For far too extended the cybersecurity planet concentrated exclusively on information technology (IT), leaving operational technology (OT) to fend for alone. Traditionally, several industrial enterprises experienced dedicated cybersecurity leaders. Any security conclusions that arose fell to the plant and manufacturing unit supervisors, who are highly proficient technical authorities in other regions but normally deficiency cybersecurity schooling or awareness.
In more current many years, an uptick in cyberattacks in opposition to industrial facilities and the trend of IT/OT convergence pushed by Marketplace 4. have highlighted the vacuum of ownership all around OT security. In accordance to a new Fortinet report, most businesses are wanting to Main Info Security Officers (CISOs) to clear up the trouble.
The good news is, CISOs are no strangers to alter or complicated challenges. The position by itself is fewer than 20 many years old, nonetheless in people two decades CISOs have navigated some of the most disruptive cybersecurity events that were really watershed moments in technology.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
However, most CISOs have produced their mark securing IT environments — and IT security techniques and instruments not often translate to an OT context. When the gentle capabilities of collaboration and team-building will unquestionably assist CISOs as they convey the manufacturing facility ground into their realm of duty, they should also make a concentrated effort to recognize the OT landscape’s distinctive topography and distinctive security troubles.
Security more than every little thing
The CIA triad — Confidentiality, Integrity & Availability — is a vital strategy in cybersecurity. Critically, IT and OT prioritize the aspects of the triad otherwise — while security is generally the popular denominator.
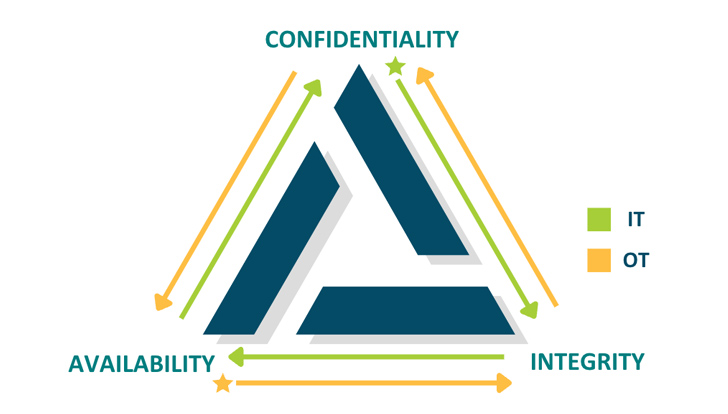 Image 1: The CIA triad of IT security is reversed in the OT environment, exactly where availability is the highest priority.
Image 1: The CIA triad of IT security is reversed in the OT environment, exactly where availability is the highest priority.
- In IT, safety indicates that details is secured by means of confidentiality. People get damage when their delicate, private facts is compromised. For the business, securing details will save them from breaches, fines, and reputational hurt.
- In OT, protection means that cyber-actual physical techniques are trustworthy and responsive. Individuals get harm when a blast furnace or an industrial boiler does not perform properly. For the enterprise, availability keeps programs managing on time down to the millisecond, which guarantees efficiency and profitability.
Relatively ironically, the AIC triad of the OT world has resulted in units and resources that prioritize physical protection but typically arrive with number of or no cybersecurity attributes at all. It will be the CISO’s obligation to detect and carry out security alternatives that protect OT devices from cyberthreats with no disrupting their operations.
.xm_container display screen: flex align-objects: centre margin: 20px 10px 30px qualifications: #f9fbff shade: #160755 padding: 5% border: 2px reliable #d9deff border-radius: 10px text-align: remaining box-shadow:6px 6px #e2ebff -webkit-border-major-remaining-radius: 25px -moz-border-radius-topleft: 25px -webkit-border-bottom-proper-radius: 25px -moz-border-radius-bottomright: 25px .book-image flex: 200px margin-ideal: 20px padding: 20px .book-particulars flex: 1 .ebook-details ul margin: 15px .book-details ul li margin-base: 5px @media (max-width: 600px) .xm_container flex-course: column .book-picture margin-correct: margin-base: 20pxpadding: 20px

Questioning how to safeguard your industrial operations from likely threats? This thorough report on I-SRA has the solutions. Uncover the prime worries, which include operational safety challenges and Advanced Persistent Threats (APTs). Down load the report today!
Degrees of segmentation
In equally OT and IT, segmentation boundaries the network’s attack floor. In OT, the Purdue Design serves as a framework for how and why units can and should really communicate with each other.
In a extremely simplified nutshell, the Purdue Product contains 5 levels.
- Amounts 4 and 5 are the outermost levels that contain web and email servers, IT infrastructure, and buyers firewalling in remotely.
