-analysis checks, opting to terminate by itself if it’s managing both in a sandboxed or virtual atmosphere.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
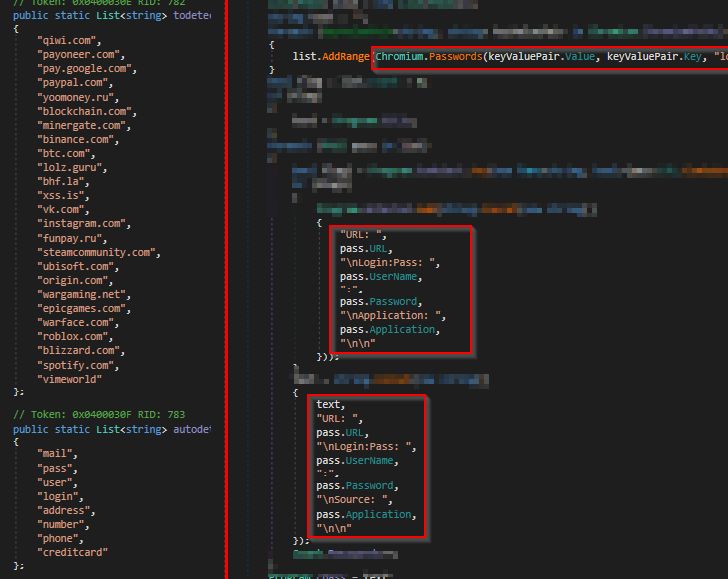
The malware can seize a vast selection of facts that ranges from getting screenshots to gathering passwords, cookies, and autofill info stored in Chromium-dependent browsers such as Google Chrome, Opera, Edge, Brave, Vivaldi, and Yandex, among others.
It can also steal Discord multi-factor authentication tokens, data files with .txt, .doc, and .docx extensions as well as extract details from VimeWorld, Telegram, and VPN applications like NordVPN, OpenVPN, and ProtonVPN.
Moreover transmitting the compressed information to a Telegram channel, the metadata relevant to the exfiltrated information is sent to a distant command-and-handle (C2) server.
What’s extra, the IP deal with linked to the C2 domain — 141.8.197[.]42 — is tied to several stealer people this kind of as Nixscare stealer, BloodyStealer, QuasarRAT, Predator stealer, and EchelonStealer.
“Details stealers can be harmful to people today as nicely as large companies,” the researchers claimed. “If even unsophisticated stealers like Saintstealer achieve infrastructural entry, it could have devastating effects on the cyberinfrastructure of the focused organization.”
The disclosure comes as a new infostealer named Prynt Stealer has surfaced in the wild that can also perform keylogging operations and money theft employing a clipper module.
“It can concentrate on 30+ Chromium-based browsers, 5+ Firefox-dependent browsers, and a range of VPN, FTP, messaging, and gaming apps,” Cyble pointed out past month.
Offered for $100 for a one particular-month license and $900 for a lifetime membership, the malware joins a long listing of other lately marketed stealers, such as Jester, BlackGuard, Mars Stealer, META, FFDroider, and Lightning Stealer.
Located this report intriguing? Observe THN on Fb, Twitter and LinkedIn to read additional special material we article.
Some components of this report are sourced from:
thehackernews.com

 Hackers Actively Exploit F5 BIG-IP Bug
Hackers Actively Exploit F5 BIG-IP Bug