Security researchers have shared a deep dive into the business Android spy ware referred to as Predator, which is marketed by the Israeli organization Intellexa (formerly Cytrox).
Predator was initial documented by Google’s Menace Assessment Team (TAG) in May 2022 as section of attacks leveraging 5 distinct zero-day flaws in the Chrome web browser and Android.
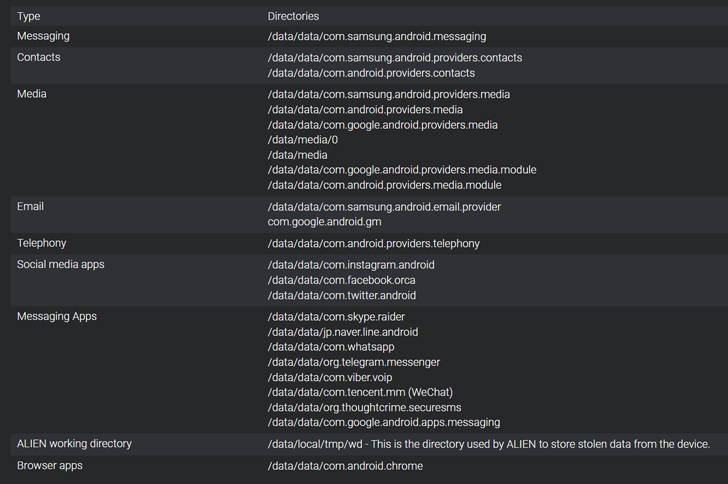
The adware, which is sent by suggests of a different loader component termed Alien, is outfitted to record audio from phone phone calls and VoIP-based mostly applications as effectively as gather contacts and messages, like from Signal, WhatsApp, and Telegram.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Its other functionalities make it possible for it to disguise applications and avert apps from becoming executed on rebooting the handset.
“A deep dive into each spy ware elements implies that Alien is far more than just a loader for Predator and actively sets up the very low-degree abilities needed for Predator to spy on its victims,” Cisco Talos said in a technological report.
Spyware like Predator and NSO Group’s Pegasus are cautiously delivered as component of very-qualified attacks by weaponizing what are called zero-click on exploit chains that normally involve no conversation from the victims and let for code execution and privilege escalation.
“Predator is an exciting piece of mercenary spyware that has been all-around given that at least 2019, designed to be flexible so that new Python-dependent modules can be shipped devoid of the require for recurring exploitation, as a result earning it particularly functional and unsafe,” Talos discussed.
Each Predator and Alien are intended to get about security guardrails in Android, with the latter loaded into a core Android approach termed Zygote to down load and start other spy ware modules, counting Predator, from an exterior server.
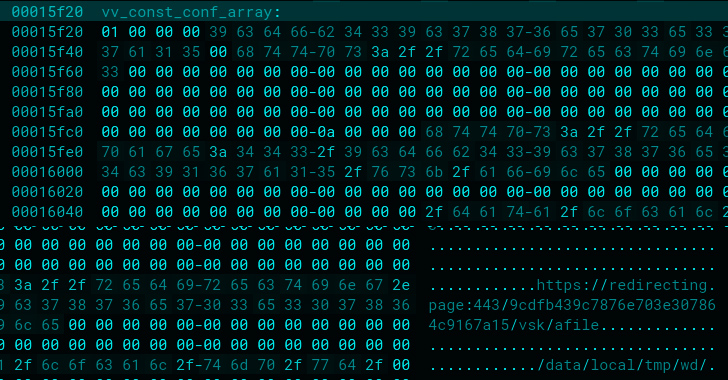
It is really presently not crystal clear how Alien is activated on an contaminated machine in the initially area. Even so, it’s suspected to be loaded from shellcode which is executed by using edge of original-phase exploits.
“Alien is not just a loader but also an executor — its various threads will preserve looking at instructions coming from Predator and executing them, supplying the spyware with the signifies to bypass some of the Android framework security capabilities,” the company said.
The numerous Python modules affiliated with Predator make it feasible to attain a broad array of tasks such as facts theft, surveillance, distant entry, and arbitrary code execution.
The spyware, which comes as an ELF binary ahead of placing up a Python runtime atmosphere, can also insert certificates to the retailer and enumerate the contents of several directories on disk if it is really managing on a system made by Samsung, Huawei, Oppo, or Xiaomi.
That stated, there are however many missing pieces that could assistance full the attack puzzle. This contains a key module termed tcore and a privilege escalation mechanism dubbed kmem, each of which have remained elusive to attain hence significantly.
Cisco Talos theorized that tcore could have implemented other options like geolocation monitoring, camera access, and simulating a shutdown to covertly spy on victims.
The results appear as danger actors’ use of business spyware has witnessed a surge in latest yrs just as the amount of cyber mercenary companies supplying these products and services are on an upward trajectory.
Although these complex equipment are supposed for exclusive use by governments to counter serious criminal offense and battle countrywide security threats, they have also been abused by buyers to surveil on dissidents, human legal rights activists, journalists, and other associates of the civil society.
As a scenario in place, digital legal rights group Entry Now stated that it uncovered proof of Pegasus targeting a dozen men and women in Armenia – which include an NGO employee, two journalists, a United Nations formal, and a human rights ombudsperson in Armenia. One particular of the victims was hacked at minimum 27 periods between Oct 2020 and July 2021.
Forthcoming WEBINARZero Have confidence in + Deception: Discover How to Outsmart Attackers!
Explore how Deception can detect state-of-the-art threats, prevent lateral motion, and enhance your Zero Belief technique. Sign up for our insightful webinar!
Preserve My Seat!
“This is the first documented proof of the use of Pegasus spy ware in an global war context,” Entry Now reported, introducing it started an investigation after Apple sent notifications to the men and women in issue that they could have been a sufferer of point out-sponsored spy ware attacks in November 2021.
There are no conclusive hyperlinks that connect the adware use to a particular federal government agency in either Armenia or Azerbaijan. It is worth noting that Armenia was outed as a customer of Intellexa by Meta in December 2021 in attacks aimed at politicians and journalists in the nation.
What is extra, cybersecurity organization Look at Point previously this yr disclosed that a variety of Armenian entities have been contaminated with a Windows backdoor referred to as OxtaRAT as part of an espionage marketing campaign aligned with Azerbaijani interests.
In a much more uncommon transform of situations, The New York Moments and The Washington Article described this week that the Mexican government may possibly be spying on alone by employing Pegasus from a senior formal in charge of investigating alleged military services abuses.
Mexico is also the to start with and most prolific user of Pegasus, inspite of its claims to cease the unlawful use of the notorious spyware.
Discovered this post appealing? Adhere to us on Twitter and LinkedIn to read extra special written content we post.
Some sections of this posting are sourced from:
thehackernews.com

 5 Must-Know Facts about 5G Network Security and Its Cloud Benefits
5 Must-Know Facts about 5G Network Security and Its Cloud Benefits