5G is a match changer for cell connectivity, which include cellular connectivity to the cloud. The technology supplies significant pace and very low latency when connecting smartphones and IoT gadgets to cloud infrastructure. 5G networks are a critical aspect of all infrastructure levels concerning the conclusion person and the conclude provider these networks transmit delicate data that can be critical for governments and businesses, not to point out people. As a consequence, 5G networks are a prime goal for attackers. For this motive, cybersecurity has been a essential thought in establishing the 5G regular.
5G encompasses robust security characteristics that assurance confidentiality, integrity, and availability of network solutions and consumer information. In this write-up, Seva Vayner, Solution Owner of Gcore’s Edge Cloud services, gives a deep dive into 5 of 5 G’s reducing-edge security actions. He also delves into the pivotal performance capabilities of 5G, accompanied by use cases that display how modern, cloud-indigenous enterprises can leverage this transformative technology to their benefit.
What Is 5G
5G is the new common of wireless networks that supersedes 4G (LTE). It is developed to link people today and devices at quickly speeds with reduced latency.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The throughput of 5G much exceeds the throughput of 4G. In idea, 5G features up to 20 Gbps in the downlink. In comparison, 4G only gives up to 100 Mbps, 200 times fewer than 5G. In accordance to the 2023 CELLSMART survey, in follow, outdoor tests show that 5G operators in the US and EU supply near to 1 Gbps for the downlink channel.
As for 5G latency, it can be up to 10 ms (vs. 30 ms in 4G)—but only in a check environment. In actuality, latency is dependent on many factors. For instance, Ericsson’s checks in the US showed that 5G latency is ordinarily all over 20 ms but no a lot more than 50 ms, which is practically unnoticeable to people. This is excellent information for gaming, exactly where latency greater than 50 ms is critical.
5 Should-Know Security Options of 5G
Necessary 5G security methods and systems incorporate encryption, privacy protection, authentication and authorization, network slicing, and network equipment security assurance. Let us look at them in much more depth.
1. Encryption
Encryption safeguards consumer information and network targeted visitors from eavesdropping, interception, and tampering. 5G makes use of powerful encryption algorithms these kinds of as AES, ZUC, SNOW 3G, and HMAC-SHA-256. The encryption attributes include a separation of the security keys between the core network segments. Also made available is rapidly synchronization of the security contexts in the obtain network (base stations) and the main network.
2. Privacy Security
In 5G networks, privacy protection is ensured as a result of the use of encryption and numerous other methods. These tactics correctly guard from substantial threats like IMSI/TMSI-catchers, which attackers frequently use to establish and observe network subscribers. Cell operators can implement the Elliptic Curve Built-in Encryption Scheme system to conceal and routinely update a subscriber’s short term identifier (TMSI). In addition, operators can detect wrong base stations, which are normally the resource of IMSI/TMSI-catchers.
3. Authentication and Authorization
Authentication and authorization in 5G is centered on the Authentication and Critical Settlement method (5G AKA). It involves a sturdy authentication mechanism to verify the identity of customers, products, and network features. Not like 4G, 5G won’t involve bodily SIM playing cards for qualifications, but also supports pre-shared keys, certificates, and tokens. Cellular operators can pick out the authentication qualifications and authentication procedures best suited to their buyers and IoT products. For illustration, traditional SIM playing cards are acceptable for cell telephones, when electronic qualifications are a lot more acceptable for basic IoT units outfitted with eSIM.
4. Network Slicing
Network slicing permits the development of virtual networks for unique expert services and apps. For occasion, a subscribing corporation can use a single network slice for significant-priority staff members with access to company providers, and a different slice for minimal-priority IoT warehouse sensors that transmit facts to storage in a community cloud. Just about every network slice can be assigned distinct security policies and protocols, helping to isolate and defend facts and products and services.
5. NESAS
NESAS, or the Network Machines Security Assurance Plan, makes certain the safe implementation of telecom products that mobile operators use in their networks, including 5G. Created by 3GPP and GSMA, NESAS establishes security needs and procedures for thriving infrastructure audits. NESAS usually takes into account both of those regional and world wide cybersecurity rules, for example, the EU cybersecurity certification framework. It is obligatory for sellers and mobile operators to comply with NESAS necessities.
How 5G Advantages Cloud-Indigenous Firms
With its very low latency, better bandwidth, and in depth security steps, 5G strengthens the security of cloud connectivity. This improve permits protected and dependable transmission of sensitive info as nicely as genuine-time data processing. 5G lets companies to confidently use cloud solutions to retail store and manage their info, minimizing the risk of facts breaches.
5G features outstanding fault tolerance when as opposed to cable connections, largely thanks to the inherent resilience of wi-fi channels in mitigating interaction failures. With a cable connecting an business office or manufacturing facility to a company, it could be important to develop a backup connection via an optical fiber or radio. But 5G has a reserved channel from the outset. If just one foundation station fails, other people will acquire above instantly, earning downtime not likely.
In addition, 5G network slicing abilities deliver organizations with dedicated digital networks inside their IT method. This allows superior isolation and segregation of facts, apps, and expert services, increasing total security. Enterprises can develop personalized network slices for certain duties or individual departments. This characteristic guarantees that critical details and apps continue being independent and shielded.
