A danger actor named H2o Curupira has been noticed actively distributing the PikaBot loader malware as component of spam strategies in 2023.
“PikaBot’s operators ran phishing strategies, concentrating on victims via its two elements — a loader and a main module — which enabled unauthorized distant obtain and authorized the execution of arbitrary instructions via an proven link with their command-and-manage (C&C) server,” Development Micro mentioned in a report published currently.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The action began in the 1st quarter of 2023 that lasted till the close of June, prior to ramping up all over again in September. It also overlaps with prior campaigns that have utilised related methods to provide QakBot, precisely people orchestrated by cybercrime groups recognised as TA571 and TA577.
It is believed that the raise in the variety of phishing strategies related to PikaBot is the outcome of QakBot’s takedown in August, with DarkGate rising as an additional replacement.
PikaBot is generally a loader, which means it truly is made to start a further payload, including Cobalt Strike, a reputable article-exploitation toolkit that usually functions as a precursor for ransomware deployment.
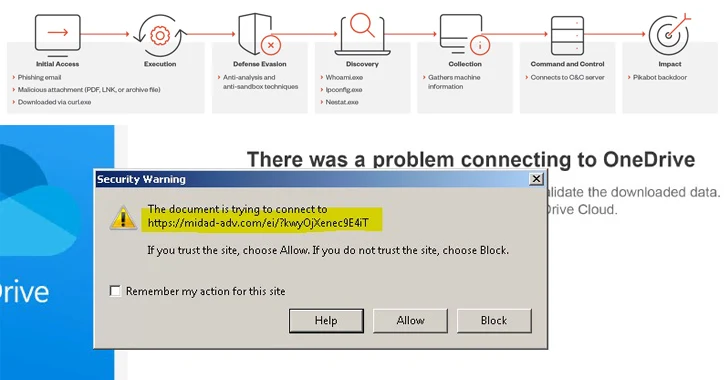
The attack chains leverage a method called email thread hijacking, employing existing email threads to trick recipients into opening destructive one-way links or attachments, properly activating the malware execution sequence.

The ZIP archive attachments, which either comprise JavaScript or IMG files, are employed as a launchpad for PikaBot. The malware, for its portion, checks the system’s language and halts execution must it be both Russian or Ukrainian.
In the future step, it collects details about the victim’s procedure and forwards them to a C&C server in JSON structure. Drinking water Curupira’s campaigns are for the intent of dropping Cobalt Strike, which subsequently guide to the deployment of Black Basta ransomware.
“The threat actor also executed numerous DarkGate spam strategies and a small number of IcedID strategies for the duration of the early months of the third quarter of 2023, but has given that pivoted exclusively to PikaBot,” Trend Micro explained.
Located this article fascinating? Abide by us on Twitter and LinkedIn to read through extra special material we write-up.
Some elements of this article are sourced from:
thehackernews.com

 Turkish Hackers Exploiting Poorly Secured MS SQL Servers Across the Globe
Turkish Hackers Exploiting Poorly Secured MS SQL Servers Across the Globe