Menace actors guiding the Akira ransomware team have extorted approximately $42 million in illicit proceeds after breaching the networks of much more than 250 victims as of January 1, 2024.
“Because March 2023, Akira ransomware has impacted a vast selection of enterprises and critical infrastructure entities in North The usa, Europe, and Australia,” cybersecurity businesses from the Netherlands and the U.S., along with Europol’s European Cybercrime Centre (EC3), mentioned in a joint warn.
“In April 2023, pursuing an preliminary target on Windows programs, Akira threat actors deployed a Linux variant focusing on VMware ESXi virtual machines.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The double-extortion team has been observed employing a C++ variant of the locker in the early stages, before shifting to a Rust-centered code as of August 2023. It truly is truly worth noting that the e-criminal offense actor is completely various from the Akira ransomware spouse and children that was lively in 2017.
First access to focus on networks is facilitated by suggests of exploiting regarded flaws in Cisco appliances (e.g., CVE-2020-3259 and CVE-2023-20269).
Alternate vectors involve the use of Remote Desktop Protocol (RDP), spear-phishing, legitimate qualifications, and virtual non-public network (VPN) products and services missing in multi-factor authentication (MFA) protections.

Akira actors are also known to leverage various methods to set up persistence by generating a new domain account on the compromised procedure, as effectively as evade detection by abusing the Zemana AntiMalware driver to terminate antivirus-similar processes by way of what’s known as a Carry Your Very own Vulnerable Driver (BYOVD) attack.
To aid in privilege escalation, the adversary relies on credential scraping equipment like Mimikatz and LaZagne, when Windows RDP is utilized to transfer laterally within just the victim’s network. Facts exfiltration is achieved as a result of FileZilla, WinRAR, WinSCP, and RClone.
“Akira ransomware encrypts specific units employing a hybrid encryption algorithm that brings together Chacha20 and RSA,” Pattern Micro mentioned in an assessment of the ransomware revealed in October 2023.
“Additionally, the Akira ransomware binary, like most contemporary ransomware binaries, has a element that enables it to inhibit procedure restoration by deleting shadow copies from the affected system.”
Blockchain and supply code info implies that Akira ransomware team is possible affiliated with the now-defunct Conti ransomware gang. A decryptor for Akira was unveiled by Avast last July, but it is really really probably the shortcomings have given that been plugged.
Akira’s mutation to target Linux company environments also follows comparable moves by other proven ransomware people this kind of as LockBit, Cl0p, Royal, Monti, and RTM Locker.

LockBit’s Struggles to Occur Again
The disclosure will come as Development Micro disclosed that the sweeping regulation enforcement takedown of the prolific LockBit gang previously this February has had a sizeable operational and reputational effects on the group’s capacity to bounce back again, prompting it to post old and faux victims on its new information leak site.
“LockBit was one particular of the most prolific and commonly used RaaS strains in operation, with likely hundreds of affiliates, including many linked with other distinguished strains,” Chainalysis pointed out in February.
The blockchain analytics business mentioned it uncovered cryptocurrency trails connecting a LockBit administrator to a journalist primarily based in Sevastopol recognised as Colonel Cassad, who has a history of soliciting donations for Russian militia team operations in the sanctioned jurisdictions of Donetsk and Luhansk following the onset of the Russo-Ukrainian war in 2022.
It’s well worth pointing out that Cisco Talos, in January 2022, linked Colonel Cassad (aka Boris Rozhin) to an anti-Ukraine disinformation campaign orchestrated by the Russian point out-sponsored group known as APT28.
“Pursuing the procedure, LockBitSupp [the alleged leader of LockBit] seems to be trying to inflate the obvious sufferer count even though also focusing on publishing victims from nations whose law enforcement organizations participated in the disruption,” Pattern Micro mentioned in a latest deep dive.
“This is maybe an try to enhance the narrative that it would appear back stronger and focus on those liable for its disruption.”
In an interview with Recorded Long run News past thirty day period, LockBitSupp acknowledged the small-expression drop in gains, but promised to increase their security measures and “function as very long as my heart beats.”

