The malware loader acknowledged as PikaBot is staying distributed as part of a malvertising campaign focusing on people seeking for authentic computer software like AnyDesk.
“PikaBot was beforehand only distributed by using malspam strategies equally to QakBot and emerged as 1 of the most well-liked payloads for a risk actor acknowledged as TA577,” Malwarebytes’ Jérôme Segura explained.
The malware family, which initially appeared in early 2023, is composed of a loader and a main module that will allow it to work as a backdoor as very well as a distributor for other payloads.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This allows the risk actors to get unauthorized remote accessibility to compromised methods and transmit instructions from a command-and-management (C2) server, ranging from arbitrary shellcode, DLLs, or executable information, to other malicious applications such as Cobalt Strike.
Forthcoming WEBINAR Conquer AI-Powered Threats with Zero Have confidence in – Webinar for Security Industry experts
Standard security actions will not lower it in today’s environment. It’s time for Zero Trust Security. Safe your facts like never in advance of.
Join Now
A person of the risk actors leveraging PikaBot in its attacks is TA577, a prolific cybercrime danger actor that has, in the previous, sent QakBot, IcedID, SystemBC, SmokeLoader, Ursnif, and Cobalt Strike.
Last month, it emerged that PikaBot, together with DarkGate, is staying propagated by using malspam campaigns mirror that of QakBot. “Pikabot infection led to Cobalt Strike on 207.246.99[.]159:443 applying masterunis[.]net as its domain,” Palo Alto Networks Unit 42 disclosed not long ago.
The newest first infection vector is a malicious Google advertisement for AnyDesk that, when clicked by a sufferer from the lookup effects web site, redirects to a faux internet site named anadesky.ovmv[.]net that factors to a malicious MSI installer hosted on Dropbox.
It is really well worth pointing out that the redirection to the bogus web site only happens right after fingerprinting the request, and only if it really is not originating from a digital device.
“The risk actors are bypassing Google’s security checks with a tracking URL via a authentic internet marketing system to redirect to their personalized domain behind Cloudflare,” Segura explained. “At this stage, only thoroughly clean IP addresses are forwarded to the subsequent action.”
Curiously, a 2nd round of fingerprinting usually takes position when the victim clicks on the download button on the web site, probably in an included try to be certain that it is really not available in a virtualized setting.
Malwarebytes stated the attacks are reminiscent of earlier determined malvertising chains utilized to disseminate a further loader malware recognized as FakeBat (aka EugenLoader).
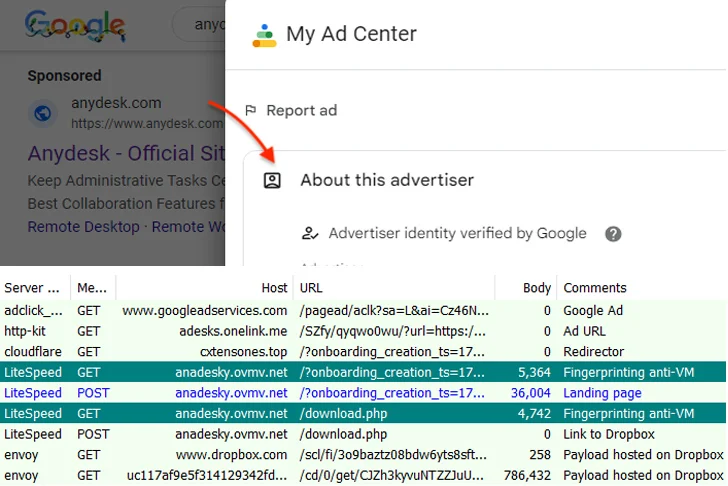
“This is significantly attention-grabbing for the reason that it factors toward a typical system applied by various menace actors,” Segura said. “Perhaps, this is anything akin to ‘malvertising-as-a-service’ wherever Google advertisements and decoy web pages are furnished to malware distributors.”
This disclosure comes as the cybersecurity company reported it detected a spike in malicious advertisements through Google searches for preferred computer software like Zoom, Sophisticated IP Scanner, and WinSCP to supply a previously in no way-in advance of-seen loader known as HiroshimaNukes as effectively as FakeBat.
“It makes use of several tactics to bypass detection from DLL side-loading to really substantial payloads,” Segura stated. “Its goal is to drop more malware, typically a stealer adopted by knowledge exfiltration.”

The increase in malvertising is indicative of how browser-based attacks act as channels for infiltrating goal networks. This also contains a new Google Chrome extension framework codenamed ParaSiteSnatcher, which makes it possible for threat actors to “check, manipulate, and exfiltrate very delicate info from a number of sources.”
Particularly intended to compromise consumers in Latin America, the rogue extension is noteworthy for its use of the Chrome Browser API to intercept and exfiltrate all Put up requests containing delicate account and money info. It is downloaded as a result of a VBScript downloader hosted on Dropbox and Google Cloud and set up on to an contaminated procedure.
“After installed, the extension manifests with the support of substantial permissions enabled by the Chrome extension, letting it to manipulate web periods, web requests, and observe user interactions throughout a number of tabs utilizing the Chrome tabs API,” Craze Micro mentioned very last thirty day period.
“The malware involves several parts that facilitate its procedure, content material scripts that permit malicious code injection into web pages, keep an eye on Chrome tabs, and intercept user input and web browser interaction.”
Found this posting appealing? Abide by us on Twitter and LinkedIn to read through far more special written content we submit.
Some components of this short article are sourced from:
thehackernews.com


 8220 Gang Exploiting Oracle WebLogic Server Vulnerability to Spread Malware
8220 Gang Exploiting Oracle WebLogic Server Vulnerability to Spread Malware