The danger actors related with the 8220 Gang have been noticed exploiting a large-severity flaw in Oracle WebLogic Server to propagate their malware.
The security shortcoming is CVE-2020-14883 (CVSS rating: 7.2), a distant code execution bug that could be exploited by authenticated attackers to acquire more than prone servers.
“This vulnerability lets distant authenticated attackers to execute code making use of a gadget chain and is generally chained with CVE-2020-14882 (an authentication bypass vulnerability also influencing Oracle Weblogic Server) or the use of leaked, stolen, or weak credentials,” Imperva stated in a report published very last week.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The 8220 Gang has a historical past of leveraging recognised security flaws to distribute cryptojacking malware. Before this May possibly, the group was noticed making use of a different shortcoming in Oracle WebLogic servers (CVE-2017-3506, CVSS rating: 7.4) to rope the products into a crypto mining botnet.
Latest attack chains documented by Imperva entail the exploitation of CVE-2020-14883 to specially craft XML documents and ultimately run code dependable for deploying stealer and coin mining malware this sort of as Agent Tesla, rhajk, and nasqa.
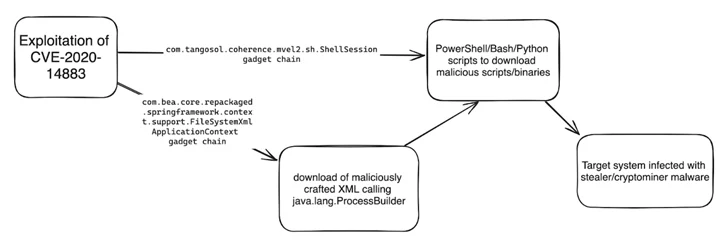
“The team seems to be opportunistic when selecting their targets, with no clear craze in country or industry,” Imperva security researcher Daniel Johnston said.
Targets of the campaign include things like health care, telecommunications, and monetary services sectors in the U.S., South Africa, Spain, Columbia, and Mexico.
“The group relies on basic, publicly accessible exploits to target nicely-recognised vulnerabilities and exploit uncomplicated targets to achieve their goals,” Johnston extra. “Even though thought of unsophisticated, they are continually evolving their techniques and tactics to evade detection.”
Uncovered this posting fascinating? Abide by us on Twitter and LinkedIn to read through more exclusive information we article.
Some parts of this post are sourced from:
thehackernews.com


 Double-Extortion Play Ransomware Strikes 300 Organizations Worldwide
Double-Extortion Play Ransomware Strikes 300 Organizations Worldwide