“Popularity and have confidence in are crucial to attracting affiliates, and when these are dropped, it really is more durable to get individuals to return. Operation Cronos succeeded in hanging against 1 component of its enterprise that was most significant: its manufacturer,” Development Micro mentioned.
Agenda Returns with an Up-to-date Rust Model
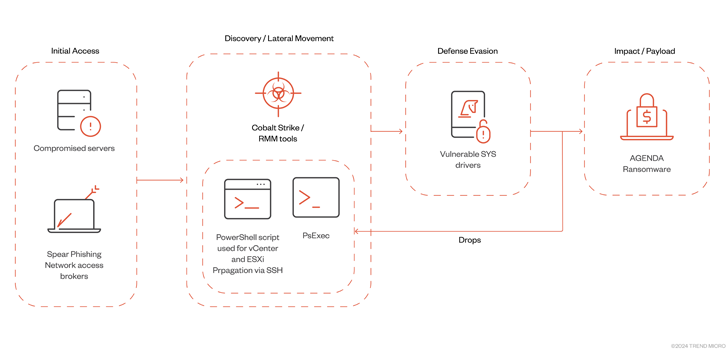
The progress also follows the Agenda ransomware group’s (aka Qilin and Drinking water Galura) use of an current Rust variant to infect VMWare vCenter and ESXi servers by means of Remote Monitoring and Management (RMM) tools and Cobalt Strike.
“The Agenda ransomware’s capacity to spread to digital equipment infrastructure reveals that its operators are also expanding to new targets and devices,” the cybersecurity organization reported.
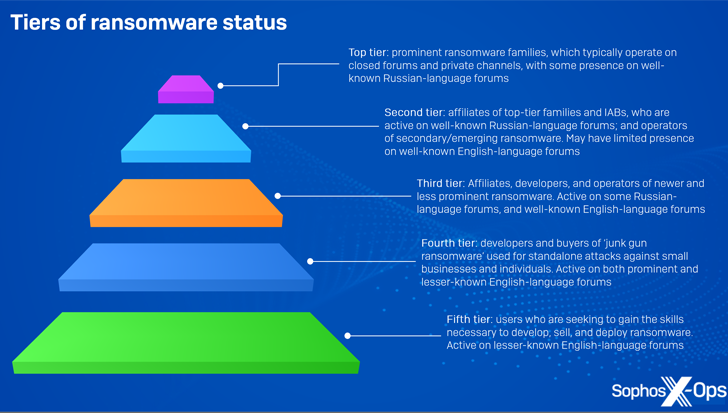
Even as a refreshing crop of ransomware actors proceeds to energize the risk landscape, it really is also turning out to be clearer that “crude, low-priced ransomware” bought on the cybercrime underground is currently being place to use in genuine-environment attacks, permitting reduced-tier specific menace actors to make substantial earnings without having possessing to be a component of a effectively-arranged team.
Apparently, a the greater part of these varieties are out there for a one, one-off price commencing from as reduced as $20 for a solitary establish, whilst a few other people such as HardShield and RansomTuga are available at no added price.
“Away from the advanced infrastructure of contemporary ransomware, junk-gun ransomware permits criminals to get in on the motion cheaply, effortlessly, and independently,” Sophos said, describing it as a “reasonably new phenomenon” that further lowers the cost of entry.
“They can goal little corporations and people today, who are unlikely to have the assets to defend by themselves or reply correctly to incidents, without having providing any one else a slash.”
Located this post fascinating? Comply with us on Twitter and LinkedIn to go through additional exceptional articles we put up.
Some elements of this write-up are sourced from:
thehackernews.com


 Hackers Target Middle East Governments with Evasive “CR4T” Backdoor
Hackers Target Middle East Governments with Evasive “CR4T” Backdoor