Cybersecurity scientists have identified a previously undocumented malware concentrating on Android equipment that employs compromised WordPress internet sites as relays for its real command-and-control (C2) servers for detection evasion.
The malware, codenamed Wpeeper, is an ELF binary that leverages the HTTPS protocol to safe its C2 communications.
“Wpeeper is a standard backdoor Trojan for Android units, supporting capabilities these types of as accumulating sensitive gadget facts, taking care of documents and directories, uploading and downloading, and executing commands,” researchers from the QiAnXin XLab staff claimed.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The ELF binary is embedded inside of a repackaged software that purports to be the UPtodown Application Store app for Android (package deal name “com.uptodown”), with the APK file performing as a supply vehicle for the backdoor in a method that evades detection.

The Chinese cybersecurity organization explained it learned the malware soon after it detected a Wpeeper artifact with zero detection on the VirusTotal platform on April 18, 2024. The marketing campaign is stated to have arrive to an abrupt end 4 times afterwards.
The use of the Uptodown App Retail store application for the campaign suggests an try to move off a respectable third-party application market and trick unsuspecting end users into putting in it. According to stats on Android-apk.org, the trojanized version of the app (5.92) has been downloaded 2,609 periods to day.

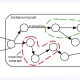
Wpeeper depends on a multi-tier C2 architecture that works by using infected WordPress websites as an middleman to obscure its genuine C2 servers. As many as 45 C2 servers have been identified as portion of the infrastructure, 9 of which are challenging-coded into the samples and are utilised to update the C2 list on the fly.
“These [hard-coded servers] are not C2s but C2 redirectors — their position is to ahead the bot’s requests to the genuine C2, aimed at shielding the precise C2 from detection,” the researchers explained.

This has also raised the probability that some of the hard-coded servers are immediately beneath their management, because there is a risk of losing access to the botnet ought to WordPress web page administrators get wind of the compromise and just take steps to appropriate it.
The instructions retrieved from the C2 server allow the malware to obtain system and file details, list of installed applications, update the C2 server, down load and execute extra payloads from the C2 server or an arbitrary URL, and self-delete alone.
The actual targets and scale of the campaign are presently mysterious, despite the fact that it can be suspected that the sneaky approach may well have been used to boost the set up numbers and then reveal the malware’s abilities.
To mitigate the risks posed by these kinds of malware, it is constantly suggested to install apps only from trustworthy resources, and scrutinize app testimonials and permissions prior to downloading them.
Observed this write-up interesting? Stick to us on Twitter and LinkedIn to read much more special articles we submit.
Some areas of this short article are sourced from:
thehackernews.com


 Everyone’s an Expert: How to Empower Your Employees for Cybersecurity Success
Everyone’s an Expert: How to Empower Your Employees for Cybersecurity Success