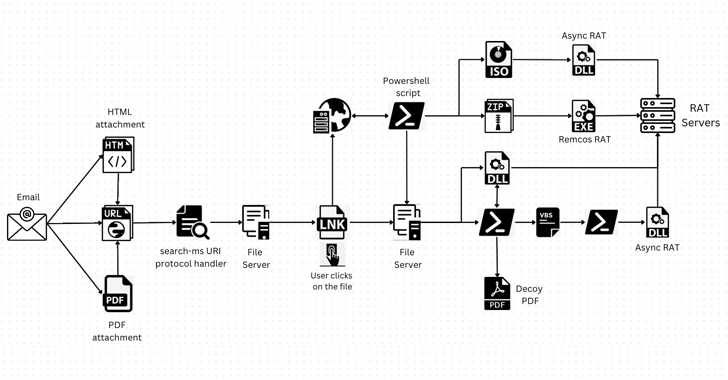
A legitimate Windows research aspect could be exploited by malicious actors to download arbitrary payloads from remote servers and compromise specific units with remote accessibility trojans such as AsyncRAT and Remcos RAT.
The novel attack system, for each Trellix, usually takes gain of the “look for-ms:” URI protocol handler, which presents the capacity for applications and HTML inbound links to launch personalized regional queries on a device, and the “search:” application protocol, a system for calling the desktop search software on Windows.
“Attackers are directing consumers to internet websites that exploit the ‘search-ms’ performance making use of JavaScript hosted on the webpage,” security scientists Mathanraj Thangaraju and Sijo Jacob claimed in a Thursday produce-up. “This system has even been prolonged to HTML attachments, expanding the attack area.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
In these types of attacks, risk actors have been noticed generating misleading emails that embed hyperlinks or HTML attachments made up of a URL that redirects people to compromised sites. This triggers the execution of JavaScript that would make use of the URI protocol handlers to perform queries on an attacker-managed server.
It’s truly worth noting that clicking on the hyperlink also generates a warning “Open up Windows Explorer?,” approving which “the look for benefits of remotely hosted destructive shortcut files are shown in Windows Explorer disguised as PDFs or other dependable icons, just like community research benefits,” the researchers defined.
“This good system conceals the fact that the person is remaining furnished with remote data files and provides the person the illusion of have faith in. As a result, the person is additional probably to open the file, assuming it is from their personal system, and unknowingly execute destructive code.”
Should really a sufferer click on a single of the shortcut information, it sales opportunities to the execution of a rogue dynamic-backlink library (DLL) making use of the regsvr32.exe utility.
In an substitute variant of the campaign, the shortcut data files are utilized to operate PowerShell scripts, which, in switch, download supplemental payloads in the track record, though displaying a decoy PDF document to deceive victims.
Regardless of the strategy utilized, the infections lead to the set up of AsyncRAT and Remcos RAT that can be applied by the menace actors to remotely commandeer the hosts, steal sensitive data, and even offer the accessibility to other attackers.
Approaching WEBINARShield Against Insider Threats: Learn SaaS Security Posture Management
Nervous about insider threats? We’ve bought you coated! Be part of this webinar to check out practical methods and the tricks of proactive security with SaaS Security Posture Administration.
Be part of These days
With Microsoft steadily taking techniques to clamp down on several initial obtain vectors, it really is envisioned that adversaries could latch on to the URI protocol handler approach to evade common security defenses and distribute malware.
“It is crucial to chorus from clicking on suspicious URLs or downloading files from unknown resources, as these actions can expose methods to destructive payloads shipped by the ‘search”https://thehackernews.com/”lookup-ms’ URI protocol handler,” the scientists mentioned.
Found this write-up attention-grabbing? Stick to us on Twitter and LinkedIn to read through a lot more exclusive articles we put up.
Some elements of this short article are sourced from:
thehackernews.com

 BlueBravo Deploys GraphicalProton Backdoor Against European Diplomatic Entities
BlueBravo Deploys GraphicalProton Backdoor Against European Diplomatic Entities