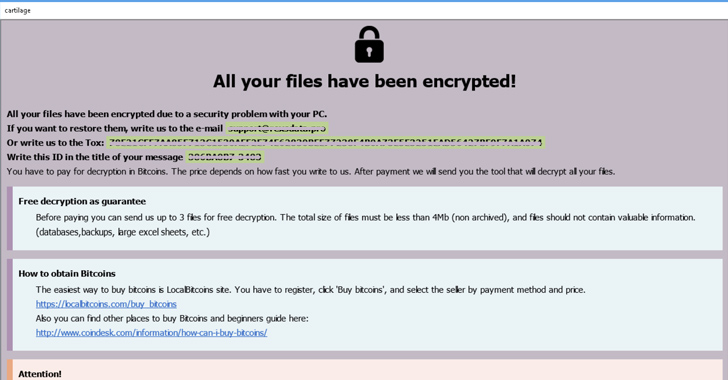
A ransomware risk referred to as 8Base that has been functioning underneath the radar for in excess of a year has been attributed to a “significant spike in action” in May well and June 2023.
“The team makes use of encryption paired with ‘name-and-shame’ procedures to compel their victims to spend their ransoms,” VMware Carbon Black scientists Deborah Snyder and Fae Carlisle explained in a report shared with The Hacker News. “8Base has an opportunistic pattern of compromise with the latest victims spanning across assorted industries.”
8Base, in accordance to figures collected by Malwarebytes and NCC Team, has been joined to 67 attacks as of Might 2023, with about 50% of the victims running in the business expert services, production, and development sectors. A majority of the specific companies are positioned in the U.S. and Brazil.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

With pretty small identified about the operators of the ransomware, its origins keep on being some thing of a cipher. What is actually apparent is that it has been lively because at minimum March 2022 and the actors describe them selves as “straightforward pentesters.”
VMware mentioned 8Base is “strikingly” similar to that of another details extortion group tracked as RansomHouse, citing overlaps in the ransom notes dropped on compromised devices and the language utilised in the respective information leak portals.
“The verbiage is copied term for word from RansomHouse’s welcome web page to 8Base’s welcome webpage,” the researchers reported. “This is the circumstance for their Terms of Assistance web pages and FAQ web pages.”
A comparison of the two threat groups reveals that while RansomHouse brazenly advertises their partnerships, 8Foundation does not. An additional crucial differentiator is their leak pages.
But in an attention-grabbing twist, VMware observed that it was in a position to detect a Phobos ransomware that makes use of the “.8base” file extension for encrypted information, boosting the likelihood that 8Base could be a successor to Phobos or that the attackers are basically building use of currently existing ransomware strains without the need of obtaining to develop their individual customized locker.
“The speed and efficiency of 8Base’s current functions does not point out the start out of a new group but alternatively signifies the continuation of a effectively-set up mature firm,” the scientists said. “Regardless of whether 8Foundation is an offshoot of Phobos or RansomHouse continues to be to be found.”

8Foundation is portion of a wave of ransomware rookies getting into the market place such as CryptNet, Xollam, and Mallox, even as identified family members like BlackCat, LockBit, and Trigona have witnessed continuous updates to their features and attack chains to broaden their horizons outside of Windows to infect Linux and macOS units.
One instance highlighted by Cyble entails the use of BATLOADER to deploy Mallox, suggesting that the danger actors are actively refining their tactics to “enrich evasiveness and preserve their malicious routines.”
“Groups undertake other groups’ code, and affiliate marketers — which can be viewed as cybercrime groups in their have right — switch between diverse styles of malware,” Kaspersky explained in an evaluation last 7 days. “Teams operate on updates to their malware, including attributes and offering guidance for several, previously unsupported, platforms, a development that existed for some time now.”
Identified this posting appealing? Follow us on Twitter and LinkedIn to go through extra unique information we put up.
Some components of this write-up are sourced from:
thehackernews.com

 Critical SQL Injection Flaws Expose Gentoo Soko to Remote Code Execution
Critical SQL Injection Flaws Expose Gentoo Soko to Remote Code Execution