- Degrees 2 and 3 are the operational layers that function the software and applications that operate OT environments.
- Stages and 1 maintain the products, sensors, programmable logic controllers (PLCs), and dispersed control systems (DCS) that do the genuine work and need to be guarded from outside the house interference.
The intent of these layers is to build both rational and physical separation concerning method levels. The nearer you get to the cyber-physical procedure of industrial units like injectors, robotic arms, and industrial presses, the much more checks and balances are in spot to guard them.
When the thought of segmentation will not be new to CISOs, they will need to have to have an understanding of that the separation of zones is significantly stricter in OT environments and need to be enforced at all instances. Industrial enterprises adhere to the Purdue product or other related frameworks to make certain security and security and to meet numerous regulatory compliance mandates.
Downtime is not an solution
In IT, downtime for updates and patches is no massive offer, especially in a Software program-as-a-Services (SaaS) environment in which new updates are produced practically in genuine time.
Whether or not for security or financial gain, OT devices are constantly up and functioning. They are not able to be stopped or paused to down load a new operating procedure or apply even a critical patch. Any course of action that involves downtime is basically a non-starter for the extensive majority of OT systems. For this reason, CISOs need to not be astonished to uncover a long time-aged systems (probably managing on software package that attained its finish-of-existence date lengthy ago) that continue to provide as a vital piece of the procedure.
The challenge experiencing CISOs will be to detect security controls that will not interrupt or interfere with fragile OT processes. The ideal remedies will “wrap” the existing OT infrastructure in a layer of security that guards critical processes without transforming, complicating, or crowding them.
All obtain is “distant” obtain
Historically, OT units have been guarded as a result of isolation. Now that companies are connecting these environments to capitalize on Sector 4. or to let a lot easier obtain for contractors, all access will have to be monitored, controlled, and recorded.
- The IT setting is a digital area in which business comes about. Enterprise end users carry out their perform and systems trade data all inside of this place, working day in and working day out. To set it yet another way, people are intended to actively participate in and make adjustments to the IT surroundings.
- OT units and environments are constructed to operate without having human intervention — “established it and overlook it.” Human beings are meant to established them up and then enable them operate. People do not continue to be logged into an OT environment all day the way business enterprise consumers would in an IT procedure.
In this context, any person accessing the OT natural environment is properly an outsider. No matter whether it is a seller connecting remotely, a business person coming in via the IT network, or even an OT operator accessing the environment on-site, every single relationship will come from the outside. Recognizing this important issue will aid CISOs to recognize that industrial secure remote access (I-SRA) equipment must be applied for all accessibility situations, not only those people that IT would consider to be “distant.”
IT instruments do not (constantly) function for OT
Applications built for IT rarely at any time translate to OT.
- Fundamental features like vulnerability scanning can interrupt OT procedures and knock devices absolutely offline, and most units do not have enough CPU/RAM to assistance endpoint security, anti-virus, or other agents.
- Most IT instruments route visitors through the cloud. In OT, this can compromise availability and can’t aid the various unconnected parts widespread to OT environments.
- The everyday living cycles of IT applications are typically a lot shorter than the lifetime cycles of OT units. Owing to the normally-up mother nature of OT environments, any resource that demands recurrent patching, updates, or downtime is not relevant.
Forcing IT-designed tools into OT environments only adds complexity without the need of addressing the elementary security specifications and priorities of these environments. The faster a CISO realizes that OT devices have earned security methods developed for their distinctive desires, the a lot quicker they will be on their way to applying the most effective instruments and policies.
Smooth techniques are the keys to CISO success
Offered that most cybersecurity leaders at present have a tendency to come from IT security roles, it would make perception that numerous CISOs will have a (potentially unconscious) bias towards IT philosophies, tools, and techniques. To effectively secure OT environments, CISOs will need to turn into students once again and lean on others to understand what they do not still know.
The very good news is that CISOs commonly have a propensity to request the appropriate issues and find support from the suitable professionals even though still pushing the envelope and demanding good outcomes. At the finish of the working day, a CISO’s task is to lead people and teams of authorities to complete the better purpose of securing the enterprise and enabling the company. People ready to bridge the OT security divide as a result of solid leadership and a willingness to discover need to speedily uncover on their own on the street to achievements.
To understand about a actual-world alternative that can enable CISOs better secure their OT atmosphere, discover Cyolo.
Uncovered this posting interesting? Observe us on Twitter and LinkedIn to study a lot more exceptional content material we publish.
Some areas of this article are sourced from:
thehackernews.com


 8Base Ransomware Spikes in Activity, Threatens U.S. and Brazilian Businesses
8Base Ransomware Spikes in Activity, Threatens U.S. and Brazilian Businesses