Exactly where 5G Can Be Valuable in Conjunction with the Cloud
Health care. Doctors can use applications like a cloud AI platform to remotely check individual health knowledge in real time even though remaining cell by using 5G. Soon after the health-related evaluation, high-resolution professional medical unit photographs can be uploaded to the Cloud AI platform, processed, and returned to a physician for further use. 5G also allows with ML diagnostics: a cloud ML application can obtain pictures or other professional medical data over 5G for condition prediction, detection, and classification.
Protected access to corporate resources. With 5G information protection, obtain management management is enabled for every SIM card. Authorized staff can securely obtain corporate electronic belongings, details, and purposes while functioning remotely with out the have to have for a VPN or firewall is expected.
Streaming. With 5G and cloud solutions like CDN, streamers, bloggers, and podcasters can love uninterrupted, high-high-quality, dwell video clip and audio streaming. 5G facilitates the fusion of interactive aspects in just stay movie streams whilst instantaneous movie analytics produce actual-time metrics that enrich the total dwell celebration expertise.
Wise factories. Manufacturers can predict maintenance requires and detect probable problems or failures by monitoring devices information with IoT equipment. They can use ML cloud services for analytics, although 5G delivers a protected and quickly connection to their cloud infrastructure.
Automotive IoT. Because of their efficiency abilities, 5G networks are a superior signifies of information transmission in industries. In the self-driving auto field, data from the vehicle’s sensors and cameras can be effortlessly despatched to the cloud at large speeds, and then processed by cloud AI equipment.
Gcore’s 5G eSIM System
The 5G eSIM platform from the global cloud and CDN provider Gcore offers a strong instance of a collaborative 5G and cloud answer. The 5G eSIM system presents entry to IaaS, PaaS, AI infrastructure, a streaming platform, and other Gcore providers over 5G. Gcore’s prospects can securely hook up to their cloud infrastructure by means of a immediate non-public channel from additional than 150 nations all over the world. 5G eSIM guarantees protected information transmission by innovative encryption algorithms and security protocols.
Right here is the architecture of the system:
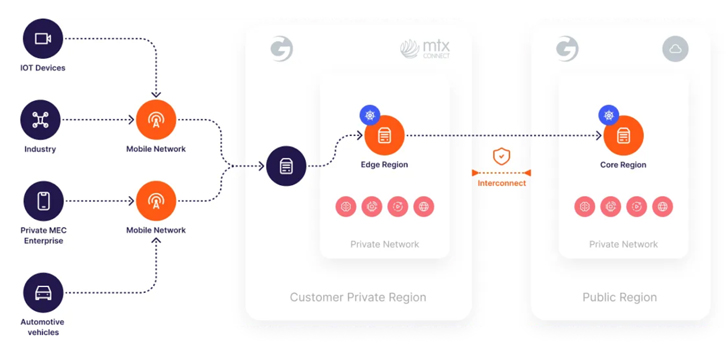 Figure 1. Gcore’s 5G eSIM System architecture
Figure 1. Gcore’s 5G eSIM System architecture
Aside from the 5G security features that are created-in in the typical, the 5G eSIM platform provides:
- Control of visitors consumption for configuring a white listing and a black listing. These enable or deny unique protocols, URLs, and IPs.
- Workgroup management for assigning employees’ names to eSIMs and grouping them by function, seniority, or section.
- In-depth reporting program to see the report by team, period, eSIM, nation, and much more.
- Personalized eSIMs for each and every staff to assign them a company mobile amount. Workforce can access the internet and inside sources from a distant spot with no the need for a corporate VPN and with out roaming expenses.
- Secured unique routing and targeted traffic filtering to be certain defense towards cyberattacks and knowledge leakage.
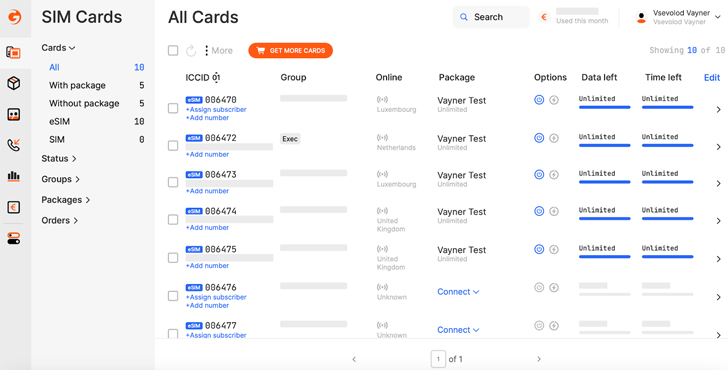 Determine 2. Gcore’s 5G eSIM regulate panel
Determine 2. Gcore’s 5G eSIM regulate panel
In addition, Gcore gives performance in just its Cloud to secure all purchaser expert services:
- Identity and access management
- Firewall with versatile security group configuration
- Secrets and techniques management
- IaaS safety
Consumers can mix these cloud options with the benefits and functions made available by the 5G eSIM platform.
Summary
5G has outstanding efficiency abilities and state-of-the-art security attributes these kinds of as encryption, network slicing, and 5G AKA. 5G networks are a lot more resilient and versatile than LAN and WLAN networks this would make 5G more effective in phrases of technological progress, organization pursuits, and compliance with security needs. As a final result, 5G networks aid corporations evolve quicker with no cutting down the level of infrastructure safety.
Uncovered this posting fascinating? Abide by us on Twitter and LinkedIn to browse extra exclusive content material we post.
Some areas of this post are sourced from:
thehackernews.com


 Romania’s Safetech Leans into UK Cybersecurity Market
Romania’s Safetech Leans into UK Cybersecurity Market